Cybersecurity News in Asia
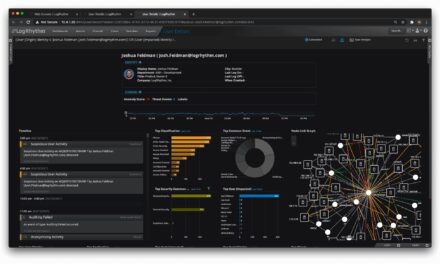
Minimizing false positives in digital payment
By Victor Ng | Oct 15, 2024
In 2024 and beyond, is Cybersecurity Awareness Month obsolet...
By Victor Ng | Oct 8, 2024
Cyber risks vs productivity – AI dichotomy in the workplace...
By Victor Ng | Oct 2, 2024
The tough conversations about cybersecurity
By Victor Ng | Oct 2, 2024
SECURITY NEWS
Were manufacturing-industry employees more prone to phishing attacks in 2023?
Oct 24, 2024
One cybersecurity training firm has examined some third-party threat intelligence reports to highlight manufacturing industry cyber trends
EXPERT OPINIONS
Preventing ransomware with EDR and NDR: a complementary approach
Oct 17, 2024
Neither EDR and NDR are complete solutions in themselves — but when combined, this writer believes a more viable defense is achievable
-

-

-

“Bump in the night”: What’s next?
Sep 26, 2024
TIPS
To use or not to use GenAI for cybersecurity… that is the question
Oct 23, 2024
Given the hallucinations and other unexpected behavior, can GenAI be used safely for cybersecurity? Here are some factors to consider.
-

-

The AI Plus Factor in OT Cyber Defence
Oct 18, 2024
-

The Triple Threat: Cyber, AI, and Quantum
Oct 17, 2024
CLOUD SECURITY
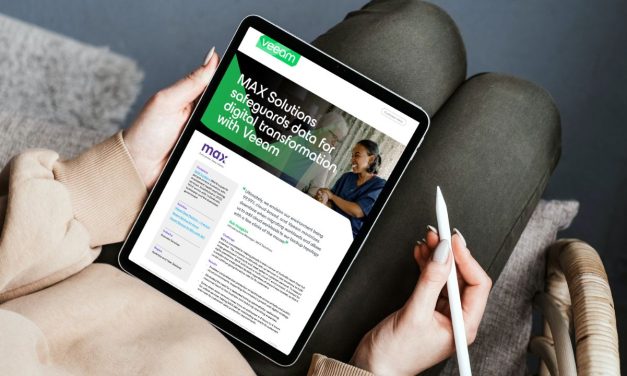
MAX Solutions safeguards data for digital transformation with Veeam
Sep 11, 2024
One of the largest employment providers in Australia needed to protect data while reducing complexity when it decided to migrate from on-prem to multi-cloud.
“Bump in the night”: What’s next?
Sep 26, 2024
Cybersecurity: looking back 2021, looking ahead 2022
Jan 20, 2022
INFOGRAPHICS
Verizon 2024 Mobile Security Index
Aug 14, 2024
600 mobile and security professionals have spoken: Mobile device risks are escalating.
-

Acronis Cyberthreats Report H1 2024
Jul 31, 2024
Cyber Intelligence
LatestW3LL-oiled machine: report uncovers covert BEC phishing empire targeting Microsoft 365
By CybersecAsia editors and webmaster webmaster | Sep 7, 2023
A new threat report “W3LL DONE: HIDDEN PHISHING ECOSYSTEM DRIVING BEC ATTACKS” has detailed the operations of W3LL, a threat actor behind a phishing empire that has remained largely unknown until now.
-

-

-

Making cyber-resilience part of your organization’s balance sheet
By Victor Ng | Apr 26, 2022
Cyber Warfare
LatestRansomware still the #1 cyber threat: report
By CybersecAsia editors | Jan 30, 2023
With stolen credentials and Ransomware-as-a-Service kits being sold cheaper than ever on the Dark Web, expect more cybercrime this year!
-

-

Ukraine-Russia conflict: war also occurs in cyberspace
By CybersecAsia editors and webmaster webmaster | Feb 28, 2022
-

MOST READ
WhatsApp group chat vulnerability hack thwarted
Researchers had discovered in August a group-chat flaw where a malicious message could crash WhatsApp group users’ devices. A...
Nine DevSecOps secret scanning tools to keep the bad guys at bay
With the secrets of over 2m corporations already leaked, it is time to mandate action to plug the preventable gaps
Join 60,000 Fellow IT & Business Professionals in APAC Region
Get the latest news, trends and expert opinions straight to your inbox, and craft an effective cybersecurity strategy.
Voters-draw/RCA-Sponsors
CybersecAsia Voting Placement
Gamification listing or Participate Now
|
PARTICIPATE NOW |
|
|
Vote Now -Placement(Google Ads)
Top-Sidebar-banner
Whitepapers

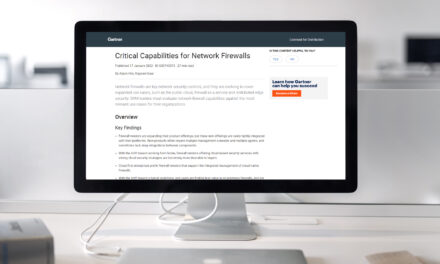
2024 Gartner® Magic Quadrant™ for SD-WAN
Gartner® has positioned Fortinet highest for Ability to Execute for the fourth year in a …Download Whitepaper
Digital Acceleration Requires Converged Security and Networking
Discover how converging security and networking can enhance your efficiency and safeguard your hybrid workforce. …Download Whitepaper
5 Key IoT Capabilities to Look for in a Networking Solution
With IoT devices becoming an essential part of modern networks, securing them is more important …Download Whitepaper
Bot or Not? Sophisticated, Malicious Bots Can Bypass Security by Mimicking Human Behavior
As bots grow increasingly advanced, they can now mimic human behavior to bypass outdated security …Download Whitepaper
Middle-sidebar-banner
Case Studies

Unlock Your Guide to Securing Business Critical Secrets
Is your organization effectively managing access to sensitive secrets like credentials, API keys, and certificates …Read more
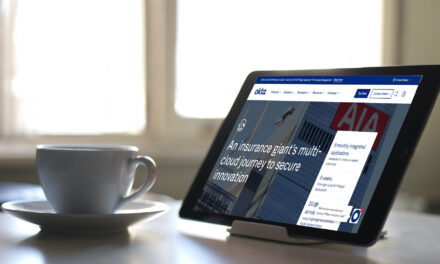
RBL Finserve boosts control of growing number of identities in its multi-cloud environment
By adopting a third-party identity security platform, the Indian financial institution expects to leverage zero …Read more
MAX Solutions safeguards data for digital transformation with Veeam
One of the largest employment providers in Australia needed to protect data while reducing complexity …Read more
Adding secure automatic multi-factor authentication boosts customer experience: Tiger Brokers
Can tightening identity security degrade customer experience? In this case study, an online trading platform …Read more