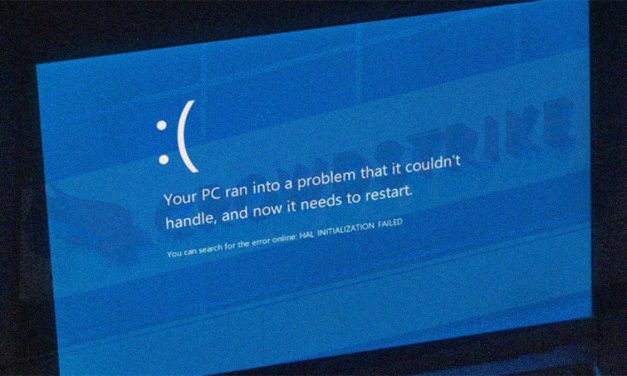
Recovering from the BSOD outage of 19 July amid ch...
By CybersecAsia editors | Jul 23, 2024
Cybercriminals have their eyes on compromising sof...
By CybersecAsia editors | Jul 23, 2024
Did you know that slack DEI/ESG corporate vigilanc...
By CybersecAsia editors | Jul 19, 2024
Cybercriminals are waiting to prey on Olympics fans as a sport
By Stanley Hsu, Regional Vice President (Asia), Mimecast | Jul 26, 2024
Here are some GOLD Olympic cyber safety tips to share around, to keep sports fans safe online…
Read MoreRecovering from the BSOD outage of 19 July amid chaos, phishing scams
By CybersecAsia editors | Jul 23, 2024
Getting affected Windows machines up and running will be an arduous undertaking in some firms, but the following precautions still apply
Read MoreCybercriminals have their eyes on compromising software patches now
By CybersecAsia editors | Jul 23, 2024
In the wake of the current global outages caused by a faulty software update, cybercriminals will be targeting software updates/patches evermore
Read MoreEmbracing AI to secure APAC’s digital future
By Pierluigi Cau, Senior Director, Field Services APAC, GitHub | Jul 22, 2024
In the face of rising cyberthreats and a shortage of cybersecurity experts, organizations must quickly embrace AI to ensure the long-term security of their applications and meet the evolving challenges...
Read MorePreparing to meet the AI-powered cyberthreats during the Olympics
By Mohan Veloo, CTO, Asia-Pacific, China and Japan, F5 | Jul 19, 2024
The 2024 Olympic Games are just around the corner! And so are bad actors seeking to leverage this global 2.5-week festive sporting event for financial or political gains…
Read MoreDid you know that slack DEI/ESG corporate vigilance is now a major cyber risk?
By CybersecAsia editors | Jul 19, 2024
So are ‘irresponsible use of AI’ and ‘ideological cyber warfare’. Here are a few sets of tips to keep organizations safe…
Read MoreUnderstanding the phishing opportunities of large yearly sales events
By CybersecAsia editors | Jul 16, 2024
From double-date (11/11 or 12/12) e-commerce sales campaigns to exclusive members-only global online sales festivals, phishing- and cyber- risks abound
Read MoreLessons from Indonesia’s worst ransomware incident in recent history
By L L Seow | Jul 12, 2024
Here are the tips and strategies that governments around the world can take away from the cyberattack and the recovery lags
Read MoreDon’t get caught offside with illegal streaming
By Darren Guccione, CEO and Co-Founder, Keeper Security | Jul 4, 2024
Cyber-attacks leveraging soccer fans' desire for live streaming of of the European Championships can lead to losing the game - and we're not just talking about football here.
Read MoreStaying safe and private with Android devices
By L L Seow | Jun 27, 2024
With more phone manufacturers extending the Android update support period to four versions, more users will need the following tips…
Read More
Voters-draw/RCA-Sponsors
CybersecAsia Voting Placement
Gamification listing or Participate Now
|
PARTICIPATE NOW |
|
|
Vote Now -Placement(Google Ads)
Top-Sidebar-banner
Whitepapers

2024 Voice of the CISO
The "2024 Voice of the CISO" report by Proofpoint offers insights from a survey of …Download Whitepaper
Securing Industry 4.0
The world is advancing to Industry 4.0 in full swing, and this is a key …Download Whitepaper
To the Power of Proofpoint
Microsoft 365 is indispensable for modern businesses, facilitating remote work, global collaboration, and cloud operations.Download Whitepaper
The 2024 Data Loss Landscape
The 2024 Data Loss Landscape Report by Proofpoint reveals that 85% of organizations have encountered …Download Whitepaper
Middle-sidebar-banner
Case Studies

Eliminating “vault sprawl” helps DCB Bank (India) in more ways than one
Centrally rotating and management credentials in its developer workflows using an identity security platform has …Read more
Nan Fung Group rolls out secure NFC building access app for Apple Wallet users
Tenants of the AIRSIDE office tower in Hong Kong are the first to experience the …Read more
What data-driven organizations need today and in the future
Our data-driven business world needs purpose-built data protection solutions that combine centralized management with a …Read more
How medical devices manufacturer Tuttnauer protects patient and personal-data safety
In running a cloud-based portal to link its smart medical equipment, the firm has also …Read more