Will your organization’s defenses be breached due to your su...
By L L Seow | May 29, 2025
How the UAE proactively protects its digital economy
By Victor Ng | May 19, 2025
Navigating blockchain adoption amid rising security challeng...
By Victor Ng | May 14, 2025
Backups are not enough for cyber resilience
By CybersecAsia editors | May 5, 2025
MSPs the first line of defense for APAC SMEs
By Victor Ng | Apr 15, 2025
SECURITY NEWS
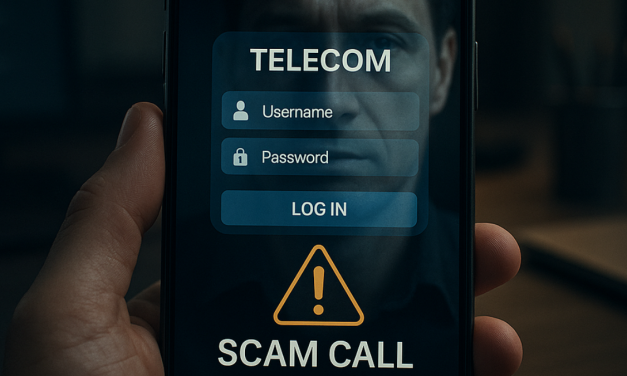
Will robocall fraud start to decline in 2026 with stronger regulations?
Jun 17, 2025
According to one marketing research firm’s forecast, the STIR/SHAKEN framework and AI-driven solutions will reverse the rise of robocall fraud soon.
EXPERT OPINIONS
Open-source AI democratization: Can cyber defenses rise to the double-edged challenges?
Apr 16, 2025
When accessibility barriers fall, vulnerabilities emerge. Open-source AI models can be exploited by more people: a double-edged sword in the making
TIPS
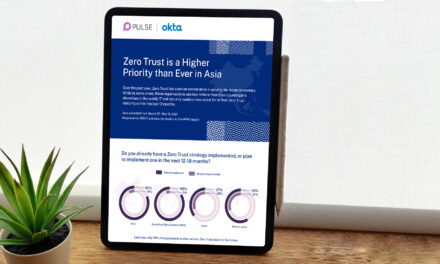
Closing the gap in Zero Trust implementation: What you need to consider
Jun 18, 2025
Organizations investing in Zero Trust may struggle to unify controls, risking exposure to AI-driven attacks, supply chain breaches, and compliance pressures.
-

-

How vigilant are you to sneaky phishing tactics?
Jun 13, 2025
-

Know the four most common password mistakes
May 27, 2025
















CLOUD SECURITY
How will Gen AI introduce benefits and risks in cloud security in 2025?
Feb 17, 2025
One set of predictions by a market research and tech advisory firm has enumerated three potential benefits and two broad risks
INFOGRAPHICS
7 themes shaping security and identity in 2025
Mar 13, 2025
security and identity, 2025 State of Security and Identity Report, platformization, biometrics, AI, mobile credentials, unified security management,
-

Phishing trends in Q3 2024
Dec 11, 2024
Cyber Intelligence
LatestW3LL-oiled machine: report uncovers covert BEC phishing empire targeting Microsoft 365
By CybersecAsia editors and webmaster webmaster | Sep 7, 2023
A new threat report “W3LL DONE: HIDDEN PHISHING ECOSYSTEM DRIVING BEC ATTACKS” has detailed the operations of W3LL, a threat actor behind a phishing empire that has remained largely unknown until now.
-

-

-

Making cyber-resilience part of your organization’s balance sheet
By Victor Ng | Apr 26, 2022
Cyber Warfare
LatestIs the world ready to be united against intensifying 2025 cyber warfare?
By Nadir Izrael, CTO, Armis | Nov 19, 2024
From AI-emboldened organized cybercriminals to state-sponsored quantum threats, the cyber landscape could run out of control unless we act now
-

-

Ransomware still the #1 cyber threat: report
By CybersecAsia editors | Jan 30, 2023
-

MOST READ
WhatsApp group chat vulnerability hack thwarted
Researchers had discovered in August a group-chat flaw where a malicious message could crash WhatsApp group users’ devices. A...
Nine DevSecOps secret scanning tools to keep the bad guys at bay
With the secrets of over 2m corporations already leaked, it is time to mandate action to plug the preventable gaps
sponsors-RCA
CybersecAsia Readers’ Choice Awards Ceremony Teaser


Fireside Chat



WHAT’S NEXT
WHAT'S NEXT |
|---|
Webinars: |
|
⚫ June 9, 2021: Prospect Webinar |
|
⚫June 9-10, 2021: Partner Webinars – BlackBerry Gateway, Optics 3.0 |
Newsletters: |
|
⚫June 2, 2021: Partner Newsletter – Gateway |
|
⚫June 8, 2021Customer Newsletter |