Newbies and detractors of e-commerce forced to go online, accounted for much of the low cybersecurity awareness and cascading vulnerability levels.
Last year was marked by massive surges, as well as the emergence, of new cyberthreats.
This does not necessarily mean that the total number of identified attacks grew in 2020, yet their redistribution is clear.
Cybersecurity researchers have discovered a 242% growth of brute force attacks on remote desktop protocols (RDP) compared to 2019, along with 1.7 million unique malicious files disguised as apps appeared. These findings reflect how attackers have been putting their efforts into targeting users that work from home.
One of the most popular application-level protocols for accessing Windows workstations or servers is Microsoft’s proprietary protocol RDP. The number of incorrectly configured RDP machines grew in number during the first wave of lockdowns across the globe, and so did the number of cyberattacks on them. These attacks were usually attempting to brute-force (systematically trying to find the correct option) a username and password. A successful attempt resulted in cybercriminals gaining remote access to the target computer in the network.
Two popular 2020 breaches
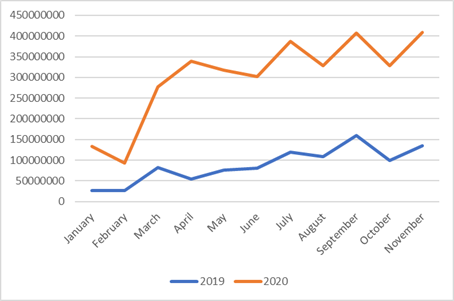
According to Kaspersky researchers, since the beginning of March 2020, the number of Bruteforce.Generic.RDP detections had skyrocketed, resulting in the total number detected in the first eleven months of 2020 growing by 3.4 times compared to the number of the same type of attacks in 2019.
Overall, 3.3 billion attacks on RDP were detected between January and November 2020. The 2019 figure for the same 11-month period was 969 million.
Aside from attacks on RDP, cybercriminals were quick to figure out that many workers replaced offline communication with online tools and so decided to abuse this demand too. Kaspersky detected 1.66 million unique malicious files that were disguised as popular messaging and online conferencing applications, typically used for work.
Once installed, these files would primarily load Adware. Another group of files disguised as corporate apps were downloaders: applications that may not be malicious, but can download other apps such as trojans or furtive remote access tools.
A hard lesson from newbies
According to Dmitry Galov, one of the firm’s security researchers: “This year taught us a lot. Economies did not freeze and we still get to have our coffee, albeit, via delivery services. Yet now we know that there is still a lot to learn about the responsible use of technology, with data sharing at the heart of it.”
One of the biggest challenges of 2020, according to Galov, was the onboarding of newbies to the digital world forced to go digital. Many were people who in principle avoided being so digitally exposed in first place! “They did not necessarily disregard the need for cybersecurity: they had simply chosen not to use digital services before and were less educated about what can happen online. This group of people turned out to be one of the most vulnerable during the pandemic. Their level of awareness of online dangers was very low. It seems like we have been given a big challenge worldwide and I hope that helped increase the level of cybersecurity awareness among ordinary users,” Galov added.
General recommendations
For one reason or other, many of the newbies did go unscathed and may continue to add to the low awareness threshold that will put many others at risk this year. While employers fight on to boost digital transformation and keep pace with the cybersecurity aspects, non-IT savvy personnel working from home even occasionally, can do their part to reduce exposure to cyberthreats:
- Set up strong passwords for your router and Wi-Fi network. Ideally it should include a mix of lower-case and upper-case letters, numbers and punctuation.
- If you can, do work and only work on devices provided by your employer. Putting corporate information on your personal devices could lead to potential security and confidentiality issues. Similarly, putting personal data and apps in official office devices is a no-no.
- Do not share your work account details with anybody else, even if it seems a good idea at the time.
- In order to protect personal devices, use a reliable security solution that safeguards your privacy, data and financial assets with a comprehensive set of tools and features, including a VPN, payment protection, PC cleaning, blocking unauthorized access to webcams, file encryption, password storage, parental control and many others.





















