Bored with capitalizing on COVID-19 fears uncertainties and doubts, cybercrooks are zooming in on lax remote-desktop protocol users …
After months of abusing the COVID-19 theme in their campaigns, cybercriminals appear to have returned to their usual tactics in the Q3 2020, with a focus on attacking remote workers using the vulnerable Remote Desktop Protocol (RDP).
Telemetry from cybersecurity firm ESET has showed further growth in attacks targeting RDP which had been escalating throughout H1 this year.
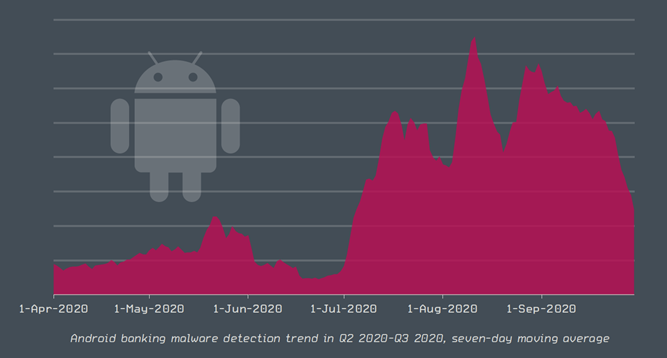
While the number of unique clients targeted rose by more than a third, the total number of attack attempts has surged by 140%. Other key trends observed in Q3 were the revival of the cryptominer Emotet after months of inactivity, as well as Android banking malware surging following the source code release of the notorious mobile banking trojan Cerberus.
Jiří Kropáč, Head of Threat Detection Labs, ESET, commented: “The continued rise in RDP attacks may be a result of the growing number of poorly-secured systems being connected to the internet during the pandemic, or possibly other criminals taking inspiration from ransomware gangs in targeting RDP.”
Other findings by the firm include:
- More Wi‑Fi chips have been determined to be vulnerable to KrØØk-like bugs: the Microsoft Azure Sphere development kit; chips by MediaTek (on the Asus RT-AC52U router) for which patches have since been issued.
- Mac malware (GMERA) bundled with the Kattana cryptocurrency trading application.
- An entirely new Linux malware CDRThief—targeting Linux VoIP soft switches to exfiltrate various private data including call detail records (CDRs) for cyberespionage or for VoIP fraud.
- A triple threat in regard to cryptocurrencies called KryptoCibule in the Czech Republic and Slovakia.
- Details of campaigns leveraging malicious MAXScripts targeting Autodesk 3DS Max.
- The spread of Latin American banking trojans Grandoreiro, Mekotio and Mispadu to Europe, new activity of the state-sponsored TA410 threat group.
- Information on three modules added to the arsenal of the Gamaredon Group: an SFX archive containing BAT and VBS files; a module using both .BAT and VBS scripts that inject malicious macros into existing documents and also replace the Microsoft Word templates “Normal.dotm” and “NormalEmail.dotm” with malicious versions; and finally an SFX archive containing scripts to scan compromised systems (local and mapped drives) for archives and executables with specific filenames, and modify them.

















