Which threats and actors should South-east Asian and Japanese businesses watch for in the remaining part of 2020 and beyond?
What does the threat landscape forSoutheast Asia (SEA) and Japan look like for the rest of the year and maybe beyond?
The two zones present a unique geography of developed and emerging markets where some of the largest enterprises in the world are based, and are a hotbed for fast-growing tech start-ups and youthful digital natives. At the same time, governments in these regions are encouraging digital adoption and driving smart city projects at breakneck levels, due in no small part to the current pandemic situation.
According to the founder and CEO of a firm that predicts cybersecurity scenarios: “All this connectivity translates to wider attack surfaces for threat actors. Additionally, cyber maturity may not be keeping pace with this growth, creating a ripe environment for cyberthreat actors looking to exploit vulnerabilities. We have already seen hacker groups taking advantage of the global health crisis over the last few months to intensify their attacks, causing a spike in cyberthreat activities.”
With that in mind, the firm, CYFIRMA, has released a predictive cyber-threat visibility and intelligence analytics report that offers facts and intelligence information on reported cyber-attack campaigns with detailed information on the top attack methods. One section deep-dives into the top critical incidents in the first half of the year; another focuses on specific threat actors that are targeting organizations in the regions and offers an analytical view into the tools and attack methods, such as phishing, during the current pandemic.
The report was developed by CYFIRMA researchers using its proprietary cloud-based threat discovery and cyber-intelligence platform. The team taps on this to dive into hackers’ trenches to analyze and correlate information and discover the deepest insights from the data.
What the report reveals
The report found that Singapore, among other nations, has become a target for Chinese-sponsored MISSION2025, a threat group that exploits cyber vulnerabilities for espionage purposes and financial gains. Also:
- The Tokyo 2020 Olympics had unleashed a cyberattack frenzy: state-sponsored hackers from China, North Korea and Russia were using COVID-19 as a means to discourage nations from participating at the games, or at the least delay it.
- After the Tokyo 2020 Olympics events were postponed, cybercriminals expanded their horizons to include other short-term targets, including the launch of fake domains by Russian cybercriminals as ‘authorized ticket resellers’ that could potentially be re-deployed for the games in 2021.
- Chinese and North Korean threat actors squarely targeted Japan and South East Asia. Geo-political arguments came to the fore as state sponsored actors like Lazarus Group and Mission2025, amongst others, unleashed disruptive campaigns in this region, especially targeting Japan.
- The pandemic was massively-leveraged as part of threat campaigns. The North Korean Lazarus Group was found to be planning a large-scale phishing campaign targeting more than five million individuals and businesses across six countries and multiple continents, amongst other such campaigns.
Additionally, during the pandemic, the healthcare sector was hit by cyberattacks without much resistance due to a myriad of reasons including outdated technologies in healthcare or employees lacking the proper knowledge to manage sensitive information securely.
Said the firm’s spokesman Kumar Ritesh: “The report offers a landscape view on cyberthreat allowing organizations to better understand the motivation behind threat actors and the methods they adopt.”
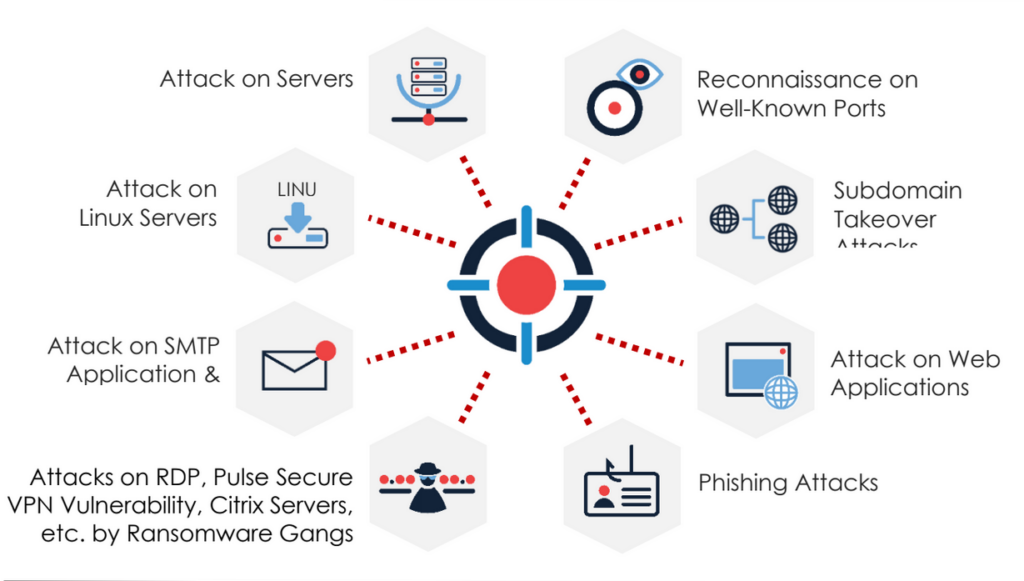
Upcoming trends
More important than what has already transpired, are the predicted activities in the remaining months of the year and maybe the first half of next year. The report’s researchers expect the following trends:
- Geopolitical tensions: The current climate of trade wars and political rivalry is fueling cyberthreats across the world. Targets that cybercriminals will be after include critical information infrastructures, financial services, manufacturing and retail/ecommerce. New entrants may sustain the recent surge in hacking attempts, also inducing the comeback of old malwares. New nations joining the game quite late have suddenly skewed the whole cyber warfare landscape in a different way, coupled with the ‘copy-and-paste’ hackers who take old malware source code and repurpose it to launch attacks.
- Reconnaissance activity: When target systems are located on a secure network, attackers need to be cautious while bypassing the elements of a defence-in-depth architecture. Hence, reconnaissance will become very important for the initial planning.
- Ransomware trends: Ransomware groups are improving their tactics and have become quite desperate. They do not depend on any particular attack vector or attack method but combine different approaches for targeting organizations. Healthcare, government agencies, banks, manufacturing, retail, IT service providers and ecommerce platforms will likely be on their radar for the rest of the year. The planning might have started long before the actual execution of campaign and deployment of the malware. Files may getting published on data leaks sites for groups like Maze as part of their new ‘name and shame’ modus operandi. ‘Ransomware as a Service’ will lure a lot of new-age cybercriminals into hacking as a means for making quick money.
- Phishing and social engineering: Data breaches have been more evident only because of different social engineering attacks, which are expected to continue unabated in the months ahead. Note that phishing emails are usually ripe with intimidating taunts such as “your account will be closed” or “your account will be compromised” etc.
- Brute Force/DDoS Attacks: DDoS & Brute-force activities have increased heavily on year, especially during April to June. Hackers will try to find information on the vulnerabilities that could be leveraged for large-scale DDoS attacks. The trend of using several compromised servers, and malware hosting assets to launch attacks, will continue.
The DDoS attacks of late have been more complex, lasted for longer. Moreover, during the COVID-19 pandemic, RDP brute-force scenarios will become more obvious. - Commodity malware usage: Nation-sponsored hacking groups are still using commodity malware for their campaigns. The Lazarus Group and Stone Panda have often utilized these malware variants for the initial intrusion stage in many of their campaigns. The observed techniques are a persistence mechanism via service creation, process injection into svchost, antivirus evasion, usage of unsigned fake applications, dynamic DNS for command and control communication, etc.

















