The chronicles of the well-known REvil attacks have actually put cybersecurity weaknesses in the spotlight for the world to learn from…
By compromise a leading IT services provider, the infamous REvil ransomware gang has upped the ante significantly with a wide ranging operation that is suspected to have impacted thousands of small-to-midsize businesses.
Reports indicate that REvil exploited the Kaseya VSA remote management service to propagate the ransomware to multiple targets by way of Managed Service Providers that use the software to service clients across the globe.
REvil is the same threat actor that hit meatpacking giant JBS with a ransomware attack at the beginning of June, shutting down a good portion of the company’s production capabilities and threatened to create supply chain disruptions and sharp cost of goods increases. The REvil ransomware (aka Sodinokibi, Sodin) is a notoriously aggressive and highly evasive threat that maintain obfuscations and prevents detection.
Detection and prevention strategies
A recently released report by Cybereason has detailed how malicious actors are fine-tuning their ransomware campaign tactics, and how both the frequency and severity of successful ransomware attacks have tremendous impact on victim organizations and their ability to conduct business.
The full REvil attack involving Kaseya can be presented as process tree for a complete view of the attack narrative:
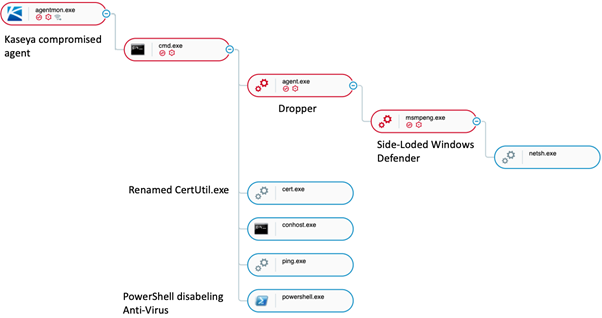
Tips gleaned from the attack
- Kaseya has released a VSA Detection Tool which analyzes the system in order to detect if any related IOCs are present
- Keep systems fully patched: Make sure your systems are patched in order to mitigate vulnerabilities
- Regularly backup files to a remote server: restoring your files from a backup is the fastest way to regain access to your data
- Use security solutions: protect your environment using organizational firewalls, proxies, web filtering, and mail filtering
- Obtain and ensure Anti-Ransomware and Anti-Malware features on next-generation antivirus solutions, and set the protection mode accordingly
The best ransomware defense for organizations is to focus on preventing a ransomware infection in the first place. Organizations need visibility into the more subtle Indicators of Behavior (IOBs) that allow detection and prevention of a ransomware attack at the earliest stages.
Ransomware defense is achievable via multi-layered prevention, detection and response, including:
- Anti-ransomware prevention and deception: This uses a combination of behavioral detections and proprietary deception techniques that surface most complex ransomware threats and end the attack before any critical data can be encrypted.
- Intelligence-based antivirus: This blocks known ransomware variants leveraging an ever-growing pool of threat intelligence based on previously detected attacks.
- NGAV: This genre of cyber defense is powered by machine learning and recognizes malicious components in code to block unknown ransomware variants prior to execution.
- Fileless ransomware protection: Attacks utilizing fileless and MBR-based ransomware can be missed by traditional antivirus solutions, so make sure to obtain this type of protection
- Endpoint controls: Hardens endpoints against attacks by managing security policies, maintaining device controls, implementing personal firewalls and enforcing whole-disk encryption across a range of device types, both fixed and mobile.
- Behavioral document protection: This can detect and block ransomware hidden in the most common business document formats, including those that leverage malicious macros and other stealthy attack vectors.





















