Here are some typical tricks that scammers are refining, to lure you into submitting your banking and login details to them.
Temperatures are rising and the days are getting longer, which means it is that time of the year again: summer vacations. Whether you are planning a relaxing beach getaway, an adventurous road trip, or exploring a new city, summer holidays offer a much-needed break from the daily routine.
Unfortunately, cybercriminals think so too, and as many of us prepare for a break from the day job, they are gearing up for “play”. In May 2023, the period running up to summertime, 29,880 new domains related to holidays or breaks were created. This represents a 23% YoY increase compared with the same period last year, when 24,367 new domains were created. Of those websites that went live, one in every 83 were either malicious or suspicious.
Be wary of vacation-linked traps
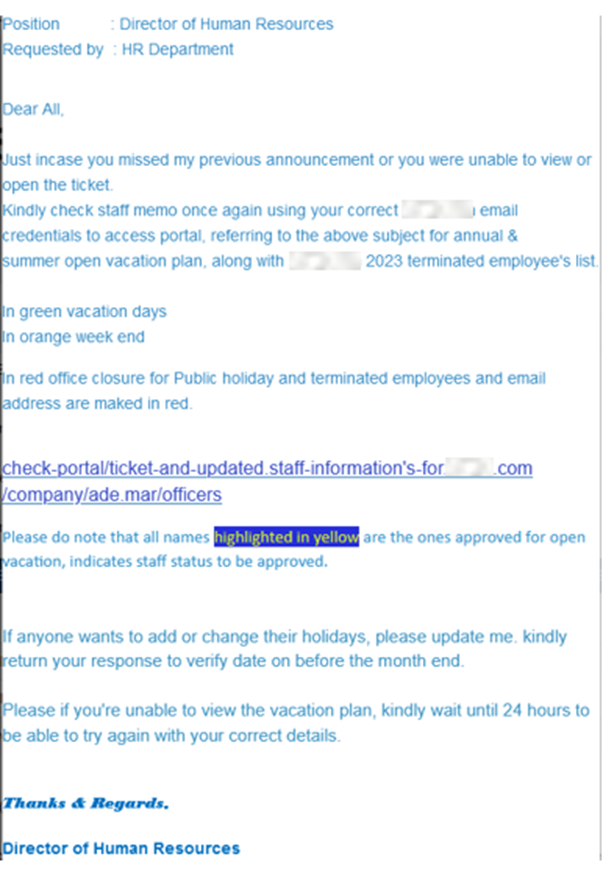
Several seasonal phishing campaigns are running in the wild now. One of these involves an email purportedly sent from “name of the target’s company” Director of Human Resources” with the subject “(name of the target’s company) Submittal – for – vacations – approval – announcement.” (refer to screenshot)
The email is a fake announcement from the Director of Human Resources regarding the annual and summer open vacation plan for the year 2023. It provides information about vacation days, weekends, office closures for public holidays and terminated employees. To enter this list, the victim needs to click on the malicious link that mimics a legitimate Microsoft login page.
Typically, phishing emails appear to be from a known contact or organization and contain malicious attachments, or links to malicious websites. Attackers often set up fake websites that appear to be owned by a trusted entity like a bank, workplace, or university. Through these websites, attackers attempt to collect private information like usernames and passwords, or payment information.
Generative AI improves phishing
Previously, phishing emails can be easy to spot due to poor quality English and improper use of fonts, logos, and layouts. However, many cybercriminals are becoming more sophisticated at creating authentic-looking messages, using professional marketing techniques to test and improve the effectiveness of their emails
Generative AI has also become the tools that hackers and low-skilled cybercriminals use to craft the perfect code and email copy that could dupe even the most suspicious recipient.
In another genre of summer-related phishing, some phishing emails were observed to mimic the airline firm TAP Air Portugal. The email appears to have been sent from no-reply@flytap\.com with the subject “Flight delay compensation EUR 135” or some similar bait words.
Next, the phishing email tries to lure the recipient into clicking on a malicious link in a claim, informing the victim that, as their last flight with TAP Portugal was delayed, they are entitled to compensation. The email contains this malicious site: green\.poc\.mk — which mimics the original firm’s website to steal the target’s credentials.
Standard phishing precautions apply
At all times, consumers need to be especially cautious to remain keep cyber safe:
- Always buy from an authentic and reliable source: Instead of following a link sent through on email or text message, go directly to the retailer by searching for them on your selected browser and locating the promotion directly.
- Be alert to similar domain names: Many scam websites will often use a domain name similar to the brand they are trying to replicate, but with additional letters or misspellings.
- Avoid ‘too good to be true’ offers: If you receive an offer that does appear to be too good to pass up, do not rush to buy it before it sells out.
- Always look for the padlock: Look at whether a potential phishing email’s link URLs start with “HTTPS”. If not, the website is likely to be fraudulent.
- Use endpoint security: Implement email security solutions to prevent them landing in your inboxes in the first place.