Given the past two years of cyberattack surges, organizations need to rethink holistic, perimiterless protection and intelligence to stay on guard.
According to some latest numbers, more than two-thirds of business leaders are now planning to reconfigure their office space to accommodate hybrid working permanently, and three quarters of employees want flexible, remote-work options to stay as a condition of their employment.
The imperative is there, and businesses are already making adjustments to their physical and digital infrastructure, but what about security?
Some businesses are not adequately prepared in terms of their security setup. Routine remote user access to the corporate network means legacy security solutions such as static firewalls and basic virtual private networks are no longer fit for purpose.
With applications everywhere and networks branching off in all directions, organizations are now ‘hyper distributed’ and therefore require more extensive security paradigms for protection.
Network security in hybrid-working
Given the sheer pace of change, it is understandable that businesses would prioritize productivity over network security in the short term, but that short-term fix is now blending into a long-term solution, and businesses need to re-evaluate their security as a result.
Traditionally, a patchwork approach to security has led to a disparate array of siloed solutions, from email and browser security, right through to web app and API protection, firewall-as-a-service, remote-access VPNs, and more.
The challenge now is to consolidate these multiple product points in a unified and cohesive security package, and that is where the Secure Access Service Edge (SASE) comes in.
For years, SASE had already been quietly reframing how large organizations handle their security, but the mass shift to hybrid working has made it relevant for nearly all businesses. In particular:
- SASE converges security and network technologies into a single, cloud-delivered platform that is easy to scale and that facilitates rapid cloud transformation.
- Geographical borders and physical spaces are becoming less relevant to today’s businesses, so it makes no sense for network security to be centralized in the traditional sense. With SASE, security is moved closer to the edge where applications, users and end-points are located, resulting in an agile, unified, low-latency solution that puts user experience, network performance and network security on an equal footing.
- The next step is for businesses to connect the security solutions that exist across users and devices in order to eliminate any potential security gaps. Even when rolling out a SASE solution, organizations need to be mindful of their overall security posture. The more distributed its users, and the more devices that connect remotely, the greater the potential attack surface area for threat actors. Keeping this attack surface limited and protected is arguably one of the biggest challenges facing businesses today.
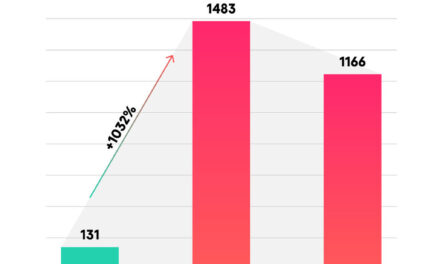
Check Point refers to the expanding attack surface due to a distributed workforce as the ‘remote-access security gap’, in which an estimated 70% of organizations allow access to corporate applications from personal devices. Our data shows that, when preparing to facilitate hybrid working, only 5% of organizations use all of the recommended remote access security settings.
Combining SASE with advanced threat prevention
With cyberattacks against corporate networks increasing dramatically over the past two years, organizations now also have to consider things like endpoint resilience; vulnerability to mobile-related attacks; remote working security policies; and even how well cloud-based collaboration solutions are protected in real-time.
Instead of stitching together disparate security solutions to cover various endpoints and channels, organizations need to embrace unified security solutions with a core focus on threat detection and prevention.
To ensure good protection of devices and internet connections from the most sophisticated cyberattacks and insider threats, organizations need to combine zero trust principles; SASE; client-less connectivity; endpoint/email security; internet access; mobile security and remote VPN access; and real-time threat intelligence into a cohesive and holistic umbrella.