The following disclosure is yet another testament to the fact that apps downloaded from official software repositories are not always safe.
Given most people think that apps from official app stores have been screened for malware, downloading anything from such stores is safe. However, countless cases of failure to detect or contain various types of malicious or tainted apps prove this is not the case, cyber researchers warn.
Case in point: a malware has been lurking in the Microsoft Store and infecting over 5,000 active machines worldwide. The malware has even had time to evolve through the years gaining new features and techniques to its arsenal.
Dubbed Electron Bot, the malware is built with a development framework of the same name (Electron) for building cross-platform desktop applications using Web scripts.
What Electron Bot can do
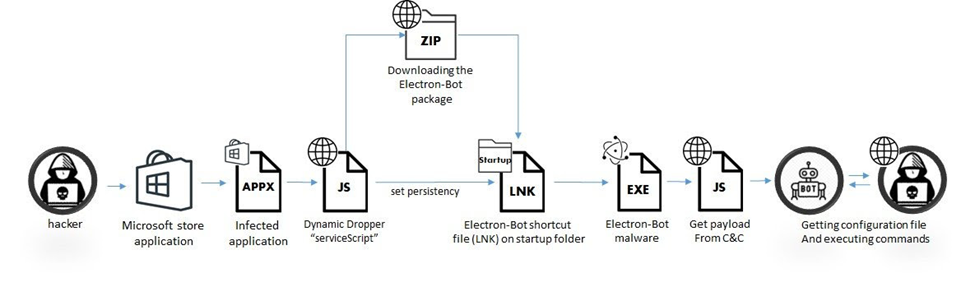
The malware is used for social media promotion and click fraud. It is mainly distributed via the Microsoft store platform and dropped from dozens of infected applications—mostly games—which are constantly uploaded by the attackers.
Electron bot is used for:
- Search-Engine Optimization poisoning: an attack method in which cybercriminals create malicious websites and use search engine optimization tactics to make them show up prominently in search results. This method is also used as a sell as a service to promote other websites ranking.
- Click fraud: as an ‘ad clicker’, the malware runs in the background and constantly connects to remote websites to generate ‘clicks’ on advertisements to earn money for the cybercriminals.
- Promotion of social media accounts: the malware directs traffic to specific content to increase views and ad clicking to generate profits.
- Promotion of online products: another type of click fraud to generate profits with ad clicking to increase certain store ratings for higher sales.
- Manipulation of social media accounts: the malware’s payload contains functions that control accounts on Facebook, Google and Sound Cloud. It can register new accounts, log in, and comment on and ‘like’ other posts in the background.
According to researchers from Check Point Research, who announced their Electron Bot findings, the bot currently does not engage in high risk activities on the infected machine, but it is important to be aware of its capabilities.
Malware created via the Electron framework have access to all of the computer resources, including graphics processing unit functionality. As the bot’s payload is loaded dynamically at every run time, the attackers can modify the code and change the bot’s behavior for high risk activities at will.
For example, cybercriminals can initialize another second stage and drop a new malware such as ransomware or a remote access trojan. All of this can happen without the victim’s knowledge.





















