A recent hacker attack against a hacker cardshop shows that the lucrative trade is not without consequence from among dark peers.
There is nothing like a bit of competition and enmity among hacker communities to keep them in check. Recently, user data of the Swarmshop (a mid-size ‘neighborhood’ store for stolen personal and payment records) were leaked online by other hackers.
The database had been posted on a different underground forum and contained 12,344 records of the card shop’s administrators, sellers and buyers: including their nicknames, hashed passwords, contact details, history of activity, and current balance.
In addition to leak of user data, the database exposed all compromised data traded on the website, including 623,036 payment card records issued by the banks from the USA (62.7%), Canada (3.09%), the UK (3.24%), China (14.02%), Singapore (1.6%), France (3.07, Brazil (1.32%), Saudi Arabia (0.99%), Mexico (0.86%). Further, 498 sets of online banking account credentials and 69,592sets of US Social Security Numbers and Canadian Social Insurance Numbers had also been leaked.
According to Dmitry Volkov, CTO of threat hunting and cyber intelligence company Group-IB, which announced these facts: “While underground forums get hacked from time to time, cardshop breaches do not happen very often. Although the source remains unknown, it must be one of those revenge hacks cases. This is a major reputation hit for the card shop as all the sellers lost their goods and personal data. The shop is unlikely to restore its status.”
Group-IB has already notified the national company emergency response teams in the affected countries about the breach so they could take the necessary steps to mitigate the threat.
Saving face amid the shame
The exposed records show that two card shop users had attempted to inject a malicious script searching for website vulnerabilities in the contact information field. It is not possible to determine if the two events are connected to the breach.
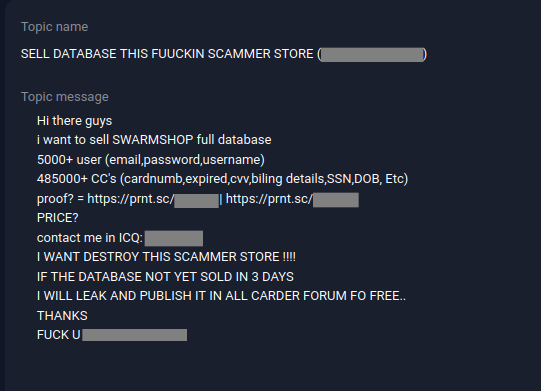
Notably, this is not the first time Swarmshophasbeen targeted by fellow cybercriminals.In January 2020, its records were leaked on an underground forum. The user, likely motivated by revenge, wanted to sell the Swarmshop user database and posted a screenshot allegedly from the cardshop’s admin panel.
The Russian-speaking admins of the cardshop never commented on this thread, but their website did go down temporarily due to a “the transfer to the new server.” When the recent breach happened, the admins of the card shops did not believe it, arguing it came from the last year’s breach after which they had “fixed the bug.” Cardshop users, however, were recommended to change the passwords shortly after the breach report came out.
A week after the post, Swarmshop users were redirected to an ‘under-maintenance’ page when trying to log in. At the same time, cardshop users had reported problems with their account balances.
Telling details of illicit profits
The analysis of the freshly exposed database found that the information was new, as it indicated the latest user activity timestamps. In total, the databased revealed the records offour cardshop admins,90 sellers,and12,250 buyers of stolen data—including their nicknames, hashed passwords, account balance, and contact details for some entries.
Comparisons made between the two sets of leaked database leaked reveal that the number of Swarmshop users has grown by more than 2.5 times. The volume of traded payment records had also increased from 485,617 pieces to 623,036 by March 2021.
It is probably fair to assume that card shop owners’ net profits have also grown exponentially.

















