At least one cybersecurity firm has noted shifts in tactics, techniques and procedures among cyber/state-sponsored threat actors.
Based on the data gleaned from its cybersecurity business, Check Point Research (CPR) has issued a summary of last year’s cyber threat landscape.
According to its data, the year 2023 was marked by a persistent escalation in cyber threats amounting to about 1% year-over-year.
In addition to the scale of attacks, the cyber threat landscape saw an evolution, particularly in how ransomware threats were executed. A notable shift had occurred, with some attackers concentrating on data theft and purely extortion-based campaigns.
The 2023 cyber threat landscape
Breaking down the summary by industry, CPR analysts noted the following in its ecosystem users:
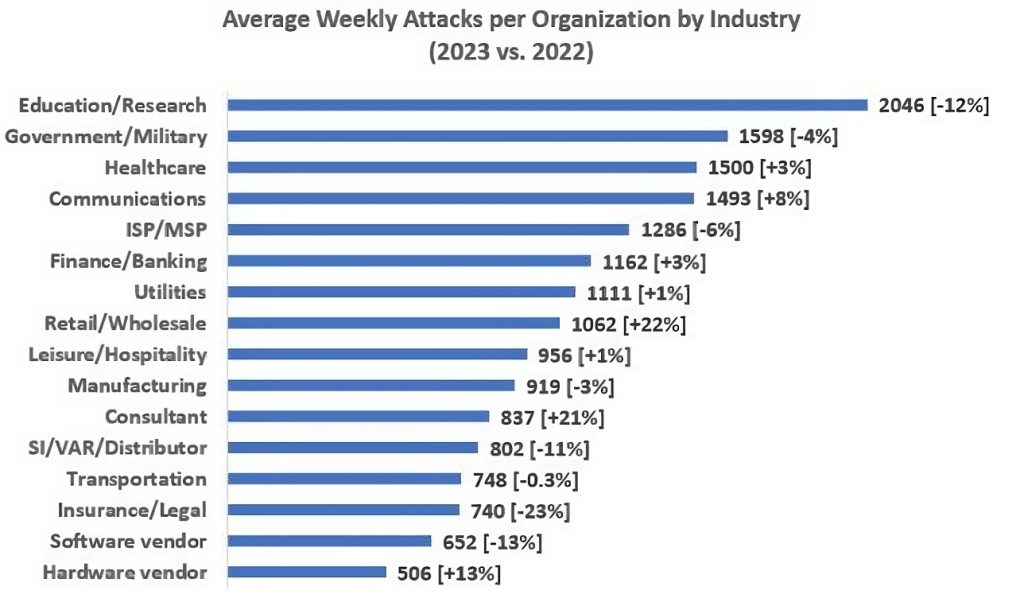
- Education/Research, previously a prime target, experienced a 12% decrease in attacks, while still remaining with the list of industry with the highest volumes of cyberattacks. In ransomware attacks, this industry saw a 22% incidence, among the three most impacted.
- Retail/Wholesale sectors faced a 22% increase, indicating a change in attacker focus. Factors contributing to the increase were cited:
- Increases in volume of consumer data collected due to data-driven digitalization strategies
- Great digitalization due to post-pandemic recovery and market forces
- More complex supply chain networks
- Expansion of e-commerce and online transactions leading to increased attack vectors and vulnerabilities
- Insufficient cybersecurity measures among the smaller players
- High transaction volumes due to revenge purchasing behaviour and other consumer trends such as stronger seasonal sales campaigns
- Healthcare saw a 3% increase in attacks, given the critical nature of its services. This industry also saw a 12% incidence of ransomware attacks — among the top three most impacted.
- Government/Military saw a 16% incidence of ransomware attacks, ranking second in the top three industries most impacted by ransomware in CPR data
- Throughout 2023, there was a 3% (from 7% in 2022 to 10% in 2023) increase in ecosystem users worldwide having been targeted by an attempted ransomware attack. The total rate of ransomware attacks in CPR’s data in 2023 was the highest rate in the past years.
Other notable statistics
Regionally, the Asia Pacific region led with the highest average number of weekly attacks, with an average of 1,930 attacks per organization, a 3% increase compared to 2022.
Africa witnessed a 12% YoY increase in the average number of weekly attacks per organization, reaching an average of 1,900 attacks.
The impact of ransomware on organizations was seen across the main regions of the world, with APAC having the highest ratio with 11% of organizations targeted by ransomware in 2023, while the Americas showed the largest increase YOY: climbing from 5% of organizations in 2022 to 9% in 2023.
Marked by “Mega Ransomware” attacks
In 2023, the landscape of ransomware underwent a significant upheaval, marked by the following trends:
- A major surge in both “conventional” ransomware and “mega”-ransomware that capitalized on a prevalence of zero-day exploits to amplify the extent of damage inflicted plus the number of victims impacted.
- An increasing number of hacking groups boldly (though in some cases, falsely) claimed responsibility for the mega ransomware attacks.
- Emerging regulatory pressures compelled more firms to disclose incidents of cyber extortion, amplifying the collective awareness of the pervasive threat.
- An increasing number of cybercriminals in 2023 adopted a different approach in their ransomware attack strategies. They concentrated more on data theft, followed by extortion campaigns that did not necessarily involve data encryption but rather, threats of public disclosure of the stolen data. This signaled a shift: from disrupting operations through encryption to leveraging stolen data for monetary gains through extortion. This change underscores the increasing adaptability of cyber threat actors.
The overarching narrative of 2023 is that hackers had continued to exploit vulnerabilities throughout the year, leaving a trail of organizations grappling with the aftermath of malicious mega ransomware attacks.