Using a sophisticated and protracted four-pronged tactic, cyberattackers have demonstrated growing large-scale malicious capabilities that augur intensifying travel industry cyber threats.
According to Check Point Research (CPR), the firm’s protection ecosystem saw an average of 1,000 weekly cyberattacks in the leisure and hospitality sector in the third quarter of 2023, a 5% increase year-over-year.
Only recently, online travel-agency Booking.com had its customers details stolen and put up for sale on the Dark Web, highlighting the emergent cyber vulnerabilities that travelers and businesses face in the digital world.
According to CPR analysts, the data breach arose from a complex scheme involving:
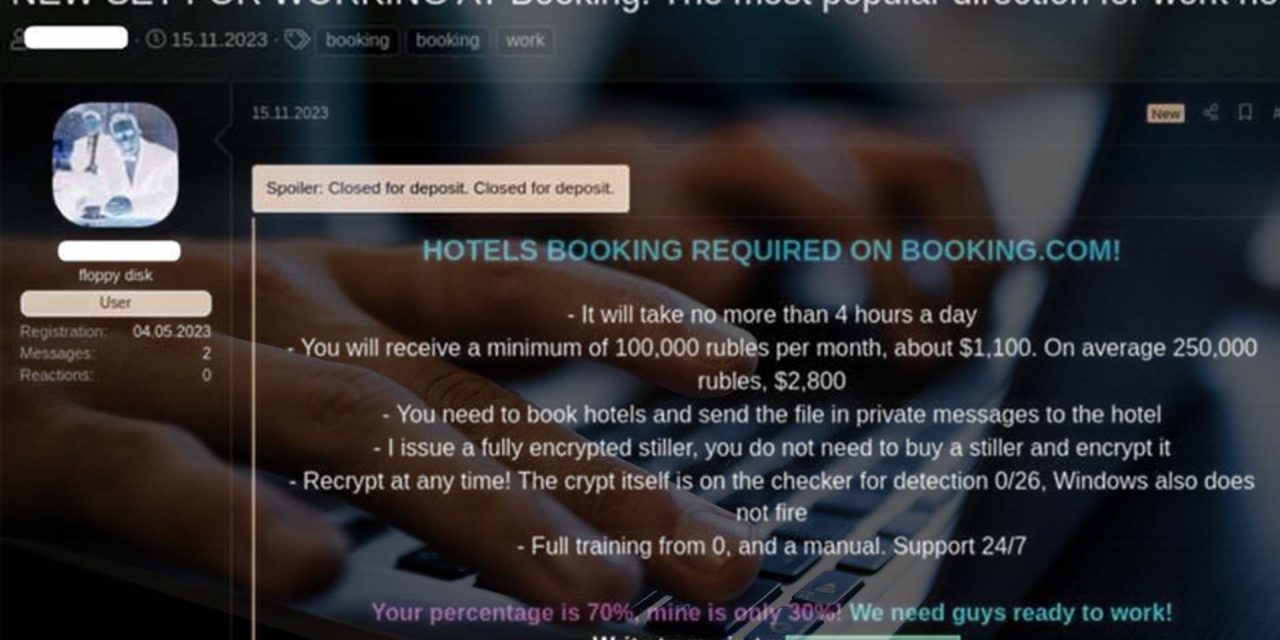
- Malware planted in the supply chain (hotel systems): In the first step, hotels in the Booking.com supply chain were infected with malware. The tactic was to book accommodation via the travel agency, and then to send a malicious file via a messaging system, with the aim of infecting their networks.
- Insider collaborations: Threat actors in the breach left evidence they had been looking to sign “malicious partnerships” with people with insider access to the travel agency. The actual attack vector or scheme was undisclosed.
- Purpose-built phishing kits: Special kits specifically targeting Booking.com were being given away to the Russian cybercrime community before the actual network breach attempt.
- Fake host accounts: Evidence shows a cybercriminal had been searching on the Dark Web for a developer to create a software that creates fake host accounts and lists fake properties on the targeted travel agency.

The scheme described here has far-reaching implications for the travel and hospitality industry, noted CPR analysts: For travelers of this age of intense cyber risk, staying safe means being vigilant about sharing personal information and verifying the authenticity of travel booking platforms; for businesses, it involves investing in advanced cybersecurity measures and constantly updating their digital security strategies.
Awareness, preparedness and widespread cyber collaborations are key to protecting consumer trust, brand reputation and the industry’s financial stability, according to the firm’s Q3 2023 threat report.