A lot of nasty things!
Is it possible and realistic that the cyberattackers can infiltrate and dwell in a network for 11 days or even up to 15 months without being detected?
In a study of a cybersecurity solutions firm’s own customer base, this is what the data shows.
Based on 2020 telemetry and 81 incident investigations and insights from its teams of incident response personnel, Sophos has reported that ransomware featured in 81% of incidents, and that 69% of attacks involved the use of the remote desktop protocol (RDP) for lateral movement inside the network.
Here is a summary of the key findings of their customer ecosystem trends in 2020:
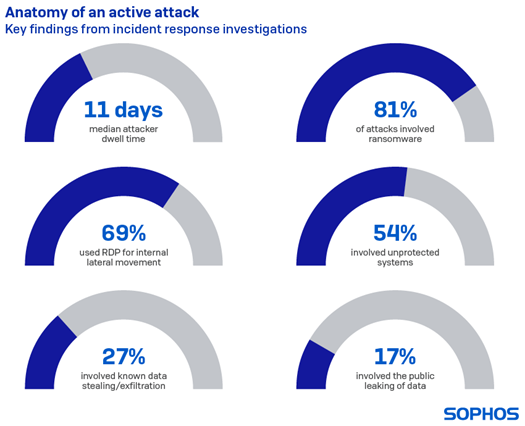
- The median attacker dwell time before detection was 11 days
This lurk time could be used for lateral movement, reconnaissance, credential dumping, data exfiltration, and more, and often takes place at night or outside standard working hours. Ransomware attacks in the study tended to have a shorter dwell time than ‘stealth’ attacks, because they are all about destruction.
- 90% of investigated attacks involved the use of the Remote Desktop Protocol (RDP)
Also, in 69% of all cases in their ecosystem, attackers had used RDP for internal lateral movement. RDP security measures such a VPNs and multi-factor authentication in the investigations tended to focus on protecting external access but did not work if the attacker was already inside the network. As far as Sophos’ own ecosystem goes, the use of RDP for internal lateral movement was increasingly common in active, hands-on-keyboard attacks such as those involving ransomware.
- Top five tools found in victim networks
It was noted that, when PowerShell is used in an attack, Cobalt Strike is seen in 58% of cases; PsExec in 49%, Mimikatz in 33%, and GMER in 19%. Cobalt Strike and PsExec were used together in 27% of attacks, while Mimikatz and PsExec occurred together in 31% of attacks. In 12%, all three tools were used in combination. The detection of these tools can serve as an early warning of an impending attack or can confirm the presence of an active attack.
- Ransomware was involved in 81% of the attacks investigated. The release of ransomware is often the point at which an attack becomes visible to an IT security team. Therefore the vast majority of the incidents Sophos responded to involved ransomware. Other attack types Sophos investigated included exfiltration only, cryptominers, banking trojans, wipers, droppers, pen test/attack tools, and others.
Said the firm’s senior security advisor John Shier: “Over the last year, many of the tools (used in cyberattacks) are also used by IT administrators and security professionals for their everyday tasks and spotting the difference between benign and malicious activity isn’t always easy… It is critical that defenders understand the warning signs to look out for and investigate. One of the biggest red flags is when a legitimate tool or activity is detected in an unexpected place.”
Shier suggested that defenders should technology can do a great deal but, in today’s threat landscape, may not be enough by itself. “Human experience and the ability to respond are a vital part of any security solution,” he asserted.