A threat intelligence platform has detected over one hundred thousand infected devices that yielded tradeable ChatGPT account login credentials.
As more workers take advantage of ChatGPT to optimize their work, their account login credentials have become saleable to cybercriminals because the confidential or sensitive information stored therein can be exploited for targeted attacks against organizations and their employees.
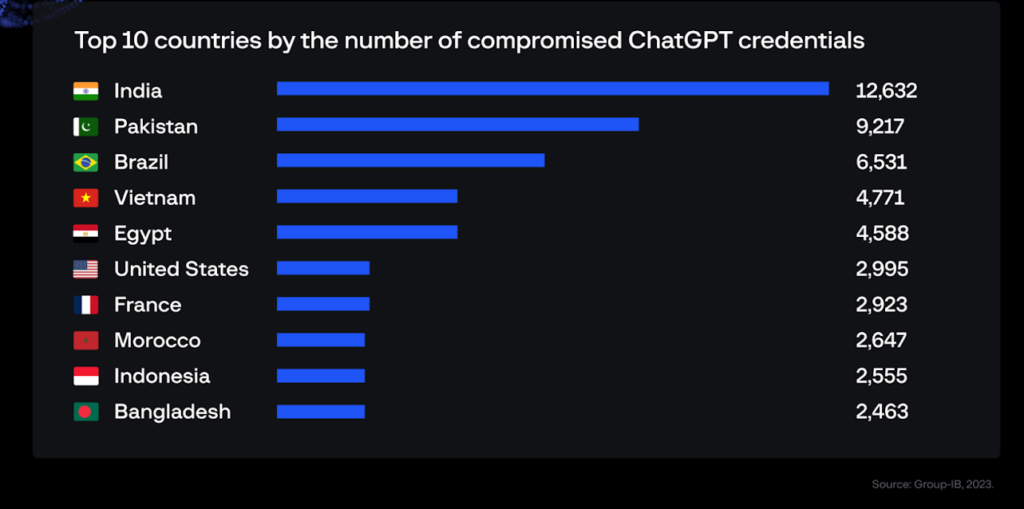
In fact, through analyzing data made available to its threat intelligence platform, a cybersecurity firm has just identified 101,134 devices containing stored ChatGPT account credentials that had been compromised by infostealer malware; the ChatGPT account credentials were being traded on Dark Web marketplaces over the past year.
Furthermore, the firm’s data showed that its customers in the Asia-Pacific region had experienced the highest concentration (40.5% of all credentials stolen between June 2022 and May 2023) of ChatGPT credentials being offered for sale — reaching a peak of 26,802 in May.
The majority of stolen credentials had been due to breaches by the Raccoon infostealer. This type of malware infects as many computers as possible through phishing or other means, in order to collect as much data as possible, and storing the data in logs that can be harvested later to be traded actively traded on Dark Web marketplaces.
Additional information about logs available on such markets includes the lists of domains found in the log, as well as the information about the IP address of the compromised host.
According to Dmitry Shestakov, Head of Threat Intelligence, Group-IB, the firm disclosing its threat intelligence platform findings: “Employees process classified correspondences or use the bot to optimize proprietary code. Given that ChatGPT’s standard configuration retains all conversations, this could inadvertently offer a trove of sensitive intelligence to threat actors if they obtain account credentials.”
To mitigate the risks associated with compromised ChatGPT accounts, readers are advised to change their login credentials regularly and implement two-factor authentication (2FA) or multifactor authentication.