The Asia Pacific and EMEA regions are no less vulnerable, and are a reflection of current medical, socio-political and financial trends.
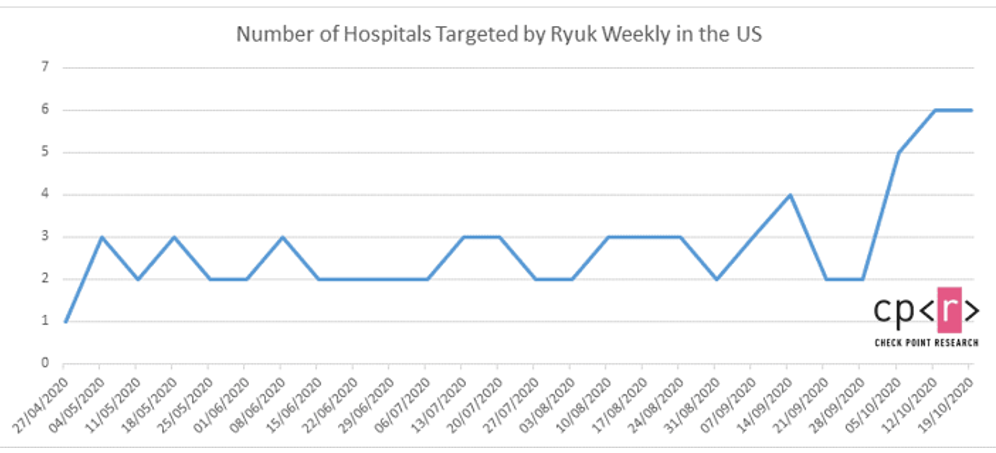
Continuing a trend discerned in Q3 2020, healthcare was still ransomware’s most-targeted industry in the United States in October.
There was an increase of 71% in ransomware attacks against the healthcare sector there, compared to the preceding month. Moreover, hospital ransomware attacks are becoming a global trend as more moderate yet alarming increases occur in the Asia Pacific region (APAC) and the Europe, Middle East and Africa region (EMEA): 33% and 36% respectively.
In APAC, the uptick in ransomware attacks was mostly in Singapore (133% increase in attacks against the healthcare industry) and India (20% increase). The increase in EMEA was derived mostly by a roughly-200% increase in attacks on the healthcare industry in Germany and Belgium.
These findings from Check Point Research follow a global surge in ransomware attacks reported just three weeks earlier. In Q3 2020, the firm saw a 50% increase in the daily average of ransomware attacks, compared to the first half of the year. Ransomware attacks in the US doubled during the same time.
Ryuk takes the lead again
In their warning, the US federal agencies specified that the Ryuk ransomware was responsible for 75% of the ransomware attacks in October.
Unlike common ransomware, which is systematically distributed via massive spam campaigns and exploit kits, Ryuk is used exclusively for targeted attacks. Ryuk was first discovered in mid-2018, and soon after, Check Point Research published the first thorough analysis of this new ransomware which was targeting the United States.
Why hospitals? Why now? It is no secret ransomware hackers’ main incentive is financially-driven, and sometimes fueled by disruption or sabotage agendas. Always struggling to make organizations pay the ransom, hackers find new extortion tactics to leave no escape from answering their demands.
While the pandemic has already recorded a shocking number of 1 million deaths globally, we witnessed the UHS attack on the last weekend in September involving Ryuk, one of the leading ransomware strains out there. According to the recent findings of the International Criminal Police Organization, threat actors have ramped up their attempts to pollute the IT networks of hospitals with ransomware amid the COVID-19 crisis.
The adverse outcome of such an incursion is not restricted to data damage or monetary damages to the organization, but also hinders individuals from receiving quick medical response and has the potential to impact the physical well-being of the patients, making the situation a matter of life or death.
Ryuk has adopted similar tactics with a steady increase in the number of healthcare organizations being targeted, forcing these organisations to pay the ransomware so they can focus on saving lives.
Preventing ransomware
Check Point offers the following reminders to cyber defenders:
Raise your guard towards the weekend and holidays
Most of the ransomware attacks over the past year took place over the weekends and holidays when people were less likely to be watching.
- Virtual Patching
The federal recommendation is to patch old versions in a timely manner, which could be impossible for hospitals. Therefore, using an intrusion prevention system with the latest packages as a virtual patching protocol is a strong safeguard. - Anti-ransomware
Although advanced hacking groups are involved in this business, the encryption process is very extensive, and anti-ransomware with a remediation feature is an effective tool to restore operation in few minutes if an infection takes place. - Employee education
Training users on how to identify and avoid potential ransomware attacks is crucial. Many current cyberattacks start with a targeted email that does not even contain malware, but only a socially-engineered message that encourages the user to click on a malicious link. User education is often considered one of the most important defenses an organization can deploy.
Finally, note that ransomware attacks do not start with ransomware: Ryuk and other ransomware purchase an infection base in targeted organizations. Security professionals should be aware of Trickbot, Emotet, Dridex and Cobalt Strike infections within their networks and to remove them as soon as possible because they open the door for Ryuk.





















