Easier in the short term, maybe, but paying off ransomers may invite further attacks and derail more-effective cybersecurity planning.
In April this year, a survey of 1,263 cybersecurity professionals from around the world covering the Technology, Manufacturing, Financial Services, Retail, Healthcare, Automotive, Legal and Government sectors was conducted to gauge sentiments on ransomware resilience.
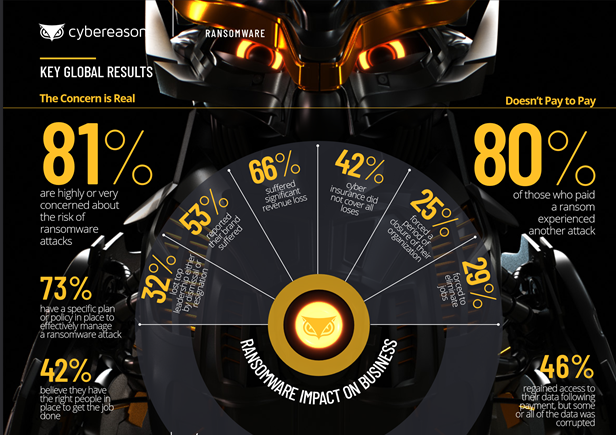
More than half of the global respondents indicated that they had been the victim of a ransomware attack. Among that group, 25 percent of those that chose to pay up had suffered a second ransomware attack, often at the hands of the same threat actor group.
The research, commissioned by Cybereason, also divulged that—of the organizations opting to pay a ransom demand to regain access to their encrypted systems—28% reported that some or all of the data was corrupted during the recovery process.
Amid constant debate and soul-searching among industry experts on this contentious topic, this set of findings adds weight to the argument that it does not pay to pay: organizations should focus on early detection and prevention strategies to end ransomware attacks at the earliest stages before critical systems and data are put in jeopardy.
Summary of findings
Globally, the following data show how ransomware has impacted responding organizations:
- Loss of business revenue: 66% of respondents reported significant loss of revenue following a ransomware attack.
- High ransom demands: 35% of businesses that paid a ransom demand shelled out between US$350,000 to US$1.4m, while 7% paid ransoms exceeding US$1.4 million.
- Brand and reputation damage: 53% of organizations indicated that their brand and reputation were damaged as a result of a successful attack.
- C-Level talent attrition: 32% of respondents reported losing C-Level talent as a direct result of ransomware attacks.
- Employee layoffs: 29% of respondents reported being forced to lay off employees due to financial pressures following a ransomware attack.
- Temporary business closures: 26% of respondents reported that a ransomware attack forced the business to close their business for some period of time.
Other key findings include: the extent to which business losses may be covered by cyber insurance; how prepared respondents were to address ransomware threats to the business with regards to adequate security policies and staffing; and more granular information on the impact of ransomware attacks by region, company size and industry vertical.
According to Leslie Wong, Regional Vice President (APAC), Cybereason: “Businesses must understand that paying a ransom demand does not guarantee a successful recovery, does not prevent the attackers from hitting the victim organization again, and in the end only exacerbates the problem by encouraging more attacks. Getting in front of the threat by adopting a prevention-first strategy for early detection will allow organizations to stop disruptive ransomware before they can hurt the business.”





















