Ransomware victims should instead ask preemptive questions that, if answered correctly, will not lead to worries about ransoms.
Imagine a scenario where your organization has been hit by ransomware or double-extortion ransomware. It is too late to regret now: your IT team has not been able to implement sufficient data backup and disaster recovery fail-safes to not need to pay the ransom.
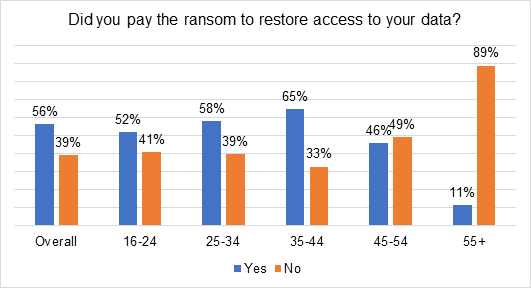
So, should your organization proceed to pay the ransom and get it over and done with? According to cybersecurity firm Kaspersky, last year, 56% of ransomware victims had paid up to have stolen data returned to them, according to a global study of 15,000 consumers. Result: 17% of paying victims did not get back what they wanted.
The percentage of victims that paid the ransom to restore access to their data last year was highest among those aged 35–44; with 65% actually admitting to paying. This compares to 52% of those aged 16–24 and only 11% of those over the age of 55, showing that younger respondents were more likely to pay a ransom than those over 55.
The real question to ask
Whether they paid or not, only 29% of victims were able to restore all their encrypted or blocked files following an attack. Some 50% had lost at least some files; 32% had lost a significant amount, and 18% had lost a small number of files. Meanwhile, 13% who did experience such an incident lost almost all their data.
According to Marina Titova, Head of Consumer Product Marketing, Kaspersky: “Handing over money doesn’t guarantee the return of data. Therefore, we always recommend that those affected by ransomware avoid paying, as that money supports this scheme to thrive. Instead consumers should make sure to invest in initial protection and security for their devices and regularly back up all data. This will make the attack itself less appealing or lucrative to cybercriminals, reducing the use of the practice, and presenting a safer future for web users.”
Additionally, Titova reminded organizations to educate all personnel:
- Do not pay the ransom: Instead, contact your local law enforcement agency and report the attack immediately.
- Try to find out the name of the ransomware Trojan. This information can help cybersecurity experts decrypt the threat and retain access to your files.
- Visit http://noransom.kaspersky.com or other similar ransomware help websites to find the latest decryptors, ransomware removal tools, and information on ransomware protection.
- Enforce basic cyber hygiene and educate staff, especially on the dangers of clicking of links in spam emails or on unfamiliar websites. Remind them to never open email attachments from unknown or suspicious senders, and to never insert USB memory sticks of unknown origin (or other removal storage devices of a possibly dubious nature) into a work computer, especially with remote-working so commonplace now.
- Ensure all computing devices are protected by a comprehensive internet security solution.
- Observe cutting-edge data backup and recovery solutions. Make sure these solutions are religiously operated, maintained and updated with security patches.
With these broad measures in place, ransomware victims can avoid having to ask a self-defeating question of whether to pay a cyber ransom or not, and instead ask preemptively: “How can we do even more to avoid ever having to reward cybercriminals for their crimes, and to worry less about ransom demands?”

















