The drop was noted in the user-base of one cybersecurity ecosystem, but the cyberthreat has generally become more targeted and malicious.
In a report of its own customer base’s incidents, one global cybersecurity firm has noted that 2020 was a year in which the number of ransomware attempts detected and foiled had actually fallen in the small and medium-sized enterprise customers in the South-east Asian (SEA) region.
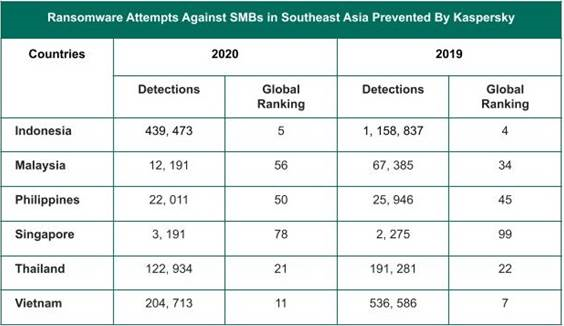
Kaspersky’s internal study show that 804,513 incidents had been addressed in 2020, compared to 2019’s over 1.9 million detections.
Among the six SEA countries covered in the report, only Singapore customers had observed an uptick in the number of ransomware detections. There was a slight increase from 2,275 instances in 2019 to 3,191 in 2020.
For Indonesia, its 158,837 detections in SMEs in 2019 had gone down to 439,473 in 2020, making it the fifth most vulnerable for the volume of ransomware detections. Across other SEA countries including Vietnam, the Philippines, Malaysia, and Thailand, the trend of decreased ransomware incidents was also observed.
How about global trends?
Outside of SEA, China remains at the top spot in terms of ransomware detections in the Kaspersky ecosystem globally both for 2019 and 2020. Meanwhile, Brazil and the Russian Federation switched places for the second and third spots, with Brazil customers now ranking second globally for 2020.
Said the firm’s security researcher Fedor Sinitsyn: “I looked at the statistics for individual families, and it follows the overall drop in the number of detections, mainly due to the drop in the number of WannaCry detections. This family makes up a significant share of all detected ransomware, despite the fact that it has not been supported by the creators for more than three years and exists as a zombie.”
Despite the notable drop in one cybersecurity firm’s clientele, ransomware continues to be one of the most persistent cyber threats to SMEs in the region, according to the firm. It has been issuing a warning to companies of all shapes and sizes against the increasing activities of ‘Ransomware 2.0’ or what is known as targeted ransomware.
Double-extortion is lucrative
Targeted ransomware goes beyond just holding data for ransom, but involves data exfiltration coupled with blackmailing. To pressure victims into paying up, cybercriminals threaten to publish the exfiltrated data to hurt the organizations’ brand image and even increase their liability to data breach penalties.
According to Yeo Siang Tiong, General Manager (South-east Asia), Kaspersky: “The decrease of ransomware detections here should not make us complacent. Since last year, we have been underlining the evolution of this threat. Ransomware groups are now more concerned about quality over quantity. Meaning, from blindly throwing a line into the ocean and waiting for an insecure user to bite, attackers are now more aggressive and targeted towards their victims.”
Yeo mentioned how a single targeted ransomware group alone managed to breach over 61 companies in the Asia Pacific region last year, riding accelerated digitalization of businesses amid the pandemic. “We also predict that the sophistication behind attack methods will only increase and become more sophisticated. SMEs and enterprises should seriously look into intelligence-based cybersecurity technologies, both for endpoint protection as well as detection and response,” Yeo added.