By dispersing small bits of junk traffic across a pool of IP addresses and IP prefixes, cyber attackers are evading detection …
Cybercriminals have reportedly shifted tactics amidst heightened awareness during the pandemic. They have been shifting to bit-and-piece attacks to launch various amplification attacks and elaborate UDP-based attacks to flood target networks with traffic.
According to the new Nexusguard’s Q2 2020 Threat Report this week, Q2 2020 recorded a 570% increase in bit-and-piece distributed denial-of-service (DDoS) attacks compared to the same period last year. Their analysts have witnessed attacks using much smaller sizes—more than 51% of bit-and-piece attacks were smaller than 30Mbps—to force communications service providers (CSPs) to subject entire networks of traffic to risk mitigation. This causes significant challenges for CSPs and typical threshold-based detection, which is unreliable for pinpointing the specific attacks to apply the correct mitigation.
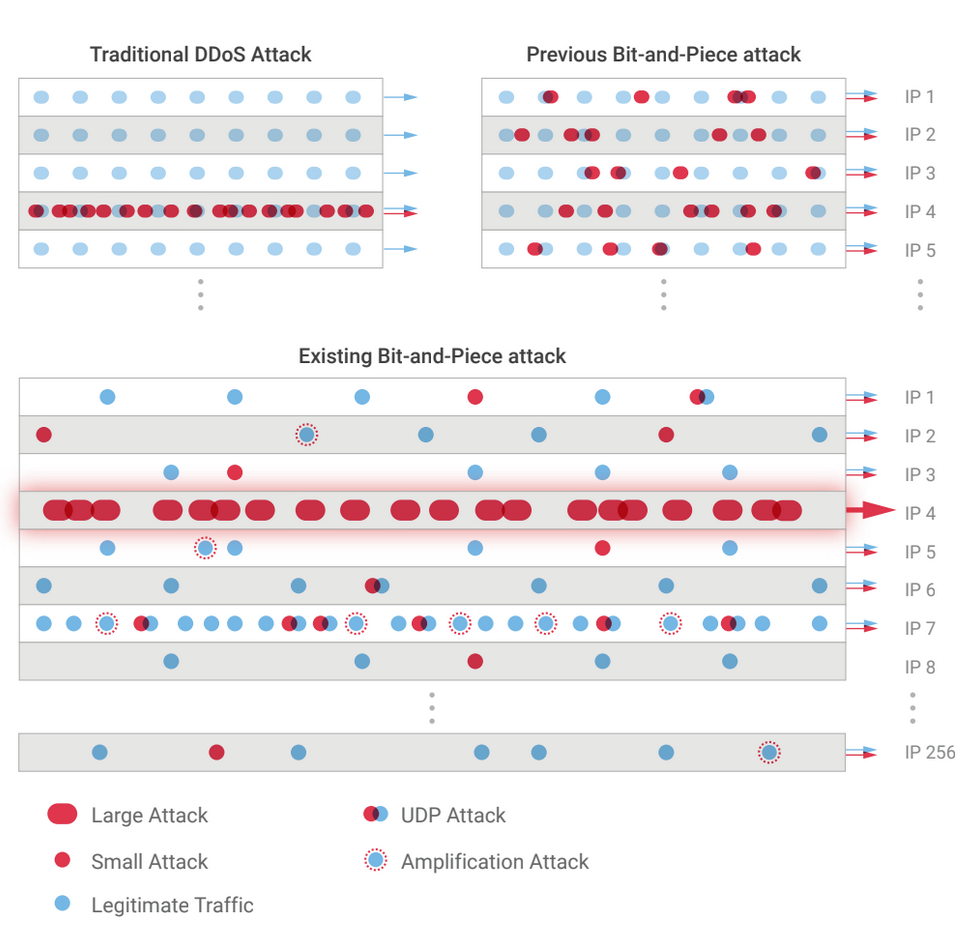
The evolution of attacks means that CSPs need to detect and identify smaller, more complex attack traffic patterns amongst large volumes of legitimate traffic. Botnets are necessarily leveraging resources and technology to become more sophisticated and evasive in order to gain command and control of target systems.
According to Juniman Kasman, the firm’s Chief Technology Officer: “Increases in remote work and learning mean that uninterrupted online service is more critical than ever. Cyber attackers have rewritten their battlefield playbooks and craftily optimized their resources so that they can sustain longer, more persistent attacks. Companies must look into deep learning in their approaches if they hope to match the sophistication and complexity needed to effectively stop these advanced threats.”
How the scene is changing
In the past, attackers used bit-and-piece attacks with a single attack vector to launch new attacks based on that vector. According to the study, attackers have the tendency to employ a blend of offensive measures in order to launch a wider range of attacks, aiming to increase the level of difficulty for CSPs to detect and differentiate between malicious and legitimate traffic.
In the first quarter of the year, DDoS attacks rose more than 278% compared to the same quarter of 2019, and more than 542% compared to Q4 2018. Tapping on the global pandemic, cybercriminals have stepped up DDoS attacks to interrupt service for large companies and individuals for various agendas. What this trend bodes for internet service providers is that they will face increasing challenges to curb undetectable and abnormal traffic that can turn into uncontrollable reflection attacks.
Deep learning, threat intelligence needed
In view of the challenges ahead, the firm’s analysts recommend service providers to ensure that their cyber defenses adopt deep learning-based predictive models in order to quickly identify malicious patterns and surgically-preempt and mitigate any DDoS incident.
Coupled with continual support from threat intelligence services that keep a constant track of botnet scanning, honeypots, CSPs and traffic moving between attackers and their targets, enterprises will be situationally aware of vulnerabilities and global cybersecurity trends.

















