With almost half of incident response requests comprising ransomware, one cybersecurity firm predicts more devious extortion tactics in 2022.
When it comes to cybersecurity, ransomware has become the undisputed story of the year, taking down gas pipelines and government health services. Ransomware operators have refined their arsenal, focusing on reducing attack frequency but increasing the size of their corporate targets. In fact, an entire underground ecosystem has appeared to support ransomware threat groups’ efforts.
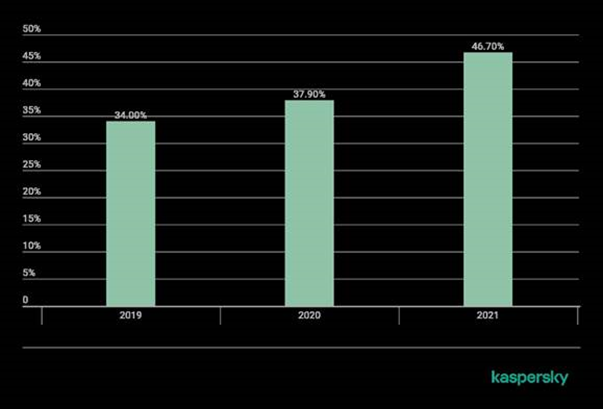
According to Kaspersky, for the first 11 months of this year, the percentage of incident response requests processed was 46.7%—a jump from 37.9% for all of 2020 and from 34% in 2019. Incident response requests by the firm are reserved for mid- to large- sized organizations.
From January to November 2021, nearly every second security incident handled by the firm’s incidence response teams was connected to ransomware—an increase of nearly 12% compared to the scene in 2020.
The most common targets were those in the government and industrial sectors, garnering nearly 50% of all ransomware-related incidence response requests in 2021. Other popular targets included IT and financial institutions.
Threat groups value efficiency
As ransomware operators have shifted to bigger ransom demands and more high-profile targets, they have been facing increasing pressure from politicians and law enforcement agencies.
This has made the threat actors focus on boosting attack efficiency. As a result, Kaspersky experts have note of two important trends that will gain in popularity in 2022:
- First, ransomware gangs are likely to construct Linux builds of ransomware to maximize their attack surface; this is something that has already been seen with groups like RansomExx and DarkSide.
- In addition, ransomware operators will start to focus more on ‘financial blackmail’. This is when operators threaten to leak critical information about companies when they are undergoing critical financial events (i.e., about to conduct a merger or acquisition, or announcing plans to go public) to undervalue their stock prices. When companies are in such a vulnerable financial state, they are more likely to pay the ransom.
According to the firm’s Head of Threat Exploration, Vladimir Kuskov: “In 2020 we began talking about so-called Ransomware 2.0. This year, what we’ve been seeing is this new era of ransomware coming into full force. Ransomware operators aren’t just encrypting data; they’re stealing it from critical, large-scale targets and threatening to expose the information if the victims do not pay.”
For the new year, Fedor Sinitsyn, a security expert at the firm, believes that “law enforcement actions will refine their tactics to remain profitable, especially as some governments are contemplating make paying ransoms illegal.”