If you know the enemy and know cyber defenses, you need not fear the result of a hundred cyberattacks.
It has been estimated by the United Nations that organized cybercrime will cost the global economy around $5.2 trillion in the 2020–2025 period. Some 60% of the huge revenue comes from illegal online markets, 30% from theft of intellectual property and trade secrets, and only 0.07% from ransomware— which, however does the most corporate damage.
With revenues estimated up to US$1.5 trillion a year—meaning 1.5 times more income (as an annual average) than counterfeiting, and 2.8 times more than the illegal drugs trade—such networks constitute a whole economic system that can endanger any organization with severe consequences.
The gravity of such threats has prompted cybersecurity experts at Thales to focus their latest CyberThreat Handbook on how these cybercriminals syndicates operate, so that cyber defenders can think like them and be better prepared for countermeasures and preemptive cyber discipline.
The psyche of cyber enemies
As a network of cybercriminals, such organized syndicates are able to function increasingly effectively: each group specializes in a particular area, and the different groups collaborate to benefit from each other’s expertise. It is this specialization that makes cybercriminals more effective, allowing them to concentrate on a given type of attack, while drawing on know-how from within the network.
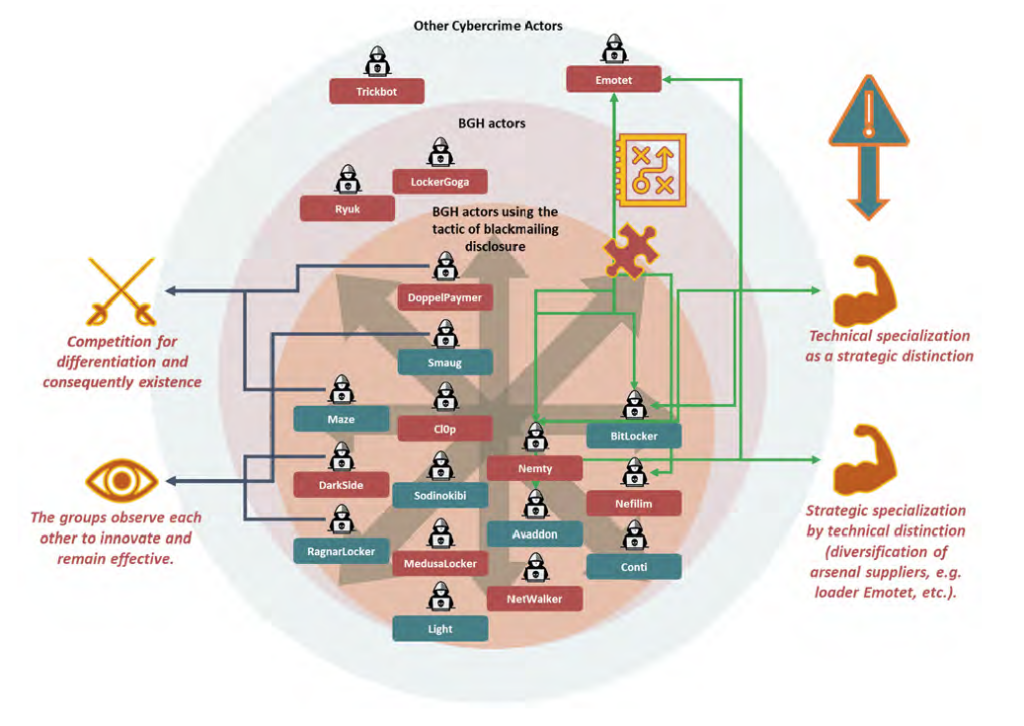
Heading such organized groups are some of the most technically-adept cyber attackers, with highly-sophisticated compromise strategies and substantial financial resources. These are the “Big Game Hunters”, whose tactics, techniques and procedures and technical infrastructure are similar to certain state-sponsored hacking groups. They attack specific targets, such as political institutions and major companies, using ransomware to demand large sums.
To achieve their objectives, cybercriminals use a combination of technical expertise and the panic that they sow in companies and institutions. Panic can have a devastating impact on the consequences of an attack. It is therefore vital not to succumb to fear and give in to threats or blackmail.
Another lesson in the handbook shows that cybercriminals’ targets are extremely diverse and opportunistic; any organization can suffer from it. That is where the experts strongly recommend adopting a clear and detailed cyber crisis strategy as part of business continuity plans.
Without protection or proactive defense in place, the constantly-evolving techniques of cyber attackers will eventually have a snowball effect on weaker organizations in the ecosystem.
Finally, advanced tools and services such as threat intelligence are useful in helping the community anticipate threats as much as possible.