Malware was apparently already lurking in the system, but the solution on trial managed to detect abnormal ‘pattern of life’ behavior.
Recently, a government organization in the Europe, Middle East and Africa (EMEA) region implemented an AI-enhanced cybersecurity trial solution to protect over 10,000 devices.
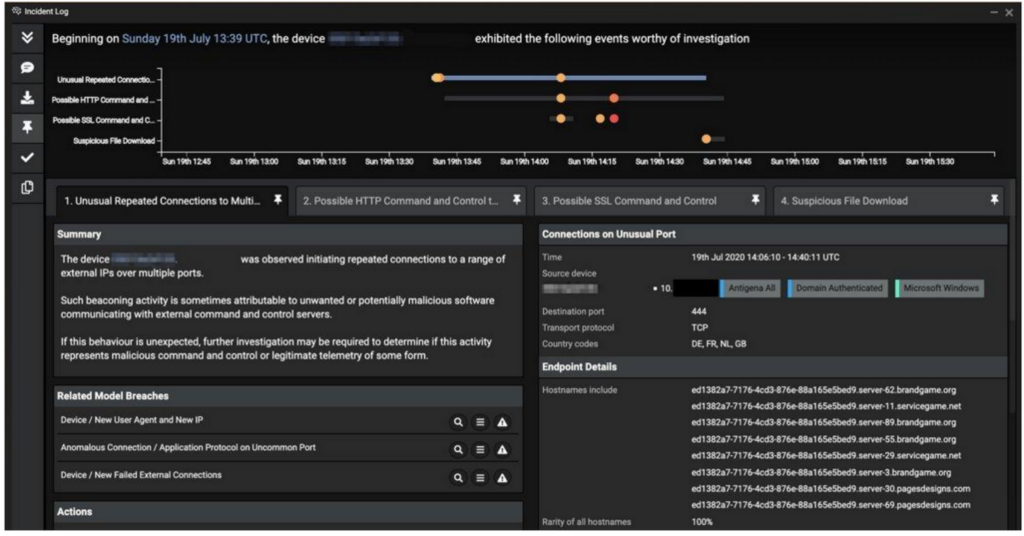
Just a week into the testing, the system detected a device acting anomalously: it had been infected with malware that was beaconing to C2 endpoints via HTTP and SSL and had downloaded a suspicious file. The attackers were using a strain of Glupteba malware in an attempt to steal sensitive information from browsers.
The attack occurred over the course of an hour on a Sunday, meaning the security team’s response time was likely slower than it would have been during a weekday. Had the attackers been able to gain access to an employees’ account credentials, the consequences could have been serious, given that this was a government agency.
How it all started
A device was first detected as initiating encrypted connections to an external domain never seen before across the organization. The device had likely been infected before the AI trial cybersecurity solutions was deployed, most likely through a malicious email attachment or link.
Newer strains of Glupteba also use malvertising, which directs a user to a rare endpoint and forces an anomalous file download. In this case, the device was downloading an executable file, atx777.exe, which appeared to be associated with the stealer Taurus, accredited to the cyber-criminal group ‘Predator the Thief’.
Following this file download, the device initiated further encrypted connections to suspicious endpoints over unusual communication channels. At the same time, the device downloaded another executable file from a domain with an unusual user agent, ‘CertUtil URL Agent’.
Shortly after the payload was dropped, the malware examined the environment in which it was installed and would stop any further processes if it detected the host machine was a sandbox. The malware was able to further conceal itself by excluding Glupteba files from Windows Defender, altering Firewall rules to allow command and control traffic, and by ‘living off the land,’ using tools preinstalled on the device such as CertUtil.
Despite these attempts at evasion, the AI cybersecurity solutions detected the suspicious activity because it fell outside the ‘pattern of life’ for the device and the wider organization. The system flagged the activity as suspicious at the first stages of the attack, and the Cyber AI Analyst on duty investigated the incident in full, revealing some crucial metrics, including the endpoints contacted.
What could have happened
The malware had been installed on the device before the new cybersecurity system started monitoring the environment. Had the trial been active earlier, it would probably have taken a precise response at every stage of the subsequent attack.
In this case, at the beginning of the attack, the solution by Darktrace would have blocked connections to the suspicious domain, zvwxstarserver17km[.]xyz for two hours, preventing any additional malicious downloads.
As the activity escalated, the solution would have enforced a ‘pattern of life’ on the infected device and stopped any malicious command and control communications by blocking all outgoing traffic for one hour.
Learning points
As the race between cybercriminals and security analysts continues, malware authors are employing increasingly sophisticated techniques to avoid detection, says Darktrace.
Although the Taurus stealer utilizes a number of these evasion techniques, the AI technology was able to not only alert and act on the malicious activity without disrupting business continuity, but did so despite the malware already being present on a device before the trial.
Despite this, the solution promptly updated and escalated its actions, and was still precise enough to ensure normal operations could continue. Since the incident occurred at a time when human security resources were at a low or when the team was out of office, the importance of autonomous cybersecurity response was greater than ever.
This incident shows the importance of employing cybersecurity solutions that can keep up with the constantly-improving evasion techniques that hackers are using AI to develop.

















