They claim to have stolen embarrassing photos/data from your work computer, but are extorting only US$1,500? What a bargain!
In analyzing 300,000 extortion emails over a period of 12 months around the world, researchers at Columbia University (US) have uncovered some clues about the financial infrastructure attackers use for extortion emails.
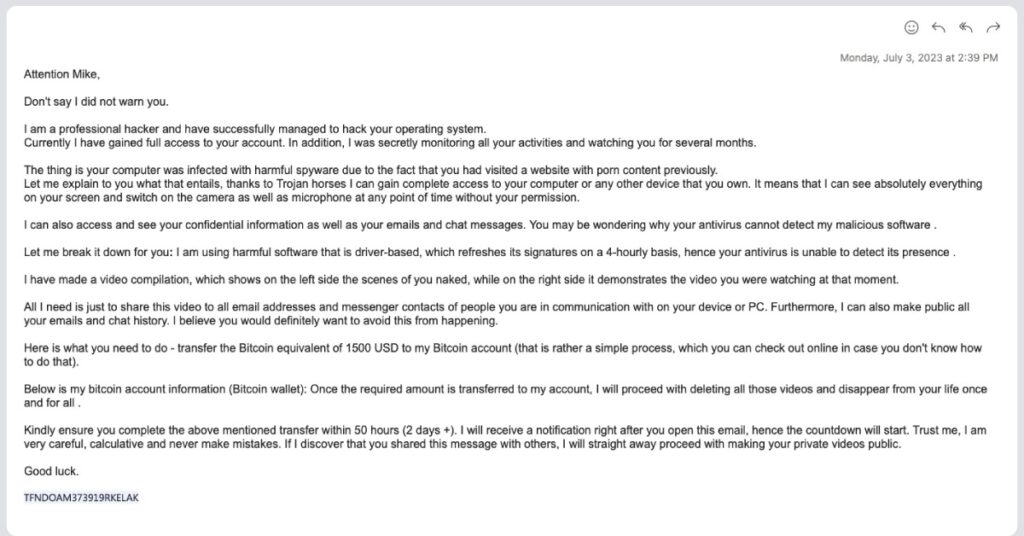
By threatening to release presumably authentic and embarrassing or illicit material (photos, videos, or details of illicit online activity) stolen from a target, blackmail fraudsters attempt to extort money via email.
Data analyzed is showing that these cyber scammers typically target no more than 10 work email accounts at a time, and make moderate payment demands (around US$1,000 in Bitcoin), so as to avoid attracting the full force of security teams and payment systems.
Understanding the attack model
For a start, the team at Columbia grouped the extortion emails by the bitcoin wallet addresses in them. They assumed that an attacker would use the same bitcoin wallet for all their attacks so that one wallet equals one attacker.
The team subsequently found 3,000 unique bitcoin wallet addresses, of which 100 appeared in 80% of the extortion emails. This suggests that a relatively small number of attackers were responsible for most of the extortion emails.
The team also looked at the “sender” email fields for each extortion email. They assumed that an attacker would use the same account for all the emails distributed in a single attack, but may have used a different account for another attack, and so on. The team found that 97% of sender accounts sent out fewer than 10 attack emails each, and 90% of the attacks demanded payments of less than US$2,000 in bitcoin.
According to Asaf Cidon, Associate Professor of Electrical Engineering: “These relatively modest sums make it likelier the targets will cooperate with the extortion, and the relatively small number of emails per sender make it easier for attackers to evade detection by traditional security technologies and anti-fraud measures at payment providers and avoid arousing the attention of law enforcement and the media — which would alert potential victims to the scam.”
Said Mark Lukie, Director of Solution Architects (APAC), Barracuda, which commissioned the research: “Extortion attacks need to be taken seriously by security teams, especially when they are targeting people through their work email accounts. How did the attacker get hold of the account details, for example: Were they exposed or stolen at some point? Or does it mean that the recipient had used their work account and device for inappropriate activity such as visiting questionable websites? Both scenarios have security implications for the company — and for the target. This can be embarrassing and distressing and can potentially make it more likely a victim will pay.”
Recommended security measures to address extortion scam emails include investing in AI-powered email security that can detect and block such threats from ever reaching the intended recipient. This should be coupled with employee training that deters staff from using their work email account to access third party sites or to store sensitive, personal material on work devices. Yet, security policies should also provide harassed victims with a safe and confidential avenue through which to report any incident.





















