Threat actors are rebranding and regrouping faster to escape identification and forensic detection, one cyber threat report suggests.
Based on numbers from its own user ecosystem, a cybersecurity firm has released a yearly report of the global cyber threat landscape for 2021/2022.
The report takes stock of the most up-to-date tactics, techniques, and procedures (TTPs) of ransomware threat actors observed across all geographic locations by the Group-IB incidence response team.
In addition to the analysis of more than 700 attacks investigated as part of the firm’s own incident response engagements and cyber threat intelligence activity in 2021, the report also examines ransomware data leak sites (DLS) for the period between Q1 2021 and Q2 2022.
Important findings
As far as the data used for the report was concerned, here are the observations and conclusions:
- Over the last three years human-operated ransomware attacks have overshadowed other threats in the study.
- The rise of initial access brokers, and the expansion of Ransomware-as-a-Service programs (RaaS), have become the two main driving forces behind the continuous growth of ransomware operations in the ecosystems under study.
- Ransomware gangs in the study had become way greedier since 2020.
- Ransomware downtime in the data had increased from 18 days in 2020 to 22 days in 2021, which is said to show increasing sophistication of the threat actors.
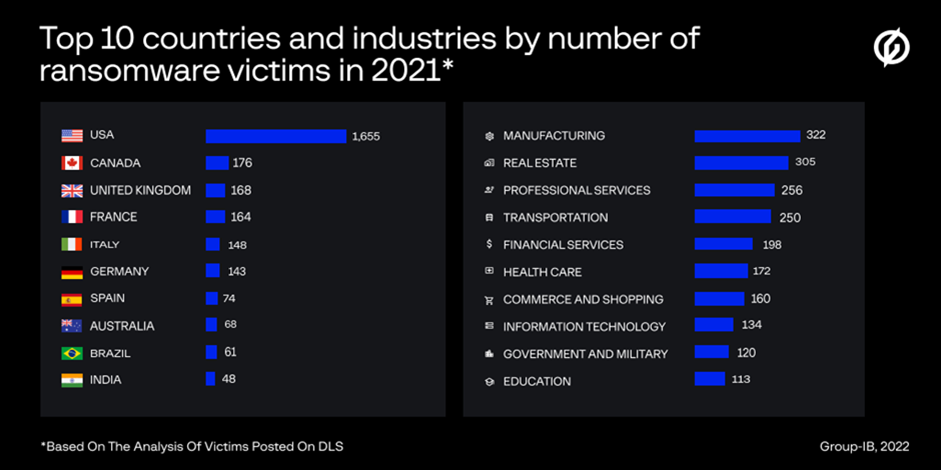
- Between Q1 2021 and Q1 2022, the Asia Pacific ecosystem was the third-most frequently targeted region after North America and Europe—based on the analysis of victim data posted on ransomware DLS. The rankings of 10 countries for number of victimized organizations posted on DLS are: Australia (68), India (48), Japan (32), China (30), Taiwan (22), Hong Kong (20), Thailand (19), Indonesia (17), Singapore (17), Malaysia (14).
- 63% of cases analyzed by the Group-IB incident response team involved payment of ransoms due to the use of double extortion ransomware facilitated by RaaS.
- In the data leak sites, Lockbit, Conti, and Pysa have turned out to be the most aggressive gangs in the firm’s study data, with 670, 640, and 186 victims. In 2021, Hive and Grief (a rebrand of the DoppelPaymer), quickly made their way to the Big Game Hunting league of top 10 gangs, accounted for by the number of victims posted on DLS.
- In 2021 47% of all the attacks investigated by the firm’s incident response experts started with compromising an external remote service—exploitation of public-facing remote desktop protocol servers had become the most common way to gain an initial foothold in target networks .
- Ranking second behind ransomware were spear phishing emails in 26% of incidents handled by Group-IB in the analysis.
- In 2020, certain commodity malware families had strong affiliation with specific ransomware gangs. For instance, IcedID was used to gain initial access by various ransomware affiliates, including Egregor, REvil, Conti, XingLocker, RansomExx. However, in 2021 the attribution of ransomware attacks in the Group-IB user ecosystem had become increasingly complicated since many bots such as Emotet, Qakbot, and IcedID were being used by various threat actors
- In 57% of attacks handled by the firm, commodity malware was often used to start post-exploitation activities via loading frameworks such as Cobalt Strike.
- In general, many ransomware affiliates relied on ‘living-off-the-land’ techniques and legitimate tools during the attack lifecycle. Some ransomware gangs tried unconventional approaches:
- REvil affiliates leveraged zero day vulnerabilities to attack Kaseya’s clients
- BazarLoader, used in Ryuk operations, was distributed via voice phishing.
According to Oleg Skulkin, head of the firm’s incident report team: “Given multiple rebrands forced by law enforcement actions as well as the constant migration of affiliates from one RaaS program to another it is becoming increasingly challenging for security professionals to keep track of the ever-evolving tactics and tools of ransomware threat actor. To help corporate cybersecurity teams navigate through and prepare for ransomware incidents we outlined the main trends and TTPs changes and turned them into actionable insights mapped to and organized according to the MITRE ATT&CK matrix.”





















