Industrial control systems were under heavy attack last year, and while cyber-research has also grown, more can be done: report
Throughout the second half of 2020 (H2), the critical infrastructure sectors such as manufacturing, energy, water & wastewater, and commercial facilities sectors—were heavily impacted by vulnerabilities arising from automation and pandemic-related factors.
The increases in vulnerability in that latter half ran as high as 140% compare to that in 2018:
- Critical manufacturing threats increased 15% from 2H 2019 (66% from 2H 2018)
- Energy sector threats increased 8% from 2H 2019 (74% from 2H 2018)
- Water and wastewater sector threats increased 54% from 2H 2019 (63% from 2H 2018)
- Commercial facilities threats increased 14% from 2H 2019 (140% from 2H 2018)
These figures come from industrial cybersecurity firm Claroty, which released its Biannual ICS Risk & Vulnerability Report this week. The research was conducted alongside trusted open sources, including the National Vulnerability Database (NVD), the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), CERT@VDE, MITRE, and industrial automation vendors Schneider Electric and Siemens.
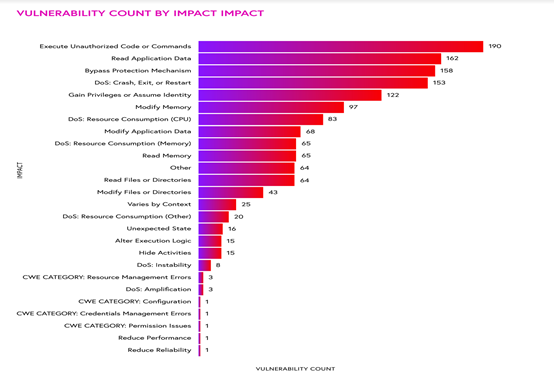
According to the findings, 71% of industrial control system (ICS) vulnerabilities disclosed were remotely exploitable through network attack vectors, and there was a 25% increase in ICS vulnerabilities disclosed compared to 2019, as well as a 33% increase from H1 2020.
During H2 2020, 449 vulnerabilities affecting ICS products from 59 vendors were disclosed. Of those, 70% were assigned high or critical Common Vulnerability Scoring System (CVSS) scores, and 76% did not require authentication for exploitation.
Commenting on the figures, the firm’s Vice President of Research, Amir Preminger said: “The accelerated convergence of IT and OT networks due to digital transformation enhances the efficiency of ICS processes, but also increases the attack surface available to adversaries. Nation-state actors are clearly looking at many aspects of the network perimeter to exploit, and cybercriminals are also focusing specifically on ICS processes, which emphasizes the need for security technologies such as network-based detection and secure remote access in industrial environments. It is heartening to see a growing interest in ICS within the security research community, as we must shine a brighter light on these vulnerabilities in order to keep threats at arm’s length.”
Greater awareness in ICS threats
The report attributes two contributing factors to the increased ICS vulnerabilities: a heightened awareness of the said risks, and an increased focus among cybersecurity researchers and vendors to identify and remediate security flaws as effectively and efficiently as possible.
This growth indicates security research focused on ICS products maturing. Third-party researchers (many of which were cybersecurity companies) were responsible for 61% of the discoveries. This signals a change in focus to include ICS alongside IT security research, further evidence of the accelerated convergence of IT and OT. Among all third-party discoveries, 22 reported their first disclosures, a positive sign of growth in the ICS vulnerability research market.
The Claroty research team had discovered and disclosed 41 vulnerabilities during the H2 2020, affecting 14 vendors. These represent the direction and core objectives of the team’s research focus. Overall, the firm’s researchers have found and disclosed more than 70 ICS vulnerabilities to date.

















