Purveyors of the Dark Web want to be jolly at your expense, says a recent TAU survey.
According to the VMware Carbon Black Threat Analysis Unit (TAU), retail organizations may see a noticeable spike in attempted cyberattacks during the holiday season.
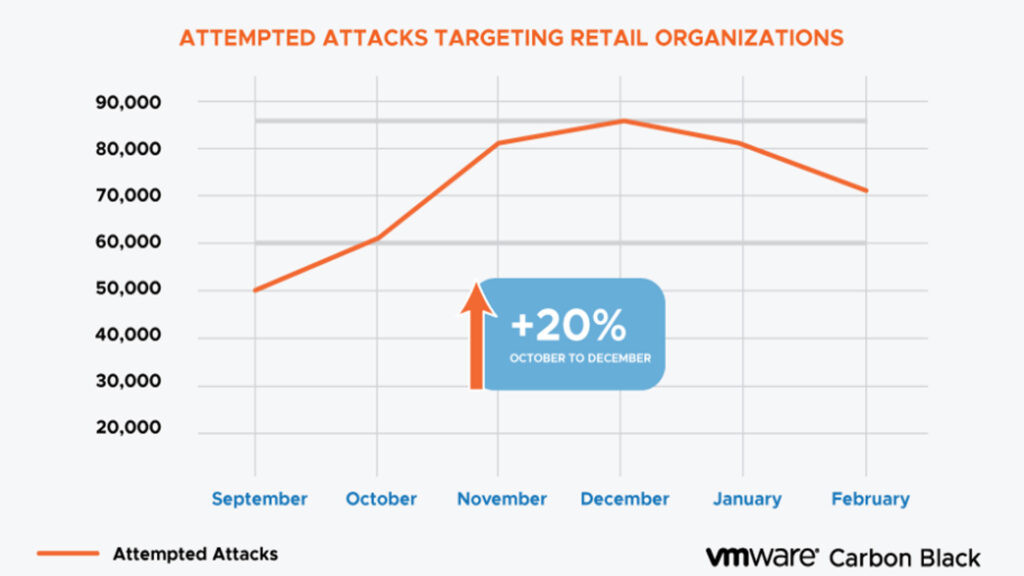
TAU’s analysis across VMware Carbon Black’s global endpoint footprint reveals that global retail organizations encountered a 20% increase in attempted cyberattacks during the 2018 holiday shopping season, continuing a trend that has been tracked since 2016.
In conjunction with TAU’s dissection of attack data, VMware Carbon Black conducted a survey measuring feedback from 20 leading CISOs from global retailers to determine how cyberattacks are evolving, how these CISOs view the threat landscape and what’s being done to stem the tide.
Of note from the survey, 73% of retail organizations said they have seen an increase in cyberattack sophistication over the past year, with 33% of these organizations saying they’ve experienced an island-hopping attack over the same time period. And these attacks are potentially harming more than just brand reputation. Also, 40% of surveyed retail organizations said they had lost revenue in 2019 as a result of a cyberattack.
As VMware Carbon Black has noted in previous vertical-specific reports, the dark web continues to compound the attack landscape. Underground providers are offering listings that could affect consumers and retailers including: Credit-card skimming guides, counterfeit credit cards, financial-specific malware, and access to specific bank accounts via stolen credentials.
According to the survey, retail CISOs are combating these trends with increased headcount, budgets and, in some cases, the implementation of threat hunting teams. The following report presents the highlights of the latest research and includes specific recommendations for how retailers can enjoy a happy holiday season.
Summary of report findings
- Attempted cyberattacks against retail organizations may increase by 20% this holiday shopping season, according to VMware Carbon Black attack data
- 73% of surveyed retail organizations said they have seen an increase in cyberattack sophistication over the past year
- 40% of surveyed retail organizations said they’ve lost revenue as a result of a cyberattack in 2019
- Two-thirds (66%) of surveyed retail organizations said they’ve experienced a ransomware attack over the past year
- Kryptik, Emotet and Obfuse were the most prevalent malware families targeting the retail sector over the past year, according to VMware Carbon Black attack data (of note, Emotet could be found in about 1 out of 5 retail organizations in 2019.) Kryptik was among the infections found in the notorious attack targeting the Ukrainian power grid in late 2015.
- 33% of surveyed retail organizations said they have encountered an island-hopping attack in 2019
- More than half (53%) of surveyed retail organizations said they plan on increasing cybersecurity staff in 2020. Some 40% said they plan to increase security budget by at least 10% in 2020
- 33% of surveyed retail organizations currently have a threat hunting team
- The dark web currently has listings for retail-related information including: credit-card skimming guides, counterfeit credit cards, financial-specific malware, and access to specific bank accounts via stolen credentials.
Recommendations
The good news from the survey is that more than half (53%) of surveyed retail organizations said they plan on increasing cybersecurity staff in 2020. And 40% said they plan to increase security budget by at least 10% in 2020. One-third of surveyed retail organizations currently have a threat hunting team. In view of these statistics, experts in the report have made the following recommendations:
1. Deploy Threat Hunting Teams: For retailers, this is increasingly important around the holiday season, when attempted attacks have historically spiked. The first step is making sure your team has visibility into what’s happening in the environment. From there, baseline what’s “normal” and empower team members to sniff out any anomalies. If the team is spending virtually all of its time responding to alerts, it can be pretty difficult to advance from a reactive position or even know where vulnerabilities exist.
2. Leverage data, facts and perceived risk to lobby for more security resources: As a CISO, translating information security risk into business risk can help business leaders see investment in security as an investment in cost reduction. CISOs should work closely with company leaders to align overall business initiatives with cybersecurity goals. Get these leaders to understand that data is an asset, much like real estate, and that data is a currency that should be protected.
3. Move critical assets to more secure compute configurations through Iron Boxing: The first part of this process is to understand the organization’s crown jewels and to develop a strategy for their protection. This information may be customer data, financial information, sensitive product or people data, or roadmaps for upcoming product launches. Many retailers have multiple access points to this data, so accounting for that total attack surface (including vendors and partners) will be critical to long-term success. Application control technology is thought by many retailers to be one of the strongest forms of protection enabling the organization to meet strict regulatory demands and evolve the program to be focused on more than just compliance.





















