Increasing use of IIoT and automation of industrial control systems and operational technology exposes such infrastructures to all-round risks
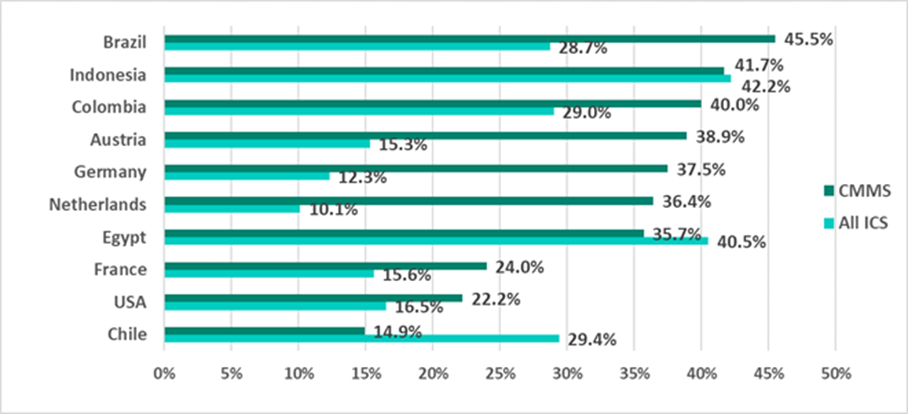
In analyzing H1 statistics and internal data on Computerized Maintenance Management Systems Kaspersky experts predict a shift in advanced persistent threat (APT) activity against industrial control systems (ICS) and operational technology (OT) systems in new industries and locations.

Attack surfaces are increasing due to digitalization in a race for higher efficiency in industrial IoT and smart workflows, including systems for predictive maintenance and digital twin technology. Furthermore, rising energy carrier prices and the resulting rises in hardware prices, could force many enterprises to abandon plans to deploy on-premises infrastructure in favor of cloud services from third party vendors.
Threats may also come from unmanned transportation means and aggregates that can either be targets or tools for attacks. Other risks to watch out for are the heightened criminal activity with a goal to harvest user credentials as well as more volunteer ideological and politically motivated insiders, and insiders working with criminal groups, usually extortionists and APTs. These insiders may be active in productions facilities, as well as technology developers, product vendors and service providers.
Other cyber threats ahead
Besides the growth of hacktivist activity due to internal and external political agendas, more ransomware attacks on critical infrastructure are expected in 2023 due to the fact that it will become harder to prosecute such attacks. Kaspersky experts also foresee:
- Deterioration of international law enforcement cooperation will lead to an influx of cyberattacks in the countries considered to be adversaries. At the same time, new alternative solutions developed domestically may also lead to new risks such as the software containing security configuration errors and easy Zero Day vulnerabilities, making them accessible to both cybercriminals and hacktivists.
- Organizations may face new risks such as a decrease in quality threat detection due to communication breakdowns between information security developers and researchers located in countries currently in conflict.
- Threat intelligence may decrease in quality leading to unsupported attribution and government attempts to control information about incidents, threats and vulnerabilities.
- The growing role of governments in the operational processes of industrial enterprises, including connections to government clouds and services, which would sometimes be less protected than the market-leading private ones, also leads to additional cyber risks. Thus, there is an increased risk of confidential data leaks due to the noticeable number of under-qualified employees in government institutions as well as a still-developing internal culture for responsible disclosure.
New techniques and tactics in future attacks
Kaspersky ICS CERT researchers also listed top techniques and tactics expected to flourish next year:
- Embedding phishing pages and scripts embedded on legitimate sites, and using advanced phishing techniques involving stolen documents and business email compromise strategies.
- The use of broken distributives with trojans packed inside, patches and key generators for commonly used and specialist software.
- As security updates for some solutions become less accessible in some markets, N-day vulnerabilities may be closed even more slowly.
- Abusing basic default configuration errors (such as using default passwords) and easy zero-day vulnerabilities in products from ‘new’ vendors, including local ones.
- Attacks on cloud services and the use of popular cloud service as command-and-control nodes. Even after an attack is identified, the victim may still be unable to block the attacks because important business processes could depend on the Cloud.
- Using configuration errors in security solutions, for instance, the ones allowing to disable an antivirus solution.
- Exploiting vulnerabilities in legitimate software; DLL Hijacking; and Bring Your Own Vulnerable Driver, for instance, to bypass end node security
- The spread of malware via removable media to overcome air gaps
We have entered an era where the most significant changes in the ICS threat landscape are mostly determined by geopolitical trends and the subsequent macroeconomic factors.