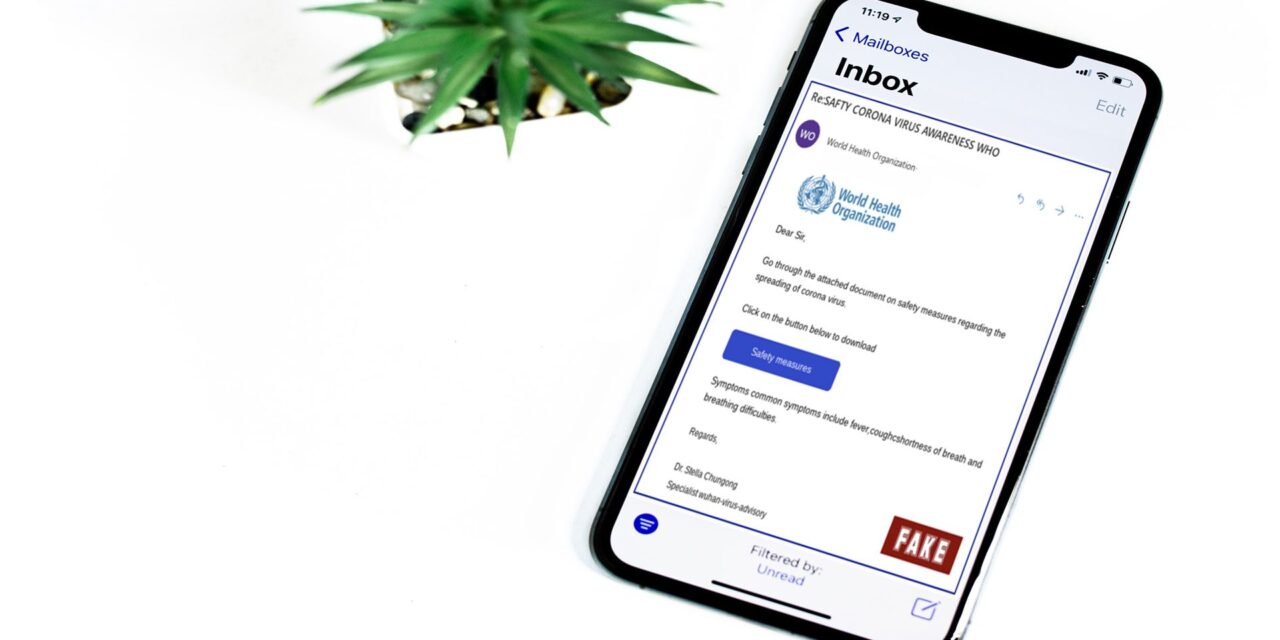
A document supposedly containing COVID-19 tips was weaponized with macros and a JavaScript dropper to tax careless people.
In the last week, SophosLabs uncovered a new email spam attack targeting Italians with a document containing a macro loaded with Trickbot malware. The email takes advantage of COVID-19 fears by offering up a clickable document that allegedly includes a list of precautions to take to prevent infection. Unfortunately, the document is weaponized.
According to SophosLabs, the COVID-19 twist to the spam message may be new, but the mechanisms used to deliver it (including the spam “bots” that send the message, the enclosed scripted Word document and the JavaScript dropper) are similar or identical to those used in Trickbot campaigns that have been active for at least six months.
According to Chester Wisniewski, Principal Research Scientist, Sophos: “The cybercriminals behind Trickbot are likely skilled attackers who leverage the concerns of the day to scare people into clicking. While this is in Italy now, we would expect a similar attack in other countries where fears of COVID-19 outbreaks are high.The best approach to avoid this type of cyberattack is to turn off macros, be extra cautious about what you click, and delete any email that is suspicious or from an unexpected source. Whenever there is a topic of public interest like COVID-19 or the Australian bush fires, we see cybercriminals try to manipulate our concern into an opportunity. We must stay vigilant and be distrustful of incoming communications during times of crisis and only obtain advice from our public health authorities.”
As cybercriminals rise up to any opportunity to attack, here are more tips from Wisniewski that can help us to stay vigilant and protected:
- Never let yourself feel pressured into clicking a link in an email. Most importantly, do not act on advice you did not ask for and were not expecting. If you are genuinely seeking advice about the coronavirus (or any other concern of the day), do your own research and make your own choice about where to look
- Do not be taken in by the sender’s name. This scam says it is from “World Health Organization”, but any sender can put any name they like in the From: field
- Look out for spelling and grammatical errors. Not all crooks make such mistakes, but many do. Take the extra time to review messages for tell-tale signs that they are fraudulent —it is bad enough to get scammed at all without realizing afterwards that you could have spotted the fraud up front
- Check the URL before you type it in or click a link. If the website you are being sent to does not look right, stay clear. Do your own research and make your own choice about where to look
- Never enter data that a website should not be asking for. There is no reason for a health awareness web page to ask for your email address, let alone your password. If in doubt, exit the prompt and entire website or document immediately
- If you realize you just revealed your password to imposters, change it as soon as you can. The crooks who run phishing sites typically try out stolen passwords immediately (this process can often be done automatically), so the sooner you react, the more likely you will beat them to it
- Never use the same password on more than one site. Once crooks have a password, they will usually try it on every website where you might have an account, to see if they can get lucky
- Turn on two-factor authentication (2FA) if you can. Those six-digit codes that you receive on your phone or generate via an app are a minor inconvenience to you, but are usually a huge barrier for the crooks, because just knowing your password alone is not enough.
CybersecAsia would like to add to the list with the following tips that may apply to certain situations or advanced users:
- When you really need to open any unsolicited “useful” document that you just must explore, consider doing so in a sandboxed browser or sandbox environment
- Use a secure virtual machine (with tight security settings) to achieve all of the above and more, if your workflow frequently requires inspection of high-risk documents
- Use an offline, secure computer or mobile device set up solely for high-risk tasks (akin to the internet segregation protocol used in some government agencies)
- Create and maintain a list of dummy accounts for the most targeted social media and web services sites. You will ensure that these accounts have absolutely zero links to any of your digital assets. At your own risk, use these dummy accounts to test suspicious links that ask for unnecessary logins. Doing this in a sandboxed environment is recommended.