Find out how the cross-platform bots and other potential vulnerabilities are already being exploited by malicious actors.
The popular Discord cross-platform application hosts more than 19 million active servers related to different genres and topics (gaming, arts, marketing, finance, sports, etc.).
This popularity has attracted early signs of malicious activity, as demonstrated by the distribution of a multi-functional malware available to anyone on Github. This malware has the capability to take screenshots, download and execute additional files, and perform keylogging—all through the use of Discord’s core features.
Piqued by the potential for major harm that this early warning sign bodes for, Check Point Research (CPR) investigators now reveal their findings.
Bots in discord
Discord lets users integrate code for enhanced features that allows for easier community management. These are the Discord bots, which have grown in popularity with the platform.
Through various centralized services, a wide variety of free bots can be installed. Additionally, Discord bot development services offer custom-made Discord bots for a variety of prices.
The real story behind enabling such powerful bots is that they can easily be abused. Several malicious repositories among GitHub include malware based on the Discord API and malicious bots with different functionalities. They can also be deployed on any supporting platform (OSX, Linux, Windows) due to being created in cross-platform languages.
One malware that CPR investigated was written in Python, and it seems to have several functionalities:
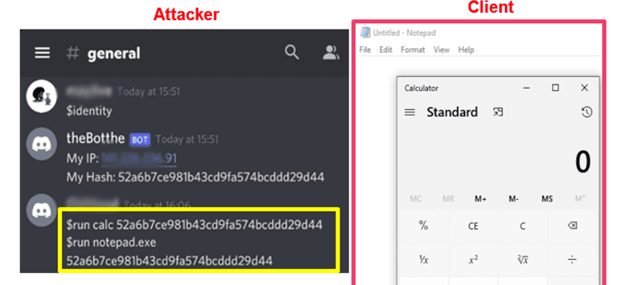
- Open a shell on the running device
- Find different browser tokens: Chrome, Opera, Yandex
- Take screenshots
- Take webcam snapshots from the device’s camera
- Perform key-logging
- Log different malware actions
- Download a file from a given link
- Copy a file to the Windows start directory to run at boot time
- Persistence method:
- Add a backdoor to Discord’s index.js file. This is for persistence purposes. Discord has file integrity checks for its files, but index.js file is an exception. This allows the malware to implement a backdoor in the file which remains undetected (this specific payload is also not detected by different antiviruses). This can be used to run arbitrary code on the client with user privileges once Discord is opened by the user (if it exists on the system).
The code is compiled with Pyinstaller, and the executable remains undetected by the platform’s internal antivirus engines.
A malware wonderland
CPR has found instances where:
- There is no need to install anything but the malware on the victim machine. Not even Discord.
- Encrypted communications make the bot malware difficult to detect.
- File hosting can be used for Dropzone (a server in the Internet that serves additional files to the malware).
These attributes mean that the Discord Bot API can easily turn a bot into a simple Remote Access Trojan. The bot uses the Discord Python module that does not even require the Discord app to be installed on a victim’s machine. The module then supplies the relevant API token to listen to incoming messages on a pre-defined Discord server.
Once a command is provided, the bot executes the pre-defined actions on the victim’s machine. The whole communication process is handled by Discord, which results in a safe, TLSv1.3 ciphered communication.
Aside from the fact that the communication is encrypted (which does not require any effort from the attacker), it is classified as Discord’s traffic. This means there is no way of distinguishing between malicious and legitimate traffic, which makes the malware much harder to detect.
This simple technique provides the attacker with an effortless botnet setup. The Discord server is used as a C2, and the communication itself is handled by Discord.
In addition, as a cross-platform service, Discord allows an attacker to control the botnet from any Discord-supporting platform, as well as mobile devices, which improves the flexibility.
Possible infection chain
Apart from the fact that Discord-based malware does not require the platform to be running or even installed on the victim’s machine, it can be easily be compiled into an executable file (.exe). The malware can then run independently on any Windows machine: using Discord or Python makes no difference.
Such malware can be disguised as a legitimate program, which, once opened, infects the victim’s machine and provides the attacker with remote control access.
In other words, such malware does not specifically target just Discord users, but all users.
In some cases, bots create and send files via Discord servers. These files are intended for the community’s use. This excess of trust can be easily exploited if the bot sends malicious files.
File hosting for cybercriminals
Hackers usually search for a domain where they can store their malicious files without risk. Discord now qualifies as a convenient dump for these criminals. Whenever a user uses the upload function in Discord, the file is uploaded to the CDN (Content Delivery Network) of Discord, and stored publicly.
After uploading the file, the user can copy the file’s CDN URL, allowing anyone that reaches this URL to download that file. In this way, Discord essentially works as a file hosting server, but one that is much easier to establish with no setup at all. An attacker can upload a file to a newly created designated server in seconds, or send the file to another party.
In addition, the attacker’s privacy is ensured. There is no link between the uploader of the file to the URL. Combined with other methods, for example sending the file each interval to change the CDN URL, makes the process of tracing back to the attacker or blocking the payload more difficult.
When CPR used this service to host malicious files, dozens of attacks which used Discord as a hosting server were also uncovered. As of now, any type of file, malicious or not, whose size is less than 8MB can be uploaded and sent via Discord without being analyzed.
Steps to stay safe from Discord
- Avoid visiting unsafe and unknown websites: suspicious links are always a red flag
- Only download files from trusted sources: do not download a file unless you are sure of its provenance and safety
- Monitor your network’s traffic: if Discord traffic exists while Discord is not installed on the system, you may have been infected by a Discord-based malware
- When working with Discord bots, host unknown code on an external server: avoid running them on your personal machine
P.S.: This is a wake-up call to Discord.

















