Names like FamousSparrow and SparrowDoor make advanced persistent threat groups sound furry and cute, but victims often cry fowl (foul).
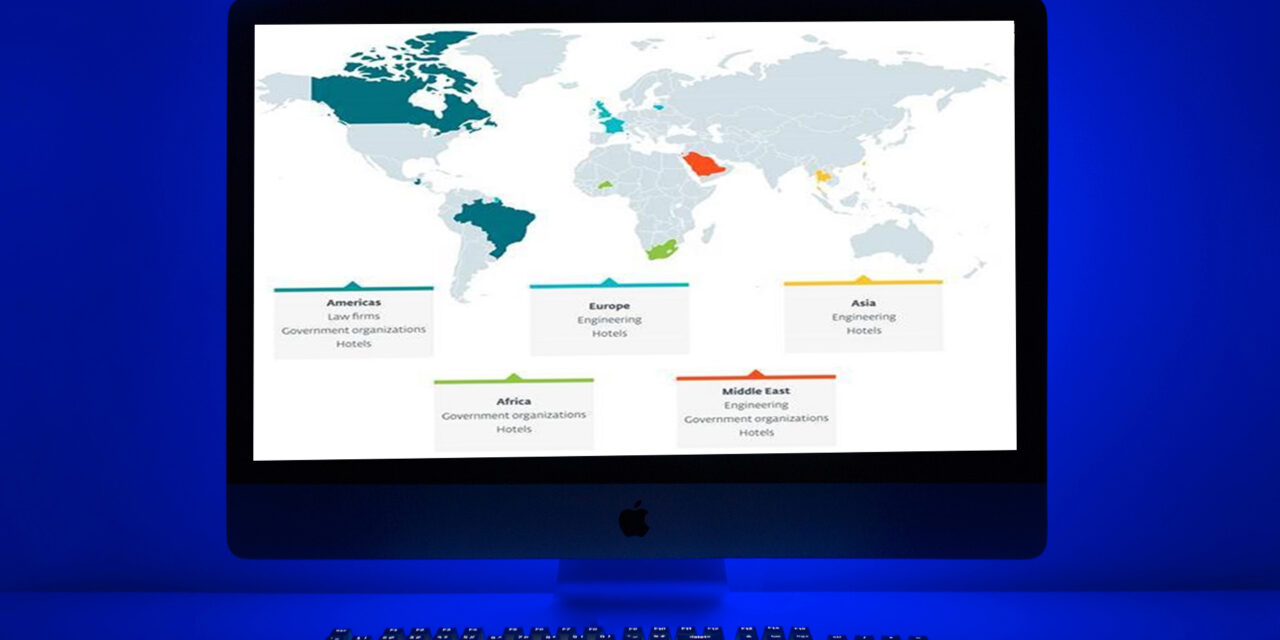
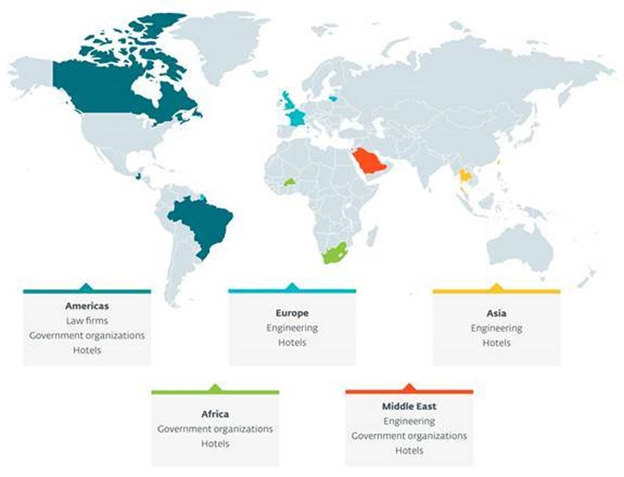
A new cyber espionage group attacking mainly hotels worldwide but not excluding governments, international organizations, engineering companies and law firms, has been discovered.
Telemetry from the ESET user base shows that the group has been active since at least 2019, with victims located in Europe (France, Lithuania, the UK), the Middle East (Israel, Saudi Arabia), the Americas (Brazil, Canada, Guatemala), Asia (Taiwan) and Africa (Burkina Faso).
The researchers have since named this advanced persistent threat group FamousSparrow. It was among the more than 10 APT groups that exploited the Microsoft Exchange vulnerabilities known as ProxyLogon. According to ESET telemetry, FamousSparrow started to exploit the vulnerabilities on March 3, 2021, the day following the release of the patches—meaning it is yet another APT group that had access to the details of the ProxyLogon vulnerability chain in March 2021.
Although the researchers consider FamousSparrow to be a separate entity, the group does share some connections to other known APT groups. In one case, the attackers deployed a variant of Motnug, a loader used by APT group SparklingGoblin. In another case, a machine compromised by FamousSparrow was also running Metasploit with cdn.kkxx888666[.]com as its command-and-control server, a domain related to a group known as DRDControl.
Uniquely, FamousSparrow is currently the only user of a custom backdoor that ESET discovered and named SparrowDoor. The group also uses two custom versions of Mimikatz. Explained one of the firm’s researchers, Tahseen Bin Taj: “The presence of any of these custom malicious tools could be used to connect incidents to FamousSparrow.”
This discovery is another reminder that timely vulnerability patching is critical; or, if quick patching is not possible, networks exposed to the internet should be taken offline, advised Matthieu Faou, another ESET researcher.