The 9+ CVE rating of these vulnerabilities could mean life-threatening supply chain attacks affecting hospital patients worldwide: report
With escalating cybersecurity threats amid high geopolitical tension, healthcare organizations need to be vigilant against network and device vulnerabilities to manage risks of cyberattacks.
Recently, a major supply chain component utilized by hundreds of IoT and IoMT devices was found to contain seven hitherto undiscovered vulnerabilities. Over 150 device models from more than 100 device manufacturers are potentially implicated. Over half of the affected device vendors belonged to the healthcare industry (55%), followed by almost a quarter (24%) that developed IoT solutions.
The vulnerabilities were found most often in medical imaging (36%) and laboratory (31%) machines.
Seven fresh IoT vulnerabilities
The vulnerabilities were found in PTC’s Axeda agent, which constantly communicate with surgical, ventilation and various lab equipment and devices. However, the agent also interacts with things such as ATM machines. Also:
- The vulnerabilities share a lot of similarities to what played out with the Kaseya attack
- If the vulnerabilities are exploited, it means hackers could take full control of these devices, access device data, alter critical patient data or modify configurations in the devices
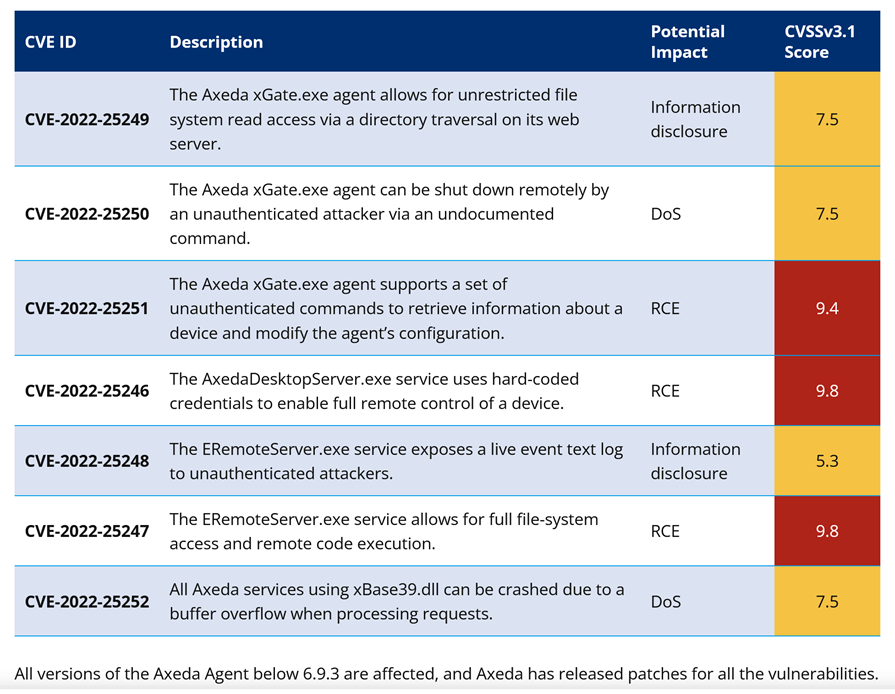
The list of seven fresh vulnerabilities were published by Vedere Labs, in partnership with CyberMDX. Due to the 9+ CVE rating, CISA will be issuing an advisory shortly.
Said Daniel dos Santos, Head of security research, Vedere Labs, Forescout: “The nature of these vulnerabilities could lead to heightened risk and expose healthcare organizations to further cybersecurity threats and risks. (The findings) further illustrate the problems with supply chain components that we have seen before in (other cyber incidents). However, this time it affects a remote management solution that could enable hackers to remotely execute malicious code. Complete protection (these new vulnerabilities) requires patching devices running the vulnerable versions of the Axeda components.”

















