The threat group has been actively attacking game development supply chains since 2012, but they now have a new malware.
Massively Multiplayer Online (MMO) games developers in South Korea and Taiwan are being targeted by a malware group, says researchers from ESET.
In at least one case, the attackers compromised a gaming development company’s build orchestration server, allowing them to take control of the automated build systems. This could have allowed the attackers to trojanize video game executables, although hard evidence is yet to be available.
In another case, threat operators compromised a company’s game servers. With this attack, it would be possible to manipulate in-game currencies for financial gain. ESET had contacted the affected companies and provided the necessary information and assistance to remediate the compromise.
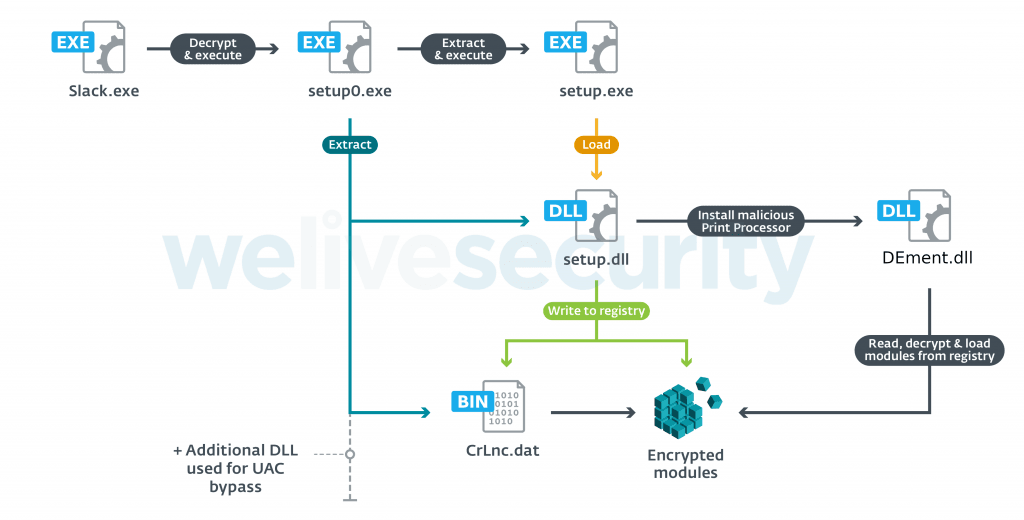
The malware by the Winnti Group has been named PipeMon by ESET. The video games developed by these companies are distributed all around the world, are available on popular gaming platforms, and have thousands of simultaneous players.
Said Mathieu Tartare, an ESET researcher monitoring the Winnti Group: “Multiple indicators led us to attribute this campaign to the Winnti Group. Some of the command and control domains used by PipeMon were used by Winnti malware in previous campaigns. Furthermore, in 2019 other Winnti malware were found at some of the same companies that were later discovered to be compromised with PipeMon in 2020”.
The Winnti Group, active since at least 2012, is responsible for high-profile supply-chain attacks against the video game and software industries, leading to the distribution of trojanized software (such as CCleaner, ASUS LiveUpdate and multiple video games) that is used to compromise more victims. Recently, ESET researchers also discovered a campaign of the Winnti Group targeting several Hong Kong universities with ShadowPad and the Winnti malware. More details about the group’s arsenal are explored in a white paper published in October 2019.
The new modular backdoor PipeMon is signed with a code-signing certificate likely stolen during a previous campaign and shares similarities with the PortReuse backdoor. “This new implant shows that the attackers are actively developing new tools using multiple open source projects and don’t rely solely on their flagship backdoors, ShadowPad and the Winnti malware,” added Tartare. ESET was able to trace two different variants of PipeMon.