The threat researchers who investigated the attack said it was the fastest ever systematic targeted attack.
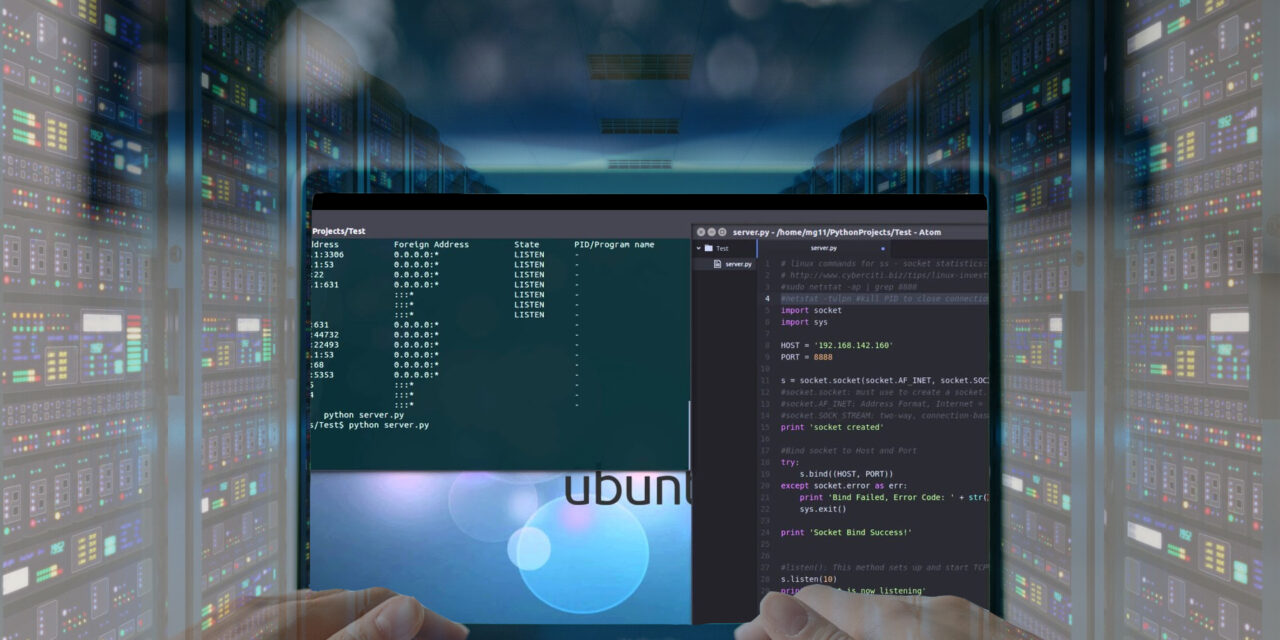
A new species of ransomware written in Python is being used to compromise and encrypt virtual machines hosted on an ESXi hypervisor, all in less than three hours from breach to encryption.
According to researchers from Sophos, who detected the attack, this was one of the fastest ransomware attacks ever investigated and it appeared to precision-target the ESXi platform.
Also, Python is pre-installed on Linux-based systems such as ESXi, so ransomware based on the coding language is an ideal fit. Furthermore, ESXi servers represent an attractive target for ransomware threat actors because multiple virtual machines can be attacked at once, where each of the virtual machines could be running business-critical applications or services.
Attacks on hypervisors can be both fast and highly disruptive. “Ransomware operators including DarkSide and REvil have targeted ESXi servers in attacks,” said Andrew Brandt, Principal Researcher, Sophos.
Attack timeline
The investigated attack began at 12:30am on a Sunday, when the ransomware operators broke into a TeamViewer account running on a computer that belonged to a user who also had domain administrator access credentials.
Within 10 minutes, the attackers had used the Advanced IP Scanner tool to seek targets on the network. The researchers believe the ESXi Server on the network was vulnerable because it had an active Shell, a programming interface that IT teams use for commands and updates. This allowed the attackers to install a secure network communications tool called Bitvise on the machine belonging to the domain administrator, which gave them remote access to the ESXi system, including the virtual disk files used by the virtual machines.
At around 3:40am, the attackers had deployed the ransomware and encrypted the virtual hard drives hosted on the ESXi server.
Security Advice
According to Brandt: “Administrators who operate ESXi or other hypervisors on their networks should follow security best practices. This includes using unique, difficult to brute-force passwords and enforcing the use of multi-factor authentication wherever possible. The ESXi Shell can and should be disabled whenever it is not being used by staff for routine maintenance, for instance, during the installation of patches. The IT team can do this by either using controls on the server console or through the software management tools provided by the vendor.”
Standard best practices to defend against ransomware and related cyberattacks are the deployment of layered protection and defense-in-depth programs combining dedicated anti-ransomware tech with human-led threat hunting.