A post-mortem report shows how the versatility and persistence of cybercriminals effectively increases attack surfaces for exploitation.
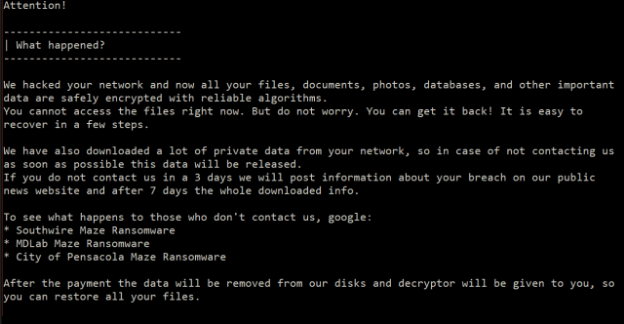
It all started when Maze ransomware attackers penetrated a company network at least six days before their first attempt to launch the payload. During this time, they sniffed out the network, ran legitimate third- party tools, established connections, and exfiltrated data to a cloud storage service to prepare for the release of the ransomware component.
Then, upon launching the first ransomware attack, the operators demanded a US$15m ransom from victim corporation. The target did not pay the ransom.
When the attackers realized the first attack had failed, they launched a second, slightly different attempt. This was in turn intercepted by security tools and the Sophos Managed Threat Response (MTR) team that was handling the incident response efforts.
For the third attempt, the attackers used a reconfigured version of Ragnar Locker’s VM technique, this time running Windows 7 instead of Ragnar Locker’s Windows XP VM—and targeted just one file server. Fortunately, the attack and the Ragnar Locker technique were immediately recognized and blocked.
A Maze of strategies used
Maze is one of the most notorious ransomware families, active since 2019 when it evolved from ChaCha ransomware, and it was among the first to combine data encryption with information theft.
Said Peter Mackenzie, Incident Response Manager, Sophos: “The attack chain uncovered by threat responders highlights the agility of human adversaries and their ability to quickly substitute and reconfigure tools and return to the ring for another round. The use of a noisy Ragnar Locker virtual machine technique, with its big foot-print and CPU usage, could reflect a growing frustration on the part of the attackers after their first two attempts to encrypt data failed.”
To prevent cyberattacks, particularly ransomware, IT security teams need to reduce the attack surface by updating to cloud-based, layered security systems, including anti-ransomware technology. Also, employees need to be educated on what to look out for. They can also consider setting up or engaging a threat hunting service to spot clues that an active attack is underway.
“Every organization is a target, and any spam or phishing email, exposed RDP port, vulnerable exploitable gateway device or stolen remote access credentials provides enough of an entry point for adversaries to gain a foothold,” said Mackenzie.

















