Although the attack was detected quickly by AI technology, further damage still occurred …
Cybercriminals have started using trusted platforms such as QuickBooks and Microsoft Teams brand names to ensnare victims. By sending out phishing emails, they attempt to coax a recipient into clicking a malicious link that leads to a page containing credential-harvesting malware.
Recently, at a leading technology firm in the APAC region, one employee fell victim to a Microsoft 365 account takeover over the weekend. The compromised account was then used to send out hundreds of phishing emails to both internal and external contacts.
The firm had over 9,000 devices being monitored by cybersecurity firm Darktrace, and its AI algorithm had detected the early signs of account compromise and had raised a high-confidence alert to the security team well before the harmful emails were sent. If the security team had acted quickly in response to the alert, the delivery of the phishing emails—and the subsequent account compromise—could have been avoided.
Timeline of attack
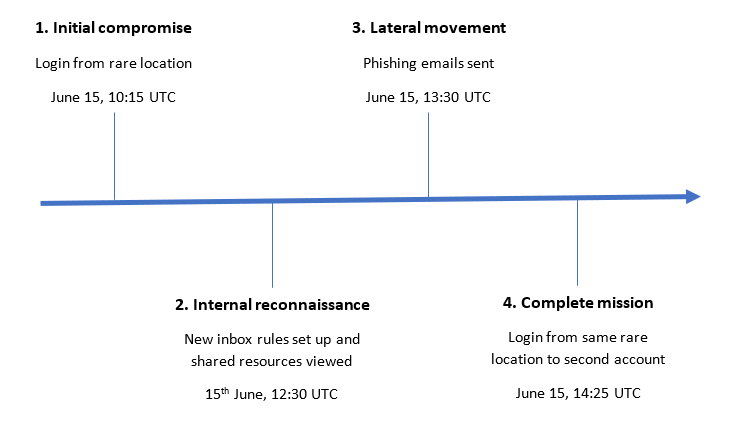
In total, the attacker(s) spent only three hours performing research before acting. This raises questions on the nature of this threat. Was the attack automated? Had the attacker done preliminary research? Did they know what they were after?
A bespoke and targeted attack
Darktrace first raised the security incident when it AI system detected that someone was logging in from an unusual geographical location, promptly setting up new inbox rules, and viewing several shared files. The attacker then proceeded to send out over 200 phishing emails to internal and external recipients.
The emails contained a link to a Microsoft OneDrive landing page titled “Contract & Proposal – CUSTOMERNAME,” indicating the page was specifically built for this attack. The page contained a phishing link hidden under the display text “Click to Review Fax Document.”
Less than one hour after the phishing emails were sent, the cyber defence software detected an unusual login from the same IP to a second account in the organization, indicating this account had likely also been compromised.
How did the attack succeed?
- The attacker leveraged compromised Microsoft 365 credentials, with the initial entry likely via compromised credentials from a previous phishing campaign before the Darktrace system was deployed
- Traditional email security software trusts internal emails
- Phishing emails contained a OneDrive link—a trusted SaaS platform—so other email security products would not have identified these links as suspicious
The technology firm had deployed Darktrace’s Enterprise Immune System across their network and SaaS applications, and consequently had real-time visibility across every event in this attack as it unfolded.
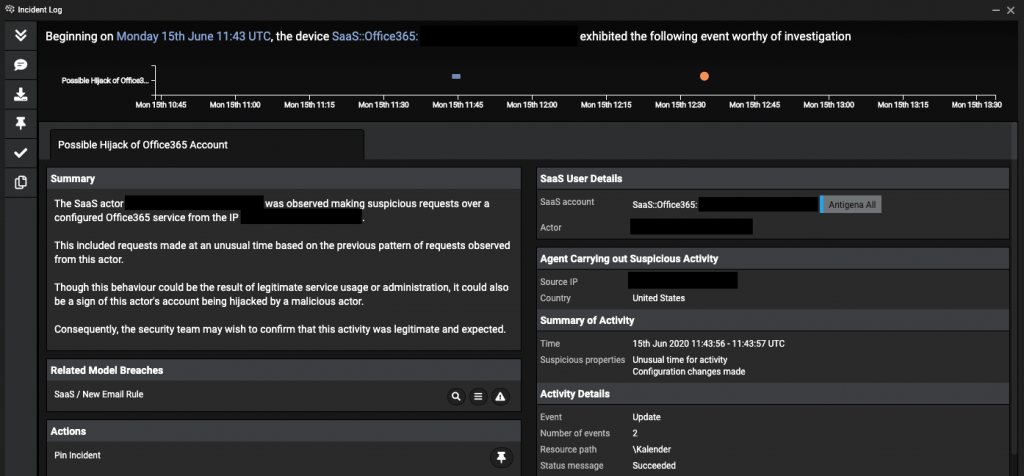
Additionally, when the unusual login location was detected, the Darktrace system immediately launched an automated investigation into the malicious activity, generating a natural language summary of the events and other crucial information to help with incident review.
This attack is another example of the changing nature of cyber-threats in the context of digital transformation. Hackers are not just targeting devices, but identities.
The unusual login location had already caused Darktrace’s software to launch an ongoing investigation into the compromised account, such that an alert was raised just three minutes after new processing rules were set up by the attacker.
With eyes on the technology, a more serious breach could have been avoided, and the breach remediated in minutes.

















