According to one cybersecurity firm’s telemetry, Exchange Server vulnerabilities and enlarged RDP attack surfaces were hotly pursued.
During the first four months of this year, the coronavirus pandemic was still the number one news topic globally; however, the leverage on the sensationalism to bait victims via phishing has become notably less prominent in the threat landscape.
However, the global trend towards work-anywhere and hybrid work arrangements arising from the pandemic containment measures is still a strong attack surface, according to a threat report by ESET.
The featured story of the report recounts the firm’s analysis of a vulnerability chain that allows an attacker to take over any reachable Exchange server. The attack has become a global crisis and ESET researchers have identified more than 10 different threat actors or groups that likely leveraged this vulnerability chain.
Commented Roman Kováč, Chief Research Officer, ESET: “We are continuing to see worrying examples of cybercrooks rapidly abusing trending vulnerabilities and configuration flaws with a focus on achieving high returns on investment. These abuses include continued abuse of the remote desktop protocol, which remains the number one target of brute-force attacks, increased numbers of cryptocurrency threats, and a steep increase of Android banking malware detections.”
Other findings disclosed in the threat report include:
- an ongoing series investigating Latin American banking trojans
- the Kobalos malware which attacks high performance computer clusters and other high-profile targets
- Operation Spalax, which targets Colombian government organizations and private entities
- a highly targeted supply‑chain attack that focused on online gaming in Asia
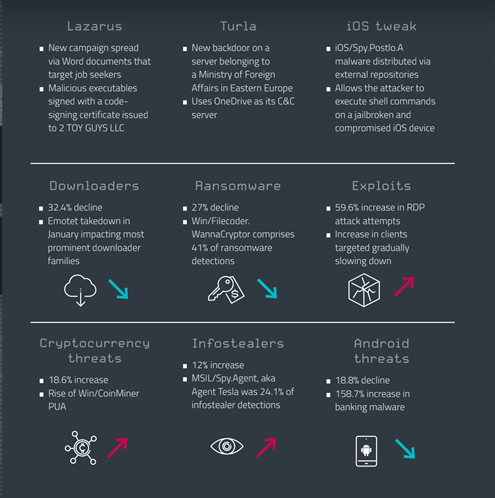
- a new Lazarus backdoor that was used to attack a freight logistics company in South Africa
- new findings about the APT groups Turla and Lazarus
- a malicious iOS tweak that leverages runtime patching in order to change program behavior, to execute shell commands on jailbroken and compromised iOS device
The report is based on the firm’s own telemetry.