One study may be the first to even touch on the psycho-social impact of ransomware attacks on cyber defenders.
After an organization has been hit by a ransomware attack, how do IT managers and their approach to battling cyberattacks?
In one instance, IT managers claimed to be nearly three times as likely to feel “significantly behind” when gauging (subjectively) their understanding of cyberthreats compared to their peers (17% versus 6%).
When it came to recruiting and retaining skilled IT security professionals, 35% of corporate ransomware victims said that it was their single biggest challenge,compared with just those that had not been hit (19%).
Ransomware victims may also spend proportionately less time on threat prevention (42.6%) and more time on response (27%) compared to those that were not (49% and 22% respectively)—diverting resources towards dealing with incidents rather than stopping them in the first place.
These findings were made in January and February 2020 when 5,000 IT decision makers in 26 countries, (US, Canada, Brazil, Colombia, Mexico, France, Germany, the UK, Italy, the Netherlands, Belgium, Spain, Sweden, Poland, the Czech Republic, Turkey, India, Nigeria, South Africa, Australia, China, Japan, Singapore, Malaysia, Philippines and UAE) from organizations with between 100 and 5,000 employees.
Said Chester Wisniewski, Principal Research Scientist, Sophos, the firm that commissioned the study: “The difference in resource priorities could indicate that ransomware victims had more incidents to deal with overall. However, it could equally indicate that they were more alert to the complex, multi-stage nature of advanced attacks and therefore put greater resource into detecting and responding to the tell-tale signs that an attack was imminent.”
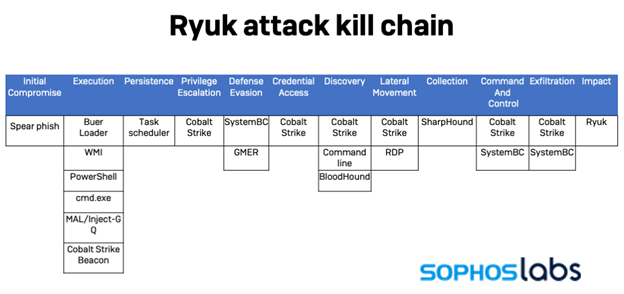
The Ryuk horror story
The fact that ransomware attackers continue to evolve their tactics, techniques and procedures (TTPs) contributes to pressure on IT security teams. Sophos incident responders have found that Ryuk attackers used updated versions of widely-available and legitimate tools to compromise a targeted network and deploy ransomware.
Unusually, the attack progressed at great speed—within three and a half hours of an employee opening a malicious phishing email attachment, the attackers were already actively conducting network reconnaissance. Within 24 hours, the attackers had accessed a domain controller and were preparing to launch the payload.
Wisniewski commented: “Those hit by ransomware were found to have severely-undermined confidence in their own cyberthreat awareness … Whatever the reasons, it is clear that when it comes to security, an organization is never the same again after being hit by ransomware.”

















