The underground service generates a prolific volume of dodgy domain names that are then camouflaged through various sophisticated techniques.
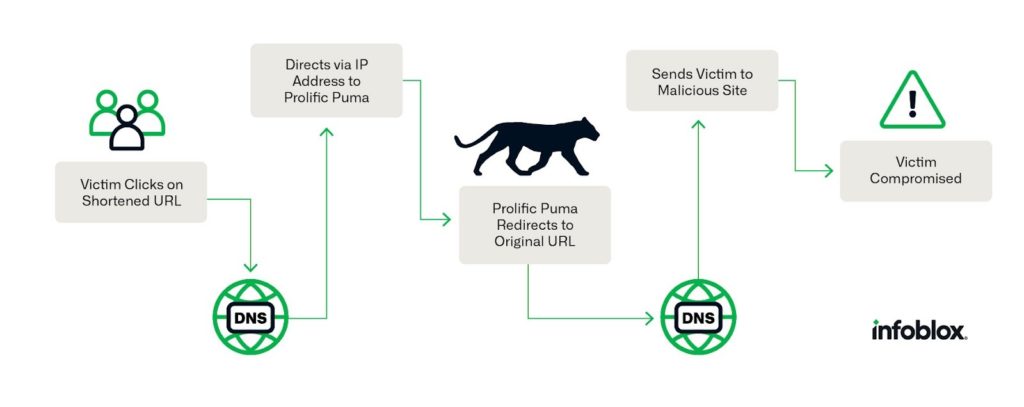
A large underground link shortening service has emerged as a central figure in aiding and abetting malicious actors in their endeavors to evade detection.
Operating since 2020, the shadowy service referred to as “Prolific Puma” leverages the use of Registered Domain Generation Algorithms (RDGAs) to craft domain names that can be employed as “link shorteners”.
Because the connection between the Prolific Puma domains and the final landing pages is indirect, the threat actor has some protection against discovery; but it also fortifies its ability to persist and remain unnoticed through the registration of a large number of domains. Malicious traffic gets divided across these domains at fairly low volumes. Over time, the domains may even gain a reputation as being “good” through ‘strategic aging’ — a technique to bypass security systems that single-out newly registered domains.
Cybercriminals can use this feature-rich service to ensure their activities — including the distribution of phishing schemes, scams, and malware and malicious text messages — remain obscured and undetected, as these domains find a home on anonymous service providers.
Furthermore, Prolific Puma abuses the usTLD, a top-level domain originally reserved for US citizens and organizations, which has become plagued by cybercrime. In a turn of events, the operators of Prolific Puma have managed to circumvent transparency requirements for the usTLD, converting nearly 2,000 domains to private registrations since 4 October 2023.
As this underground service provider’s operations continue to evolve, the revelations surrounding its activities demonstrate how the domain name system (DNS) can be abused to support criminal activity and remain undetected for years. According to Infoblox, the firm disclosing its analyses of Prolific Puma, the underground operation was discovered not through the usual malware or phishing sites but through meticulous analyses of DNS data.
The firm has concluded that blocking the cybercriminals at the DNS layer has the potential to safeguard users from the full spectrum of malicious content that can be propagated through the DNS threat actor.
Generally, organizations can thwart such activities by blocking access to suspicious domains with adequate DNS detection and response systems in place.