Reviewing the past half year has led one cybersecurity solutions firm to predict more attacks ahead. Is your organization sufficiently prepared?
Now that we are into H2 of 2020, what intrusion trends can we discern from the first half of the year?
We all know cybercriminals rode the waves of COVID-19 infections to exploit fear, panic and rushed migrations to remote-working. What other trends were not so obvious even now?
According to one cloud-based cybersecurity solutions firm, cyberthreat activity is intrinsically linked to global economic and geo-political forces.
Jennifer Ayers, Vice President of OverWatch and Security Response, CrowdStrike Inc, said: “Threat hunting data demonstrates how adversaries are keenly attuned to their victim’s environment and ready to pivot to meet changing objectives or emerging opportunities. For this reason, organizations must implement a layered defense system that incorporates basic security hygiene, endpoint detection and response (EDR), expert threat hunting, strong passwords and employee education to properly defend their environments.”
Her comments come with the release of an H1 2020 threat report which includes some interesting findings:
Hands-on-keyboard intrusion activity: The firm noted an explosion in hands-on-keyboard intrusions in the H1 2020 that surpassed the total seen in all of 2019. This significant increase can be attributed to the expanded attack surfaces of organizations rapidly migrating to remote-working, as well as to expanded social engineering opportunities due to increased news and social media chatter.
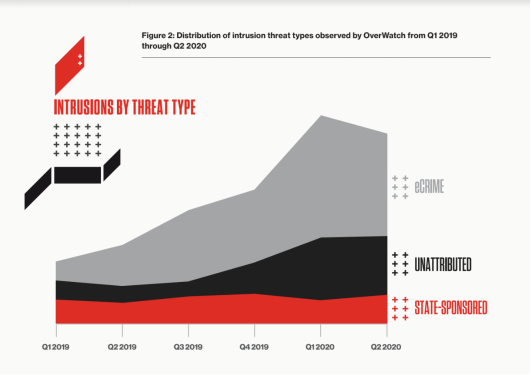
State-sponsored activity: Sophisticated cybercriminal activity continued to outpace state-sponsored activity, an upward trend that the firm has been observing over the past three years, accounting for over 80% of interactive intrusions. This does not indicate a reduction in state-sponsored activity, but rather, reflects the extraordinary success threat actors have seen with targeted intrusions using ransomware and Ransomware-as-a-Service (RaaS) models, which have contributed to a proliferation of activity from a wider array of malicious actors.
Increased targeting of the manufacturing, healthcare and food sectors: There was a sharp escalation of activity in the manufacturing sector in H1 2020 in terms of both the quantity and sophistication of intrusions from both state-sponsored and other cyberthreats, making it the second most targeted vertical observed in the report. Healthcare and food and beverage also saw increased targeting, suggesting that adversaries have adjusted their targets to the shifting economic conditions resulting from the pandemic, focusing on industries made vulnerable by complex operating environments that are experiencing sudden changes in demand.
China continues its aim at telcos: The telecommunications industry continued to be a popular target for the nation-states, specifically China. The report noted six different China-based actors, whose motivations were likely associated with espionage and data theft objectives, conducting campaigns against telecommunications companies in the period under study.
The findings above were gleaned over the firm’s cloud-scale telemetry of over 3 trillion endpoint-related events collected per week, coupled with the detailed tradecraft on 140 adversary groups. Earlier studies had also shown non-malware cyberattacks to form a new normal over 2019.
Looking forward to the remainder of 2020, the researchers expect to see the continued brazen tactics of cybercriminals as they innovate and mature their processes to evade detection technologies and maximize their impact with opportunistic campaigns.
The report asserts that, to protect their data, organizations must secure their distributed workforce with device-agnostic solutions that are scalable and supported by an active threat hunting platform, and offers a single lightweight agent that is easily deployable regardless of an end user’s location.
As reports and expert opinions continue to pour into CybersecAsia, readers can take refuge in the various best practices frequently suggested, such as zero-trust networking, tight privileged access management, carefully-administered bug bounty programs, immutable backup architectures, strengthening of employee cybersecurity awareness as a corporate culture, vigilance to insider threats, and many more.

















