Organizations want a better way to address risks tied to the shift to a remote or hybrid work environment.
Welcome to the pandemic bring-your-own-device (BYOD) era of work. Before December 2019, workers around the world were still wishing for more flexibility to work anywhere, anytime. Now, that wish has become a mandate in many countries.
With widespread Internet access, centralized cloud services, and smart devices in use, the world was actually ripe for such liberation from the office workplace. However, the suddenness of facilitating work-from-anywhere driven by the pandemic had left gaping weaknesses in security and control.
In the face of massive surges in cyberattacks on work-from-home (WFH) users, IT leaders are very concerned about the risks to the enterprise posed by:
- Poorly secured desktops, laptops, smartphones, IoT, and other endpoint devices
- Sharing of official work devices at home between family members
- Unregulated patching/updating of productivity and other software on the devices
- Social media phishing and profiling of targeted WFH staff
In a November 2020 IDC global survey of 300 IT professionals commissioned by BlackBerry, respondents wanted technologies that help to improve endpoint incident detection. For example, they wanted better visibility and control over remote desktops, laptops, and mobile devices, faster security patching, and stronger user authentication and access privilege management.
In light of numerous pandemic-themed phishing and business-email compromise incidents worldwide, survey respondents perceived the ability to consolidate endpoint protection, incident detection, and response capabilities as the key to mitigating attacks, enabling better support, and lowering the total cost of ownership (TCO). A majority even wanted an endpoint security solution to extend beyond traditional endpoints to the cloud.
Intelligent security without a tether
After a year of rushed digital transformation, business pivoting, and ‘firefighting’ due to the pandemic, many organizations have settled down to a saner pace. Organizations are now assessing their weaknesses and mistakes that may have resulted from the urgent need to modify their workplace environment.
With many staff now able to return to the office at least once or twice a week, now is the time for IT teams to sanitize and audit the cyber safety of WFH laptops and smart devices.
According to BlackBerry’s global survey, mobile threat detection (MTD) and endpoint detection and response (EDR) technologies were popular considerations for implementation in the remote-working era.
Security professionals surveyed also wanted endpoint technologies to support the ability to dynamically adapt security policy based on user location, device, and other factors. The most anticipated benefits include enhanced user (worker) experience and less friction (44%), continuous authentication (43%), and reduced remediation cost (43%). More than half (53%) of respondents in the tech sector said adaptive security policies could reduce the cost of issue remediation, while 56% of financial services respondents believed such adaptive security policies could boost worker productivity.
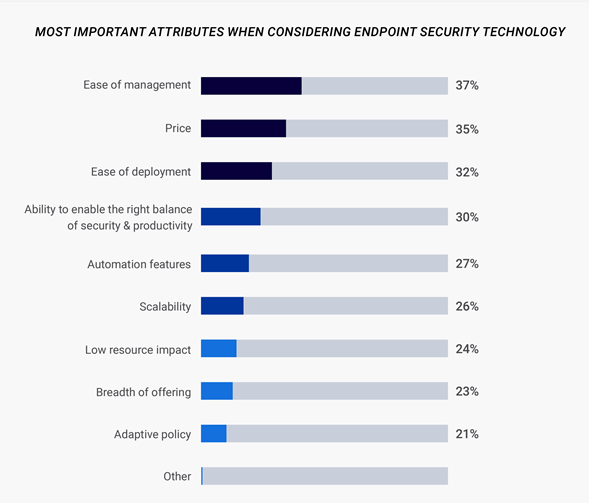
Ultimately, ease of management and deployment, as well as price, were the three most important considerations for choosing a unified endpoint security (UES) solution for unified endpoint management (UEM). Ideally, such a solution must consolidate incident prevention, detection, response, and data loss prevention (DLP) across all endpoints. A solution should also offer significant benefits over current endpoint protection products, including better detection of both known and unknown threats, the ability to manage the endpoint environment via a single console, lower operational expenses, and better integration with endpoint management tools.
Security professionals also perceive UES technology as helping them align better with enterprise Zero Trust initiatives.
AI-enhanced UEM promises even more
IDC’s MarketScape assessment of 18 global vendors for UEM software for 2021notes that firms like BlackBerry fit into the Leaders category because of all-around, class-leading UEM performance. With its integration of innovative Cylance® AI technology, BlackBerry Spark® UEM Suite BlackBerry Spark® Unified Endpoint Management Suite has been ranked by IDC as a leader in the following strengths:
- “With its platform, BlackBerry has a strong solution around secure app development, deployment, and life-cycle management, with specific focus on data security and containerization. This has been a must-have requirement for many companies in regulated industries with high requirements for data security and device/app compliance auditing.”
- IDC notes BlackBerry’s legacy experience with smartphones, enjoying the broadest partnering and integration lineup of mobile operators worldwide among any UEM vendor.
- As for accessibility, major carriers in every region support and resell BlackBerry Spark UEM Suite and other solutions, making BlackBerry an attractive choice for both enterprises and SMBs.
- With the integration of Cylance technology into the BlackBerry Spark® Unified Endpoint Security Suite, the company has an extensive endpoint management/security technology portfolio, along with a newly introduced mobile threat management solution BlackBerry® Protect Mobile, and BlackBerry® Persona with user behavior analytics and continuous authentication solution.
- BlackBerry has strong Microsoft® integration capabilities with its BlackBerry® Enterprise BRIDGE solution for security/managing Microsoft® Office 365® apps in the BlackBerry Dynamics security container architecture, as well as applying policies to O365 apps via Microsoft® Graph API.
New challenges stemming from the global pandemic have heightened requirements for a UES solution at many organizations. To secure employees’ devices wherever they are used, organizations with endpoint protection, endpoint detection response, and mobile threat defense tools want increased visibility over devices accessing the corporate network.








