In one cybersecurity firm’s 2023 metrics, tactics such as remote encryption, and password-locking malicious files to evade email scanners, were common
In analyzing its customer base’s threat detection telemetry, including managed detection and response* data sets, a cybersecurity firm has summarized 2023 findings focused on small- and medium-sized enterprises (SMEs) with up to 500 employees.
First, “nearly 50%” of malware detections for SMEs were keyloggers, spyware and stealers.
Second, initial access brokers (IABs) were using the Dark Web to advertise their ability and services to break specifically into SME networks or sell ready-to-go-access to SMEs they had already cracked.
Third, the number of ransomware attacks against SMEs in the firm’s customer base had stabilized in 2023 data, despite continuing to be the biggest cyber threat to such businesses. LockBit was the top ransomware gang wreaking havoc, followed by Akira, BlackCat, BitLocker and Crytox.
Other findings
The data for the year showed that ransomware operators continued to change ransomware tactics, including leveraging remote encryption (using an unmanaged device on organizations’ networks to encrypt files on other systems in the network), and targeting managed service providers’ remote monitoring and management software. Also:
- “More than 90%” of all cyberattacks in the 2023 incidents analyzed involved data or credential theft, whether through ransomware attacks, data extortion, unauthorized remote access, or simply data theft.
- Second to ransomware attacks, business email compromise (BEC) attacks were the second highest type of attacks targeting SME customers.
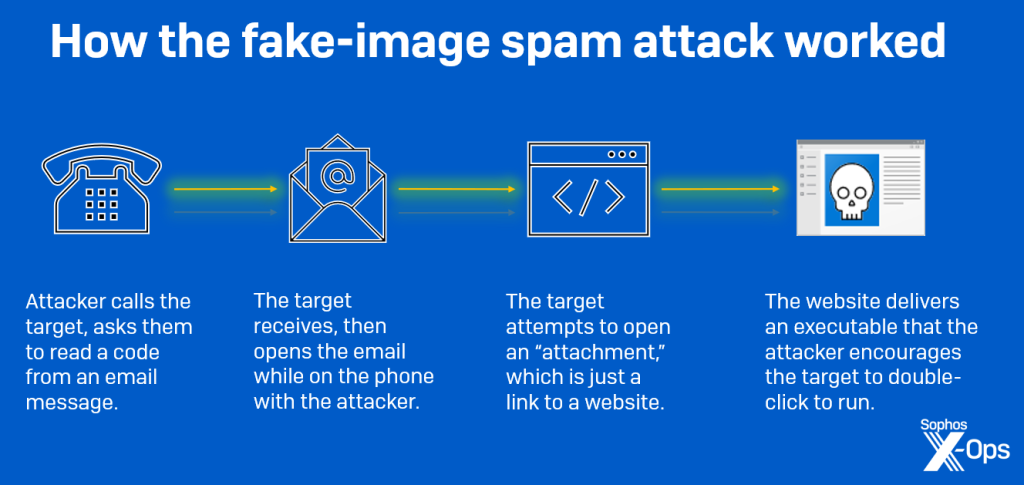
- In 2023 the BEC attacks and other social engineering campaigns contained an increasing level of sophistication, including sending a series of conversational emails or even calling them (on the pretext of package delivery failure) in order to coax them to open specific malicious links and attachments in a malspam attack.
- In an attempt to evade detection by traditional spam prevention tools, attackers were experimenting with new formats for their malicious content, embedding images that contain malicious code in Microsoft OneNote or password-locked compressed-file formats. In one case, attackers sent a PDF document with a blurry, unreadable thumbnail of an “invoice”. The download button actually contained a link to a malicious website.
According to Christopher Budd, Director of X-Ops Research, Sophos, the cybersecurity firm releasing its 2023 findings: “The value of ‘data’ as currency has increased exponentially among cybercriminals, and this is particularly true for SMEs, which tend to use one service or software application, per function, for their entire operation. For example, let’s say attackers… steal credentials and then get hold of the password for the company’s accounting software. Attackers could then gain access to the targeted company’s financials and have the ability to funnel funds into their own accounts.”
* and incident response team data drawn from customers with up to 500 employees (defined as small- and medium-sized enterprises) when there was little or no managed detection and response protection in place
How cyberattackers personally called a potential victim to click on a malspam email to facilitate network penetration