A clocked Kermit-like hacker calledSubject X!
The recently disclosed phishing attacks on Twilio and Cloudflare employees had apparently resulted in 9,931 thousand accounts of over 130 IT-services organizations (114 USA firms or non-American firms with US-based employees) being compromised.
Now, investigations are revealing that the incidents were links in a chain—a simple yet effective single phishing campaign unprecedented in scale and reach that has been active since at least March 2022.
Codenamed ‘0ktapus’ by Group-IB researchers, the phishing campaign’s primary goal was to obtain Okta identity credentials and two-factor authentication codes from users of the targeted organizations. These users received text messages containing links to 169 unique phishing domains that mimicked the Okta authentication page of their organization.
It is still unknown how fraudsters prepared their target list and how they obtained the phone numbers. However, according to the compromised data analyzed by Group-IB, the threat actors started their attacks by targeting mobile operators and telecommunications companies and could have collected the numbers from those initial attacks. Also, clues from the phishing sites point to the use of a common phishing kit for their creation—one that researchers had not seen yet in the past.
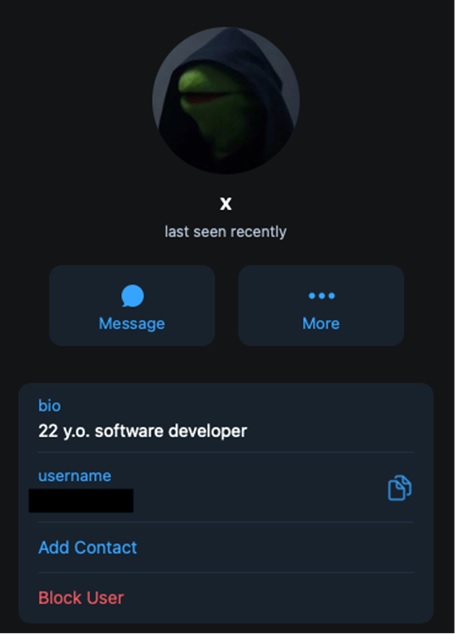
Further examination of the phishing kit’s code showed the lines dedicated to the configuration of the Telegram bot and the channel used by the attackers to drop compromised data. The Group-IB team was able to retrieve some details about one administrator of the Telegram channel in question who goes by the nickname “X”. Forensic data show that X is based in North Carolina.
According to Rustam Mirkasymov, Head of Cyber Threat Research, Group-IB Europe: “0ktapus shows how vulnerable modern organizations are to some basic social engineering attacks and how far-reaching the effects of such incidents can be for their partners and customers. By making our findings public we hope that more companies will be able to take preventive steps to protect their digital assets.”