In the cybercriminal domain, exploit authors are the first-line hackers to find or create vulnerabilities. Researchers sniff out their modus operandi.
Last year, an exploit broker was willing to pay up to US$2 million for zero-day jailbreaks of Apple’s iOS software, and US$1 million for zero-day exploits that take over WhatsApp and iMessage.
Zero-day vulnerabilities are the most valuable and prized asset: they are vulnerabilities for which no patch or update available until precious time has lapsed and damage perpetrated.
These vulnerabilities can take many forms, involving missing or flawed data encryption, SQL injection, buffer overflows, missing authorizations, broken algorithms, URL redirects, bugs, or problems with password security.
The focus of attention is usually on the malware that exploits the zero-day vulnerability, but in order for that malware to be developed and created, someone has to first find the vulnerability and work out how to exploit it. These specialists are the exploit authors, who usually work quietly out of the spotlight to discover and sell zero-day vulnerabilities to the highest bidder.
Check Point’s CSI ambitions
Just like crime-scene investigators, the Vulnerability and Malware research teams at Check Point wanted to probe into the workings of exploit authors and their motivations.
Starting from a single incident response case, they built a profile of one of the most active exploit developers for Windows, known as ‘Volodya’ or ‘BuggiCorp’. So far, they managed to track down more than 10 of the two’s Windows Kernel Local Privilege Escalation (LPE) exploits, many of which were zero-days at the time of development.
Their approach was to ‘fingerprint’ the authors’ working technique, looking for unique identifiers that could be associated with each individual. They did this by analyzing code and looking for characteristics such as the way that code was written and implemented. This is similar to how a graphologist analyzes handwriting.
During this research, the team focused on exploits that are used by or embedded in different malware families, both in advanced persistent threat (APT) attacks and in commoditized malware (especially ransomware). Although such threats are widespread, the researchers often found detailed malware reports that neglected to mention that the malware at hand also used exploits for escalating access privilege.
The team was able to use this technique repeatedly to track 16 Windows LPE exploits, written and sold by two different authors. Out of these, 15 date to the timeframe of 2015-2019, so it is plausible to assume that they constitute a significant share of the exploitation market, specifically for Windows LPE exploits.
Zero-day customers
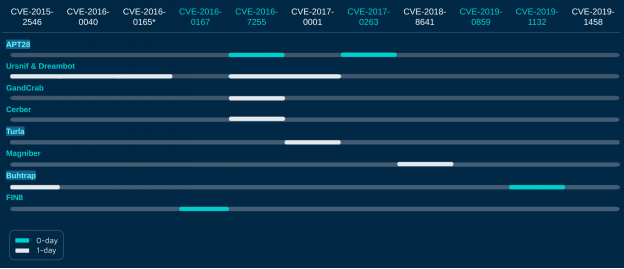
During the entire research process, the team wanted to focus on the two exploit authors and their clientele. The list of Volodya’s clients is diverse, and includes banker trojan authors such as Ursnif, ransomware authors such as GandCrab, Cerber and Magniber, and APT groups such as Turla, APT28 and Buhtrap.
The APT customers, Turla, APT28, and Buhtrap, are all commonly-linked to Russia. Even these advanced groups purchase exploits from exploit authors, instead of developing them in-house! This is another point that strengthens the team’s hypothesis that these zero-day exploits should be treated as a separate and distinct part of the construction of malware and the malware economy.
The following table summarizes and shows the CVEs that they were able to attribute to Volodya, as well as the customers or the malware groups found using these exploits. CVEs that are marked with blue are Zero-day, and naturally more expensive. The highlighted groups on the left are considered APTs.
The researchers have been able to fingerprint each exploit writer’s characteristic techniques, and then use these properties to identify and track two exploit authors, Volodya and PlayBit.
Based on these two successful test cases, the Check Point team believe that this research methodology can be used to identify additional exploit writers. Other researchers can perhaps try the suggested technique and adopt it as an additional tool in their arsenal.

















