Find out what OT organizations can do to clean up their act before a massive attack takes place.
In a recent study of the state of industrial cybersecurity, the main barriers inhibiting or delaying implementation of industrial cybersecurity initiatives have been uncovered.
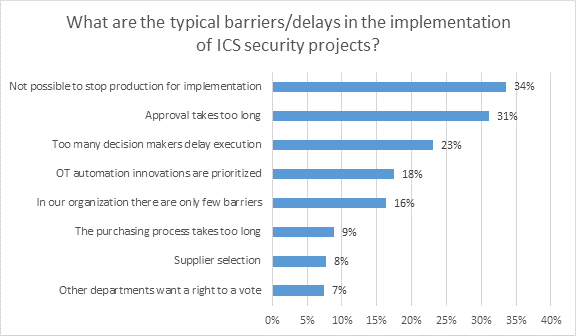
The most common obstacles cited included the inability to stop production (34%) and excessive bureaucracy such as lengthy approval processes (31%) and having too many decision-makers (23%).
These barriers may become a critical point in the years ahead because they can affect the implementation of pandemic-driven operational technology (OT) security initiatives.
Industrial control systems (ICS) are not exempt from the cybersecurity battle raging even harder in pandemic times. Industries have had to adapt and make sure their protection is keeping pace with malicious intentions in ICS networks.
Bureaucracy as a threat
The barriers cited by the study show when bureaucracy hampers actions to address cybersecurity, then it becomes a threat in itself. In total, almost half of organizations (46%) faced red tape delays. In addition to the most prevalent—long approval times and numerous decision-makers—these barriers included protracted supplier selection and purchasing processes, as well as interference from various functions in the organization.
These barriers may have become even more critical in the current period of relaxed or tapering lockdown measures. The survey revealed that almost half of the organizations (46%) polled expected to see changes in their OT security priorities as a result of the pandemic. These organizations will probably need to shift their security strategy on-the-fly and quickly implement new cybersecurity practices.
Due to the specific requirements of OT, the barriers for implementation can complicate and slow down the process of tightening cybersecurity even more. Some organizations (24%) citing decreased OT security budgets will face even more difficulties.
According to Georgy Shebuldaev, Head, Growth Center, Kaspersky: “It’s always more difficult to invest money and resources in projects without a clear return on investment, such as with cybersecurity initiatives. And while cybersecurity for OT is still a developing area, all these management barriers are quite natural.”
To eliminate these obstacles and simplify and speed up the implementation of protection measures, we need to make ROI figures more visible and showcase the risks for businesses so management boards can understand the benefits from the very beginning, said Shebuldaev. He offered the following tips:
- If an organization does not have enough experience and practice in complex ICS security projects, it is better to implement solutions step by step. Start with building organizational processes and adopting basic cybersecurity measures such as security gateways and endpoint protection.
Then, move to more complex projects such as network monitoring, intrusion prevention and security information and event management. Industrial standards such as ISO or IEC guidelines will organize the methods and increase the speed of project execution. - Introduce a practice whereby all new OT systems are implemented with cybersecurity built-in. This should simplify further protection processes and give the OT security team the ability to test new protection tools on these parts of the infrastructure.
- Enable education and training for all teams, including specific ICS security training for IT security and OT engineers and awareness to all employees. This will help different teams understand the risks and responsibilities of each other and increase the overall level of consciousness about cybersecurity.
When choosing a reliable cybersecurity solution for OT components and networks, as well as trusted partners for implementation, ensure dedicated protection for endpoints and network monitoring as well as ICS expert services and intelligence.
Such value-added services enable cybersecurity assessment, incident response and updated threat intelligence to help prioritize various detection and mitigation measures. These assessment and threat intelligence processes may be helpful in justifying protection projects to the Board.