Knowing thy enemy and his tactics, techniques and procedures can save thy data …
Imagine an attacker is lurking inside your network right now. Do you have the ability to find out and respond before they can cause harm?
Now imagine your adversary has privileged access to virtually every file and system in your IT environment and can impersonate any human, application or machine identity, at any time. Could you spot the attacker hiding in plain sight?
These are just some of the many questions security teams have been asking themselves in the wake of the massive SolarWinds digital supply chain vector that hit more than 18,000 organizations worldwide.
While details of the attack and its implications continue to surface, it is clear that the compromise of identity, and the manipulation of privileged access, were instrumental in the success of this attack.
There is much to be learned from examining the tactics, techniques and procedures (TTPs) used by the adversary. Researchers at CyberArk have deconstructed the attack so organizations can have a better understanding what they are up against and thereby prioritize prevention.
Three major attack stages
Why was Orion targeted? Because it is connected everywhere: from switches and routers, to firewalls, virtualization infrastructure, Active Directory, storage management tools and more. All of these connections rely on credentials, which in most cases are highly privileged. Simply put, Orion has its ‘hooks’ in all facets of an enterprise, making it the perfect “trusted” platform for an adversary.
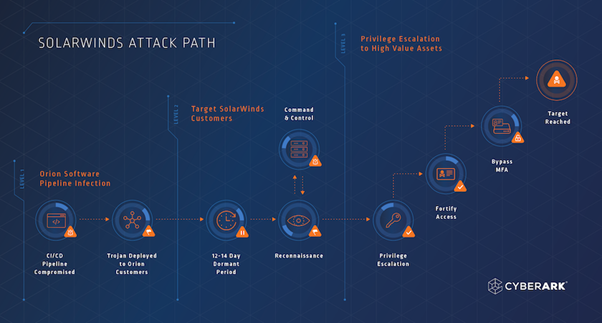
- Stage 1: Infect the CI/CD software pipeline
Forensic evidence reported in the press indicates the attackers had worked hard to learn the company’s code structure and terminology before launching the attack. Threat actors, especially well-resourced nation-state actors, will nearly always find a way to get inside. It is also why defenders must always adopt the defense-in-depth ‘assume breach’ motto.
To establish a foothold into the organization, the threat actor compromised the ‘heart’ of the CI/CD pipeline where code is tested, wrapped, containerized and signed, then successfully changed SolarWinode. The attackers used ‘SunSpot’ malware, which ran with high privileges, scanning for Orion builds.
With surgical precision—and without tipping off developers or engineers—the malware changed source file code names to deploy a backdoor. Following the build update, the backdoor code was deleted and the original file names were restored.
The actors had to silence warnings in the code and ensure the deployment of the malicious code was flawless. Making it seem as though they had never been there was no easy task.
These revelations have prompted many organizations to re-examine the security of their own CI/CD pipelines, and particularly, pipeline orchestrators and infrastructure managers, since these assets have extensive privileged access. These organizations are asking their supply chain vendors to do the same.
- Stage 2: Target SolarWinds customers
After two weeks of dormancy—an intentional pause that helped the attacker cover their tracks—the malicious payload started doing some reconnaissance and operation security checks. One of these was aimed at identifying hashes linked to specific endpoint security agents and forensics tools that could expose the running malware.
If an agent or tool on this ‘checklist’ was identified in the environment, the malware attempted to terminate the agents or suspend itself, if unsuccessful. However, if the malware did not find these specific hashes, or if it successfully terminated them, it moved to the next stage: calling home, dispatching commands from command & control servers, and disabling any vulnerable endpoint security agents.
Generally speaking the level of privilege a malware has upon initial infection can spell the difference between an infected endpoint and an entire network takeover. Enforcing the principle of least privilege across all endpoints can help prevent lateral movement, making it significantly harder for attackers to accomplish their goals. In the case of this digital supply chain attack, the malware already had elevated privileges when it reached each Orion customer organization.
Note, with the benefit of 20/20 hindsight, credential theft protection policies protecting Orion’s credentials database may have slowed the attack down by requiring the actor to use tools and techniques that increased the chance of exposure. But as it were, Orion’s privileged credentials were accessible to the attacker once inside, and almost certainly used in the next stage of the attack.
- Stage 3: Privilege escalation to high-value targets
Based on what has been reported, the threat actors most likely harvested credentials stored in Orion’s database, such as those traditional Tier0 assets like Active Directory, firewalls and infrastructure and networking management software. This would have enabled rapid escalation of privileges. With these powerful credentials in hand, the threat actors could have owned the targeted network right away.
Here is where it got interesting. The attackers began making moves to establish persistence, possessing sufficient privileges to not only add a backdoor account, but to also get an entire trusted tenant completely under their control. This provided continued access to the target network’s applications, services and data using the new trusted tenant accounts. Further, it eliminated the impact of any potential password changes by the organization and allowed the attacker to bypass multi-factor authentication completely. Doing this required a mix of sophisticated methods, and most notably, the Golden Security Assertion Markup Language (SAML) technique.
Using highly privileged credentials, the attackers successfully accessed and manipulated the victim organizations’ SAML token-signing certificate and forged digital SAML tokens that provide single sign-on access to virtually any system and application in the environment, both on-premises and in the cloud.
Since SAML token-signing certificates are almost never changed, the attacker could persist in the network for lengthy periods of time without fear of detection, and ultimately, achieve the intended goal. The Golden SAML technique highlights the fact that if the primary secret of the identity provider is compromised—for example, Active Directory Federation Services—then the threat actor ‘owns’ the source of truth and BECOMES their own identity provider. They can impersonate any user they want, no matter the user’s password, no matter the level of privilege and no matter if multifactor authentication is implemented.
Assume-a-breach mentality
The vast majority of all cyberattacks involve the compromise of identity and manipulation of privileged access. The SolarWinds breach was no exception.
As traditional network security barriers dissolve, the ‘assume breach’ mindset has never been more critical.
By assuming that any identity—whether human or machine—in your network may have been compromised, you can turn your attention to identifying, isolating and stopping threats from gaining privileged access and executing lateral movement to do harm.

















