Half of the money has been recovered, but the Florentine Banker group is still at large.
A wire transfer heist worth US$1.3m targeting three British private equity firms has been unravelled by security researchers.
A sophisticated cybercrime gang dubbed “The Florentine Banker” had for months focused on its targets, manipulating email correspondences, registering lookalike domains, and cashing immediately out in phases.
All in all, four separate bank transactions had attempted to transfer £1.1m (US$1.3m) to unrecognized bank accounts.
Emergency intervention by Check Point had enabled the recovery of only £570K (US$707,645). Check Point researchers also uncovered a number of purchased domains unrelated to the target mentioned, indicating that there are potentially more targets in cybercrime gang’s lineup.
What was their modus operandi?
After selecting a target, the Florentine Banker initiates its attack by setting up a targeted phishing campaign against key people inside the victim’s company, often CEOs and CFO in charge of money transactions.
In this case, the first phishing emails targeted only two personnel, of which one successfully stole credentials. The phishing attacks then continue, persisting for weeks in alternating methods, occasionally adding new individuals to the list of targets until the attackers gain a panoramic view of the entire financial picture of the company.
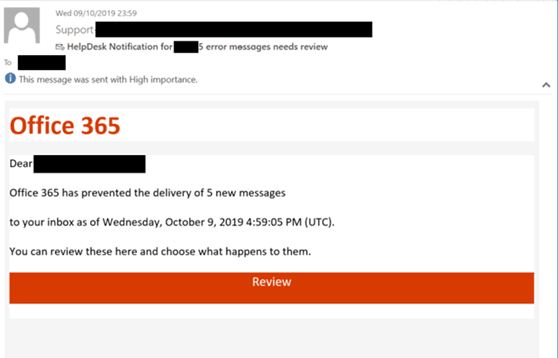
Check Point Research has profiled the steps of attack in five:
- Observation. Once the attackers gain control over an email account, they start reading the emails. The Florentine Banker can spend days, weeks or even months doing reconnaissance before actively intervening in the communication, patiently mapping the business scheme and procedures.
- Control and Isolation. The attackers start to isolate the victim from third parties and internal colleagues by creating malicious mailbox rules. These email rules divert any emails with filtered content or subjects into a folder monitored by the threat group, essentially creating a “Man in the Middle” attack.
- Lookalike setup. The attackers register lookalike domains—domains that look visually similar to the legitimate domains of the entities involved in the email. correspondences they want to intercept. The attacker starts sending emails from the lookalike domains. They either create a new conversation or continue an existing one —thus deceiving the target into presuming the source of the email is legitimate.
- Siphoning money. The attackers begin injecting fraudulent bank account information through the following two techniques: intercepting legitimate wire transfers and generating new wire transfer requests.
- Money transfer. The Florentine Banker manipulates the conversation until the third party approves the new banking details and confirms the transaction. If the bank rejects the transaction due to a mismatch in the account currency, beneficiary name or any other reason, the attackers are there to fix the rejects until the money is in their own hands.
Additional targets
In the case of the British private equity funds, a total of seven different domains were used by the attackers: either lookalike domains, or a website to serve the phishing pages. After closer examination, Check Point found 39 additional lookalike domains registered throughout 2018-2020, clearly trying to masquerade as a variety of legitimate businesses that may have been targeted by the Florentine Banker as well. Check Point Research is contacting these potential target organizations in order to prevent the next business email compromise (BEC) heist.
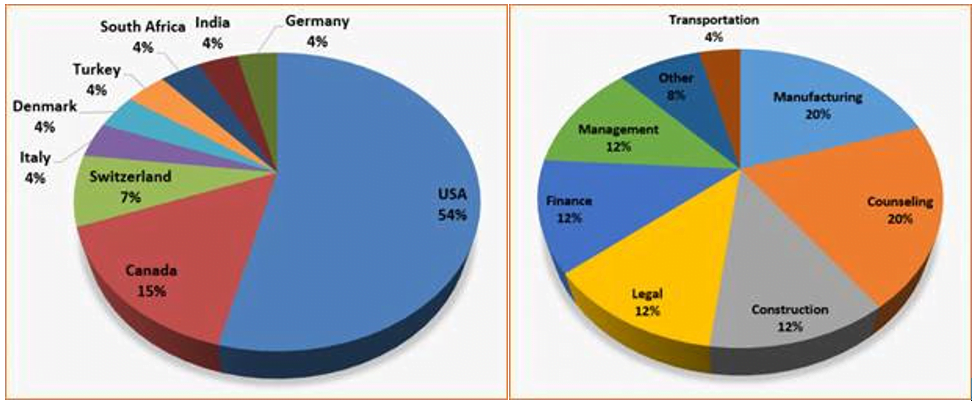
Here is a breakdown by country and industry of possible Florentine Banker targets, deduced from the lookalike domains researchers have uncovered:
Hacker background details
During Check Point’s investigation, it did not find definitive evidence to the origins of Florentine Banker, but they do have some clues that may indicate origin:
- Only conversations or transactions conducted in English were intercepted and modified.
- During the two months that the Florentine Banker group spent inside the victim’s environment, they operated Mondays through Fridays.
- Fraudulent bank accounts were located in Hong Kong and the United Kingdom.
- Several email threads in Hebrew included valuable leads that were not used by the attacker—which indicates the hackers do not speak Hebrew.
- A Hong Kon-based company name was used for the fraudulent money transfers in which the Florentine Banker group requested a wire transfer directly from the victim’s bank contact. It appears that this company was either fake or previously registered and it has since gone out of business.
Ways to protect against BEC
- Tighten email security. Emails are by far the number one vector for attackers to infiltrate business networks. Phishing emails baiting users to expose their organization credentials or to click on a malicious link/file are the number one threat in the email space. Organizations must always incorporate a continuously updated email security solution designed to prevent such attacks automatically.
- Educate your employees. Conduct proper and ongoing education of employees on vigilance against the evolving threat landscape.
- Tighten verification protocols. When dealing with wire transfers, always make sure to add a second verification by either calling the person who asked to make the transfer or calling the receiving party.
- Notify business partners. If a similar breach has been detected, make sure to notify all business partners as well—any delay in notification only works for the benefit of the attacker.

















