What the cyber defense world needs now is LOVE: Limiting Our Vulnerability Exposure!
A recently released threat intelligence report for 2021 has pointed to a 42% increase in new ransomware programs targeting known vulnerabilities, a surge so high that it is “shrinking the window that organizations have to remediate vulnerabilities ahead of an attack.”
The report’s data also indicated that Operational technology (OT) vulnerabilities had jumped 88% on year. Attacks on these critical infrastructural l assets can inflict severe economic damage and even endanger public health and safety.
Additionally, three other cyber trends were observed:
- There was a 24% rise in new vulnerabilities being exploited in the wild compared to the numbers in 2020. In other words, threat actors and malware developers were getting better at weaponizing recent vulnerabilities.
- Finally, a 75% increase in new cryptojacking malware was observed in the 2021 data, indicating that the malware industry was getting more adept at leveraging emerging business opportunities through collaborations and the distribution of ‘malware-as-a-service’ tools and services.
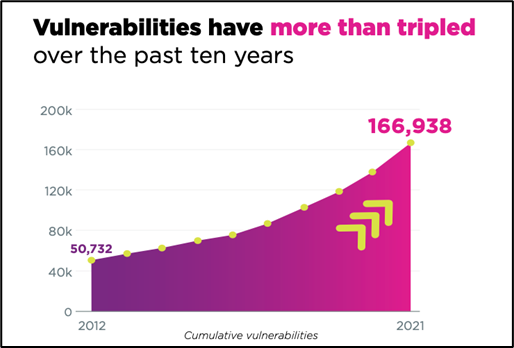
- Overall, the total number of vulnerabilities published over the last 10 years had reached 166,938 in 2021: a three-fold increase over a decade. As the US Cybersecurity and Infrastructure Security Agency (CISA) highlighted in its Top Routinely Exploited Vulnerabilities list, threat actors are routinely exploiting publicly disclosed vulnerabilities from years past. These cumulative vulnerabilities represent an enormous aggregate risk, and they have left organizations struggling with a mountain of ‘cybersecurity debt’.
According to Threat Intelligence Analyst Ran Abramson, Skybox Security Research Lab, which released the report: “The sheer volume of accumulated risks means (we cannot) possibly patch all of them. (Therefore) it is critical to prioritize (focus on) exposed vulnerabilities that could cause the most significant disruption, and then apply appropriate remediation options including configuration changes or network segmentation to eliminate risk, even before patches are applied or in cases where patches aren’t available.”
Abramson recommended standardizations on a common risk language for gauging risk in a rigorous scoring system that can be used to guide prioritization of remediation efforts.

















