Besides stealing passwords for payment services, Russia-linked groups have started going after gaming accounts in over 111 countries
First we have Ransomware-as-a-Service. Now the trend of democratizing cybercriminal activities has been extend to malware and info-stealing as a service!
34 Russian-speaking groups were recently identified as distributors of info-stealing malware using mainly Racoon and Redline stealers to obtain passwords for gaming accounts on Steam and Roblox; credentials for Amazon and PayPal, as well as those for users’ payment records and crypto wallet credentials.
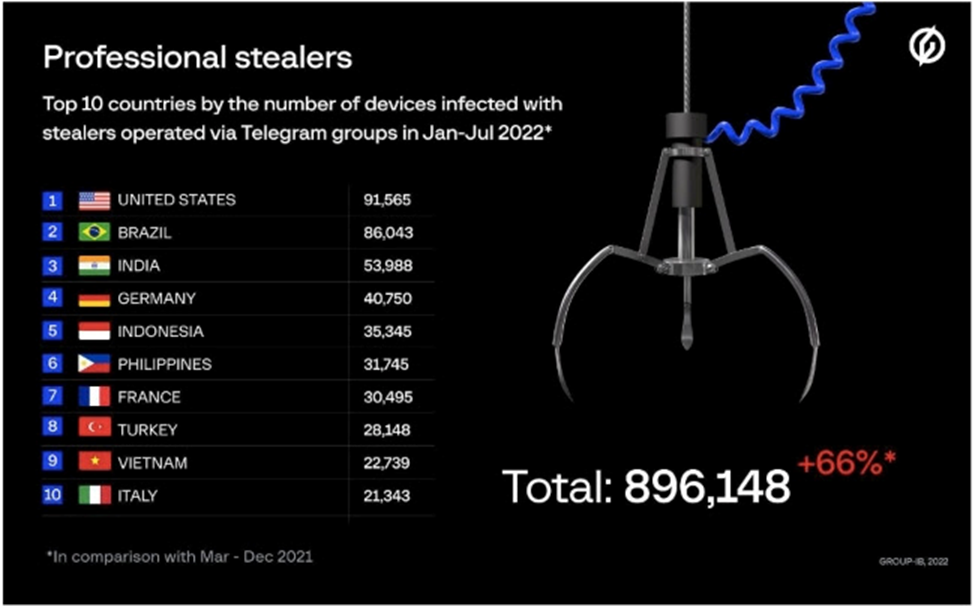
In the first seven months of 2022, the gangs collectively infected over 890,000 user devices and stole over 50m passwords. All the identified groups were orchestrating their attacks through Russian-language Telegram groups, although they mainly targeted users in the United States, Brazil, India, Germany, and Indonesia.
Graduates of Classiscam
According to Group-IB analysts, the infostealer gangs comprises low-rank online scammers who were dealing in the popular scam Classiscam scheme. Moreover, the illicit business of stealers, which is coordinated via Telegram groups, uses exactly the same operational model as Classiscam.
The mass Telegram groups and bots designed to distribute info stealers first appeared in early 2021. By investigating a number of accounts, Group-IB analysts were able to confirm that members of several scam groups that previously participated in the Classiscam scheme had begun using stealers. In 2021 and 2022, 34 active groups were identified on Telegram. On average, such info stealer distribution groups have around 200 active members. These cybercriminals embed links for downloading stealers into video reviews of popular games, into mining software or NFT files on specialized forums, and into ‘lucky draws’ and lotteries on social media.
The most popular stealer among the groups examined is RedLine, which is used by 23 out of 34 gangs. Racoon ranks second: eight groups employ this tool. Custom stealers are used in three communities. Administrators usually give workers both RedLine and Racoon in exchange for a share of the stolen data or money. However, the malware in question is offered for rent on the dark web for US$150–200 per month. Some groups use three stealers at the same time, while others have only one stealer in their arsenal.
Info stealers world tour
Group-IB estimates that between March 1 (when Group-IB started researching the scheme) and December 31, 2021 stealers operated via Telegram groups were able to compromise 538,000 devices. In the first 7 months of 2022, Telegram stealers were found to be almost twice more active infecting more than 890,000 devices in 111 countries.
The top five most often attacked countries in 2022 were the United States, Brazil, India, Germany and Indonesia. In the Asia Pacific region, the top ranked victims came from India (19,249 devices), Indonesia (35,345 devices), the Philippines (31,745 devices), Vietnam (22,739 devices), Australia (5,794 devices) and Singapore (2,179 devices).
In 2022, the most targeted services are the same as for 2021— namely PayPal (more than 16%) and Amazon (more than 13%). However, over the course of the 2022, cases of password theft for gaming services (Steam, EpicGames, Roblox) in the Group-IB ecosystem have increased almost five-fold. The underground market value of just the stolen logs and compromised card details is around US$5.8m, Group-IB experts estimate.
According to the firm’s head of Digital Risk Protection in the Asia Pacific region, Ilia Rozhnov: “The popularity of schemes involving stealers can be explained by the low entry barrier. Beginners do not need to have advanced technical knowledge as the process is fully automated and the only task is to create a file with a stealer in the Telegram bot and drive traffic to it. For victims whose computers become infected with a stealer, however, the consequences can be disastrous.”