Over the past three years, one global cybersecurity firm has seen IoT attack levels surge by double digits despite experts’ warnings
In a three-year analysis of data from its own user base and threat intelligence telemetry, a cybersecurity firm has noted a sharp increase in cyberattacks targeting IoT devices.
Also, in the first two months of 2023, almost every week, on average 54% of organizations in Check Point’s user base were targeted by IoT attack attempts, with an average of almost 60 attacks per organization per week targeting IoT devices — 41% higher than in 2022, and more than triple the number of attacks from two years ago.
IoT devices that were attacked range from a variety of routers, IP cameras, digital video recorders to network video recorders, printers and more. IoT devices such as speakers and IP cameras have become increasingly common in remote-working and learning environments, providing cybercriminals with a wealth of potential entry points.
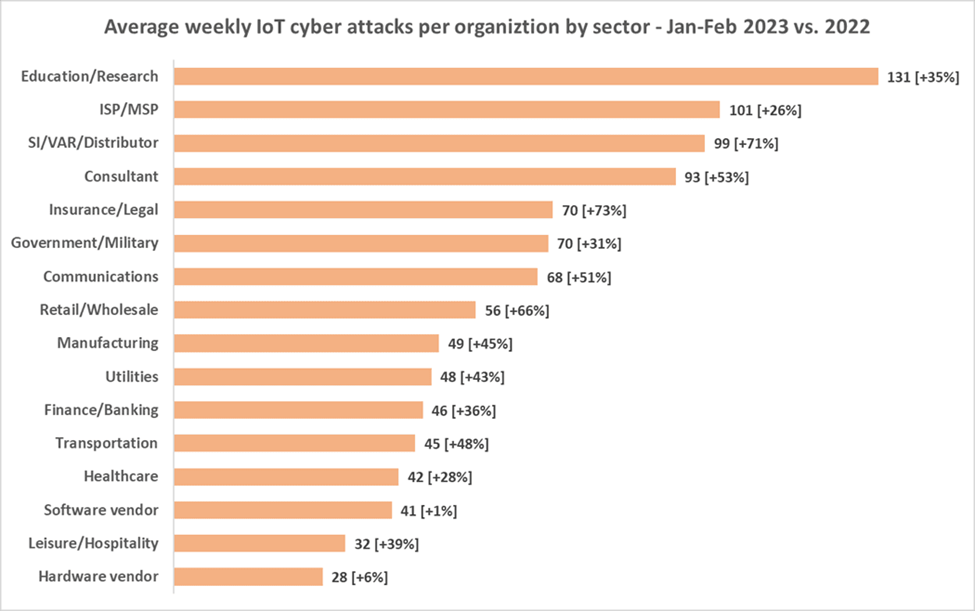
This trend was observed across all regions and sectors in the firm’s services. Europe was ranked as the worst-hit, with an average of almost 70 such attacks per organization every week, followed by the Asia Pacific region with 64; Latin America with 48, North America with 37 (and the largest increase from 2022, with 58%), and Africa with 34 weekly IoT cyberattacks per organization.
The data showed that the education and research sectors were facing an unprecedented surge in IoT attacks, with 131 weekly attacks per organization — more than twice the global average and a 34% increase from the previous year. Other sectors in the firm’s protection ecosystem were also witnessing a surge in attacks, with most sectors experiencing double-digit growth compared to 2022.
Top five IoT attack vectors
While the threat landscape for IoT vulnerability exploits contains hundreds of vulnerabilities, some are seen widely more than others in scanning and attack attempts against corporate networks. These are the top five exploits in the firm’s ecosystem (and weekly incidence rate) since the beginning of 2023:
- MVPower DVR Remote Code Execution: 49%
- Dasan GPON Router Authentication Bypass (CVE-2018-10561): 38%
- NETGEAR DGN Command Injection: 33%
- D-Link Multiple Products Remote Code Execution (CVE-2015-2051): 23%
- D-Link DSL-2750B Remote Command Execution: 14%
Abuse of vulnerability scanning tools
Vulnerability scanners are widely used to identify and exploit weaknesses in web applications and APIs, but cybercriminals can also employ them for malicious purposes. Two increasingly popular tools include Out-of-band security testing (OAST) and “Interact.sh”.
The process entails sending a simple payload to a large group, with vulnerable targets responding to the initial request, confirming their vulnerability. This method falls under active scanning, the first step in the MITRE Matrix for Enterprise—a hierarchical framework of attack tactics and techniques used by cybercriminals.
Scanning enables attackers to verify the vulnerability of their targets and ensure only they receive the actual malicious payload. During a one-week testing period, at least 3% of networks were affected by this scanning method. The top exploits employing this attack method in Check Point’s data include:
- NETGEAR DGN Command Injection
- Netgear R7000 and R6400 cgi-bin Command Injection (CVE-2016-6277)
- FLIR AX8 Thermal Camera Command Injection (CVE-2022-37061)
- Multiple IoT Command Injection